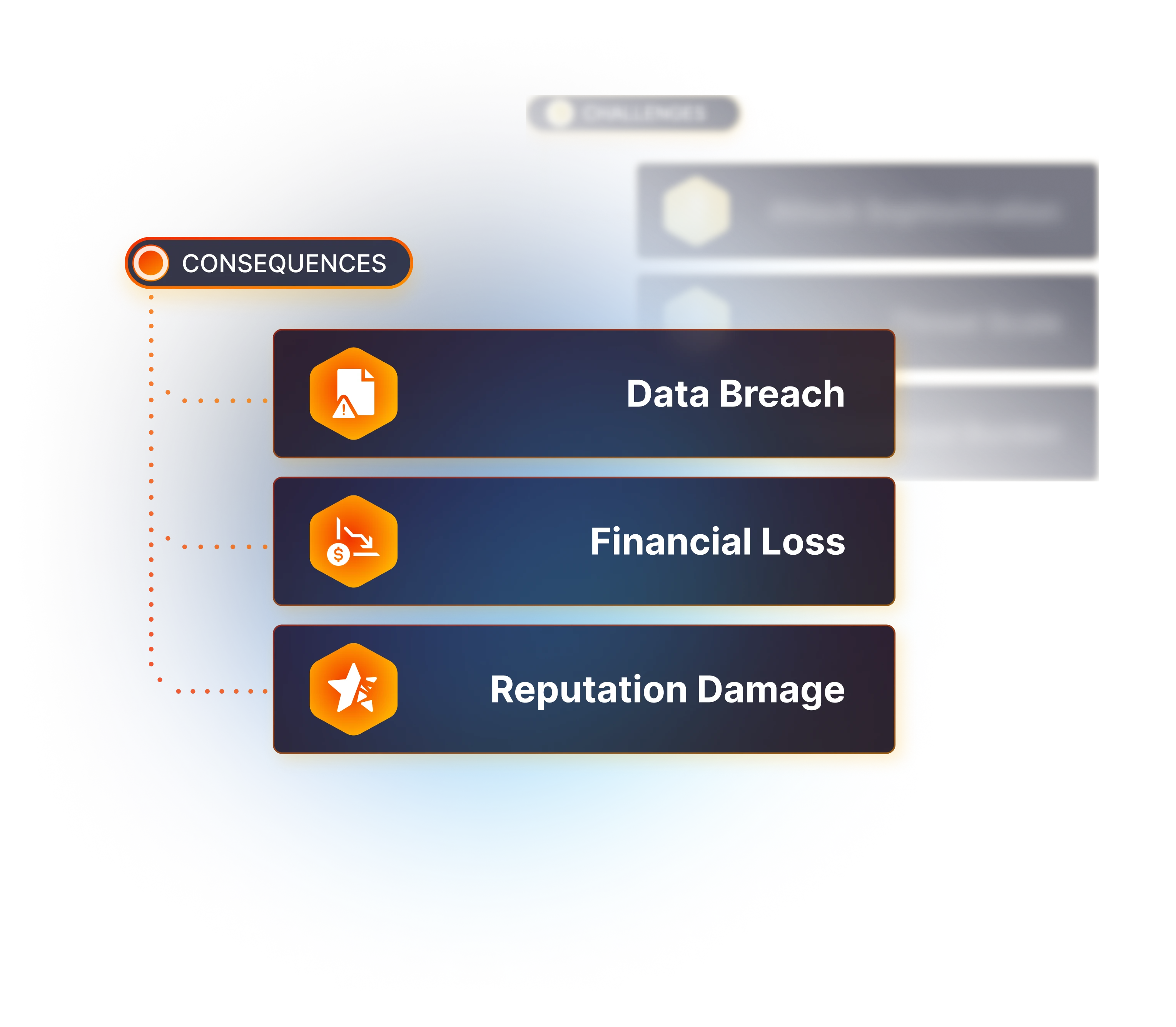
BEC Consequences
Business Email Compromise attacks strike at the heart of your organization, carrying severe implications:
- Financial Fallout—BEC schemes often result in direct monetary loss through fraudulent financial transactions, substantial enough to destabilize business operations.
- Data Exposure—These sophisticated attacks can expose sensitive customer information or proprietary business data to unauthorized entities.
- Reputational Damage—The trust your business has built can quickly erode following a BEC incident, impacting customer confidence and your brand image.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







/solution_bec_detection_2x.webp?width=2135&height=1495&name=solution_bec_detection_2x.webp)
/solution_bec_detection_2x.webp)
/simplify_operations_generic_.webp)
/Triangle-protect.webp)
/Triangle-simplify.webp)
/Triangle-Empower.webp)
