Table of Contents
Security Terms Explained: A Primer on Polymorphism
During a recent client presentation, a member of our sales team (no doubt caught up in the excitement common to security professionals) used the term “polymorphism.” The client, who was unfamiliar with the term, could only sit in confusion until the sales rep took a breath. The resulting interaction quickly taught us two things: 1. Be mindful of using jargon and overly technical terminology in client discussions (a.k.a., know your audience), and 2. Take the appropriate opportunities to familiarize your audience with new and emerging terms, attack methods, and defensive strategies.
Derived from the Greek "poly" (many) and "morphe" (form), polymorphism is used in biology to describe variations within a given species of animal. In cybersecurity, however, polymorphic simply describes different variations of the same basic attack. For example, every attack has a payload, or a means to deliver malicious data. These can come in any number of forms: text message, email, image, executable files, etc. Every attack payload has some form of identifiable information—origin, sender, even the literal content being delivered—embedded right in the payload.
And though they have existed for a few decades, over the past several years polymorphic attacks have swelled in volume and capacity for damage. In fact, according to Webroot, more than 94 percent of malicious executables involve polymorphic malware.
Why email is such an effective courier of attacks
Email is commonly and benignly used as a payload to deliver data. Every email has metadata (a set of data about data) associated with it, such as the From / To fields, a return path parameter, the subject line, and so on.
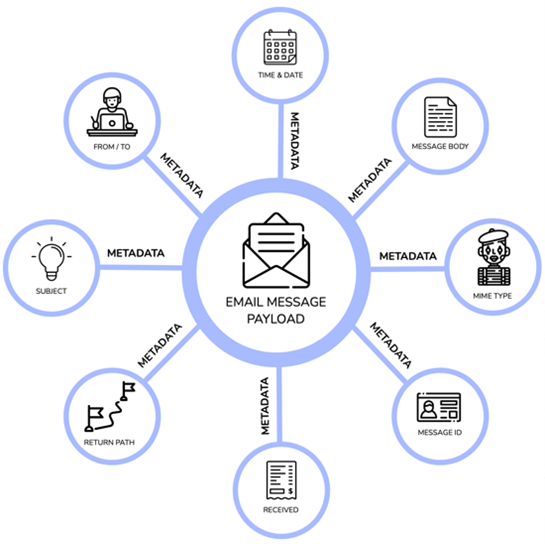
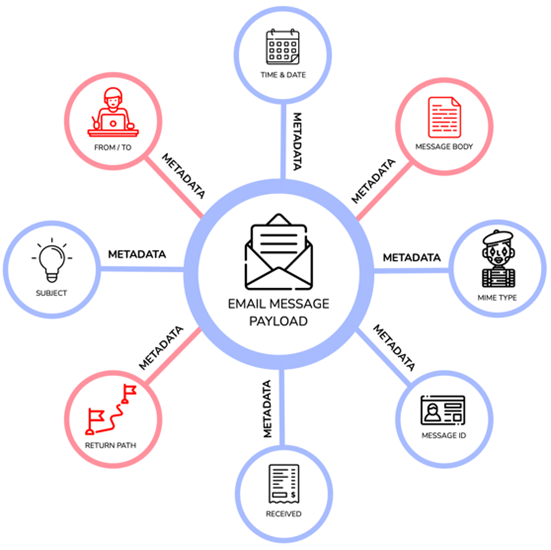
Historically, attackers take a normal email message, modify some aspects of the metadata, and send it to a potential victim. Traditional security tools first require a method to find the compromised email, after which the modified metadata must be identified, followed by writing a rule to describe that metadata, and only then will the tool start filtering based on that rule. This approach is problematic.
First, someone must investigate and analyze the email, assess what was changed, determine how to write the necessary rule, and define that rule in their security tool. This process takes a significant amount of time, which is no longer realistic in today’s fast-moving world.
Today, attackers can easily take advantage of organizations because they exploit the delay between the time their email is sent, and the time action is taken against it. They do this by developing and implementing automation tools to generate “many forms” of a given attack. In other words, attackers create a huge number of subtle variations of the same basic attack—a polymorphic attack—and overwhelm organizations with the speed and volume of one attack type or another.
The value of a thorough and candid analyst
At IRONSCALES, our goal is to stop the attackers before they can damage your business. We strive to arm your teams with the latest knowledge, tools, and education to make that a reality. This was the impetus behind the development of our algorithm, Themis.
Named for the Greek goddess of good counsel, Themis will review the historical mail in your environment, amassing deep knowledge about your users, how they are organized, who they interact with, and how/when they communicate. Next, Themis will examine every message your organization receives. She will analyze the metadata for those messages and then go even deeper, seeking any variations in your team’s communication patterns. For example, is it normal for your CEO to engage with a purchaser who is several levels down on the organizational structure? Would it make sense if your CFO suddenly began using words incorrectly and ignoring basic grammar? The answers will depend on the organization, the relationships, and the individuals—and only after deep analysis will they be revealed.
Following that analysis, Themis will rate each message. If a given message is rated beyond a set threshold, she will immediately quarantine it, summarize her findings, alert the security operations team, and ask them to make a final determination. Once that’s been done, Themis gets stronger and smarter. She applies this newly gained knowledge to every company she protects, instantly. Armed with this information, security teams can stop searching and start deciding where attacks are coming from, who is being targeted, and how best to direct their resources.
The bottom line is simple: Attackers using polymorphic attacks in huge volumes can now be stopped thanks to this technology that analyzes messages in totality and within the context of how your team communicates. Learn more about Themis, then request a demo.
1 https://www-cdn.webroot.com/9315/2354/6488/2018-Webroot-Threat-Report_US-ONLINE.pdf
2 https://cybersecurityventures.com/the-devastating-effect-of-polymorphic-malware/
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)





.png)