As we approach the end of 2019 and the culmination of a chaotic decade for phishing attacks, it’s time we begin to look forward to the email security industry challenges and opportunities that lie ahead.
Last year, we made email security projections for 2019, which included:
- Email flooding attacks would return with a vengeance
- Buyers would force the industry to define automation
- Companies would begin to rethink social media policies
- Artificial intelligence would become a SOC’s best friend
While the return to email flooding hasn’t been as quick as we believed, the other three projections have begun to come true. As recently reported by the Wall Street Journal article entitled ‘Business Use AI to Thwart Hackers,’ organizations are “racing to improve products and services with artificial intelligence, the Internet of Things and other emerging technologies.”
Additionally, while we aren’t quite sure how many companies have updated their social media policies to reflect how oversharing on social media is increasing risk, the topic of oversharing and its connection to phishing has been proliferating in the news. According to an article in SecurityInfoWatch, “employees who are unaware of the risks associated with oversharing on social media can endanger the company’s intellectual property, reputation, clients, and fellow employees.”
So, what are some of the anti-phishing and email security narratives for 2020 and beyond. Here’s what we think is most likely to occur:
Native, built-in security takes a backseat
The Federal Bureau of Investigation recently reported that business email compromise (BEC) attacks have cost organizations around the world nearly $26 billion in the past three years. Other reports are stating that cybercrime will top nearly $6 trillion by 2021. With these numbers in mind, organizations heading into 2020 are beginning to realize that native cloud email security, such as the security that is built-in to Microsoft Office 365 and Gmail, is no longer sufficient against today’s, and tomorrow’s, advanced cyberattacks; 90% of which begin with email phishing. Microsoft ATP, for example, has proven slow-moving against attacks, taking up to 250 days for a signature to be deployed once an attack is identified.
Not to mention the solutions’ inability to identify file-less based attacks akin to the challenges inherent to secure email gateway. In a threat landscape where a phishing attack takes less that 82 seconds to be clicked on, the time from threat identification to attack response is of the essence.
As we head into the next decade, organizations will finally embrace human controls and technological controls working together to decentralize threat intelligence, automate rapid response and encourage employee collaboration. For this is the only way to shrink an attackers’ advantage to a much more manageable level.
MSPs, MSSPs and MDRs bolster email security
As the risk of falling victim to a cyberattack becomes more of a reality, businesses of all sizes are now looking towards managed services to formulate strategic partnerships in the next decade that can help reduce cyber risk. In fact, the cyber threat landscape has shifted so much that Market Research Future expects the managed services market to grow 11% by 2022.
The irony here is that the explosive growth of the channel market is now elevating the attack profile of service providers themselves, which we predict will continue if risks aren’t mitigated.
Often lower risk and less time intensive to execute with potentially higher reward, one successful MSP attack could expose proprietary data from dozens of companies at once while also serving as a gateway into the various networks and cloud apps associated with each MSP customer. And since email continues to be the main vector for cyberattacks, the channel must prioritize an email security strategy that protects not only their customers, but themselves. Otherwise, we expect that MSPs will constantly be on edge for the next attack that might disrupt not only its customers but its internal operations as well.
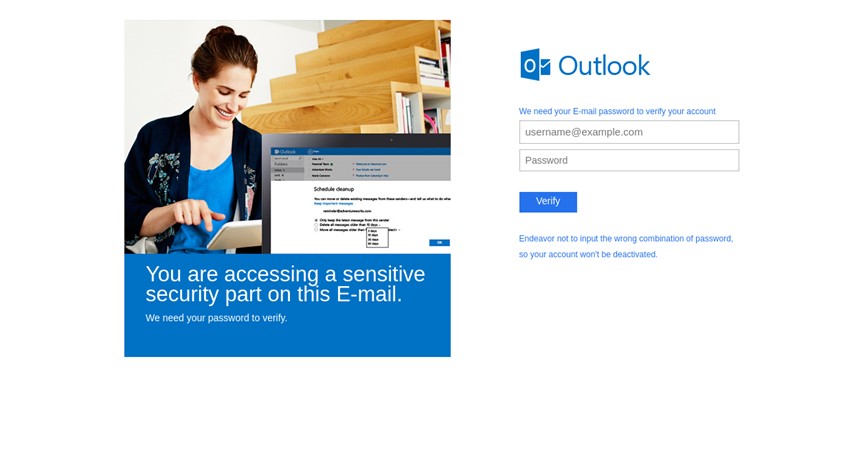
Fake login pages will continue to fool even the best of us
In today’s threat landscape, attackers are constantly looking for techniques to bypass traditional email security tools, and other protocols in order for a malicious email to land in an inbox. Recently, research has shown the rising popularity of credential theft attacks which tricks victims into providing login information through a fake login page that is nearly identical to the original.
The key to this attack is that traditional protocols are unable to identify the URLS as malicious as they contain no malicious code and the URLs are legit and unknown to any malware scanners due to their short lifespan and ease of recreation - making it easier for these malicious emails to land in an inbox, and more likely for a target to fall victim due to their uncanny visual similarity to known brands and websites.
Unfortunately, this attack is proving so successful it will continue into 2020 if email security tools don't evolve from only signature-based gateway-level technologies.
Polymorphism to remain a thorn in SOC teams’ sides -
The cybersecurity industry is knowingly suffering from a workforce shortage. Combine this with the fact that 65% of stressed out IT workers think about quitting their jobs and the cybersecurity industry is in real trouble. To make matters worse, phishing attacks continue to cost more in time, money, and effort as advanced attacks bypass traditional email solutions and protocols. This places an undue burden on SOC and security teams who are still manually removing malicious emails from inboxes and writing scripts and rules to prevent one attack from happening again.
Unfortunately, attackers are exploiting this burden through polymorphic emails, where an attacker implements slight but significant and often random changes to an emails’ artifacts, such as its content, copy, subject line, sender name or template in conjunction with or after an initial attack has deployed. This attack has proven to be so successful since it is time-consuming and burdensome for SOC teams to prevent. In fact, research has shown that 42% of email phishing attacks are polymorphic.
As we head into 2020, we predict the burden on SOC teams and fall-out from a stressed-out workforce will occur more if the cybersecurity industry doesn’t adopt AI and machine learning to reduce and automate repetitive and mundane tasks that machines can do. To do so, the industry need to embrace AI and ML by working together 24/7/365 to defeat attacks going into 2020 and beyond.
Regardless of the phishing threats and techniques trending in 2020 and beyond, IRONSCALES’ self-learning email security platform is proven to reduce risk by alleviating SOC team burden through threat intelligence sharing and reducing the time from threat identification to attack remediation from days to just seconds.
From all of us at IRONSCALES, we with you a phish-free holiday season and business email compromise-less New Year!
P.S. - Check out our new case study to learn how we helped a midsized PR agency dramatically reduce email phishing risk.

December 30, 2019