The 200 million Microsoft Office 365 (O365) users worldwide are now being targeted by a new global spear-phishing attack spoofing Microsoft.com. Two weeks ago, IRONSCALES researchers first identified what we can now confirm to be a well-coordinated email spoofing campaign targeting O365 users, particularly within the financial services, healthcare, insurance, manufacturing, utilities, and telecom industries, among others.
This spear-phishing campaign is putting companies at high risk since even the savviest employees - those who know how to check sender addresses - are likely to perceive the message as legitimate.
To date, almost 100 IRONSCALES customers with a combined total of a few thousand mailboxes have been targeted by this email spoofing attack. Today’s news comes just a few weeks after our research team uncovered that nearly 50% of phishing emulations bypass Office 365 Advanced Threat Protection (ATP).
Details about how Office 365 didn’t stop the email spoofing attack
The attack deploys an exact domain spoofing technique, which occurs when an email is sent from a fraudulent domain that is an exact match to the spoofed brand’s domain. In this spoof, the attackers devised a realistic-looking email from sender “Microsoft Outlook,” attempting to compel users to take advantage of a relatively new 0365 capability that allows for “reclaiming emails that have been accidentally marked as phishing or spam messages.”
Specifically, the fraudulent message is composed of urgent and somewhat fear-inducing language intended to convince users to click on what is a malicious link without hesitation. As inferred by the message, the link will redirect users to a secure portal in which they can review and take action on “quarantined messages” captured by the Exchange Online Protection (EOP) filtering stack, the new feature that has only been available since September.
-1.png?width=762&name=microsoft-spoof-1%20(1)-1.png) Once the link is clicked, users are asked to input their legitimate O365 login credentials on a fake login page, mistakenly believing that they are providing their private information to Microsoft online. Unbeknown to them, attackers are harvesting these credentials (usernames and passwords), most often to illegally obtain proprietary or confidential information, enact financial fraud, or sell online. Just last week, it was discovered that O365 login credentials of executives are selling for thousands of dollars per record on the Dark Web.
Once the link is clicked, users are asked to input their legitimate O365 login credentials on a fake login page, mistakenly believing that they are providing their private information to Microsoft online. Unbeknown to them, attackers are harvesting these credentials (usernames and passwords), most often to illegally obtain proprietary or confidential information, enact financial fraud, or sell online. Just last week, it was discovered that O365 login credentials of executives are selling for thousands of dollars per record on the Dark Web.
DMARC and Exact domain spoofs
What’s interesting about this campaign is that exact domain spoofs aren’t incredibly sophisticated attacks for gateway controls to detect. In fact, previous IRONSCALES research revealed that exact domain spoofs represent less than 1% of total email spoofing attacks that bypass secure email gateways (SEGs) in a given year. Even non-cloud-native and legacy email security tools are fairly efficient at stopping these sorts of attacks.
The reason why SEGs can traditionally stop exact domain spoofing is that, when configured correctly, this control is compliant with the domain-based message authentication, reporting & conformance (DMARC), an email authentication protocol built specifically to stop exact domain spoofing (SPF/DKIM).
As evident in the screenshot below, the attack appears to come from <no-reply@microsoft.com>, yet it failed its SPF result, nevertheless.
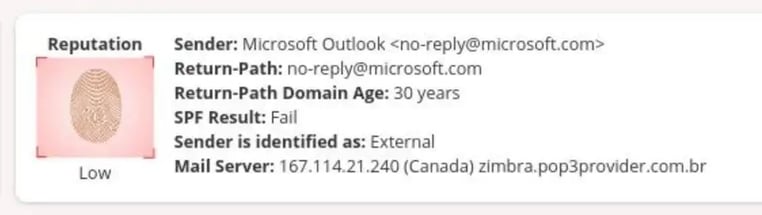 So then, why was the message allowed to bypass the gateway and land in the inbox?
So then, why was the message allowed to bypass the gateway and land in the inbox?
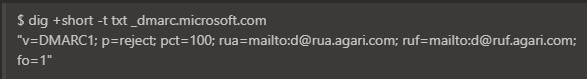
Any other email service that respects and enforces DMARC would have allowed Office 365 to stop email spoofing such emails. It remains unknown as to why Microsoft is allowing a spoof of their very own domain against their own email infrastructure.
Mitigating phishing risk by defending the mailbox-level
While exact sender name impersonations and domain name impersonation are technically more complicated, exact domain spoofing remains a common spear-phishing technique that even hyper-aware workers can overlook.
To the naked eye, the most suspicious element of this attack would be the sense of urgency to view the quarantined messages or the unusualness of receiving this type of email solicitation.
To mitigate risk, companies should ensure that their defenses are configured for DMARC. We’ve written extensively about how DMARC gets more credit than it actually deserves, but in this instance, the protocol can be helpful. In addition, advanced mailbox-level email security that continuously studies every employee's inbox to detect anomalies based on both email data and metadata extracted from previously trusted communications can help stop email spoofs that slip through the cracks.
To learn more about IRONSCALES’ award-winning anti-phishing solution, please sign up for a demo today at https://ironscales.com/get-a-demo/.

December 7, 2020