In April [2018], the UK’s National Cyber Security Centre (NCSC) published its Active Cyber Defence (ACD) Programme which urged companies to employ the Domain-based message authentication, reporting and conformance protocol (DMARC) to block fake emails spoofed to appear as if they have been sent by a government department.
HM Revenue and Customers (HMRC) is one brand that has been plagued by scammers abusing its authoritative position to spoof consumers into disclosing sensitive information. In an effort to stamp out this practice, it has invested significantly in various cybersecurity efforts, including implementing DMARC. It took part in ACD’s 2016 pilot and claims to have blocked over 300 million malicious or fraudulent emails. But it’s not stopped all of them and continues to find its brand spoofed by criminals to target victims and exploit cash. Which?, the largest independent consumer body in the UK, confirmed it had received reports from consumers this month [April 2018] who had been sent communications, purporting to be from HMRC, threatening legal action from unpaid taxes.
Phishing emails mimicking HMRC are often circulating and key dates will often see an uptick in activity. For example, around the end of the tax year in early April, end of May when P60 documents are typically issued, in July when final payments for settlement agreements are due, and again towards the end of the year when self-assessments need to be filed.
Let’s take a look at why, despite its promise, DMARC hasn’t stopped criminals mimicking HMRC.
What is DMARC?
It has been well documented that spoofing and impersonation techniques are becoming increasingly sophisticated, making their authenticity difficult to distinguish. To understand why DMARC fails to stop these spoofed messages, we need to understand what it is and where it’s weaknesses lie.
Initially launched in 2012, DMARC claims to help email domain owners control how their email is processed, which in principle should make it harder for criminals to spoof messages to appear as if they have come from a trusted address. It is built on the Domain Keys Identified Mail (DKIM) and Sender Policy Framework (SPF) and is meant to prevent senders (i.e. criminals) using a different sender address than the one actually being used. When an email fails this test, the spoofed domain owner (i.e. HMRC, etc.) will receive a report to alert them to someone trying to spoof their brand, hence the claim of millions of spoofed messages having been blocked. The problem is it doesn’t tell HMRC when attackers dupe the system and allow the spoofed messages through.
Another challenge is that phishers aren’t ones to give up easily and, in fact, it’s been widely reported that they’ve found a way around DMARC. Mailspoit is a phishing method that can exploit how email gateways handle text data differently than operating systems. We’ve detailed more on this, and other DMARC challenges and vulnerabilities, in a previous blog so feel free to take a read of that to find out more.
While DMARC can be effective in filtering out and reducing the number of fraudulent emails that attempt to hit users’ inboxes, alone it is not enough.
Before we move on, I’d also like to mention a disappointment we at IRONSCALES recently experienced. We offer phishing awareness and training - IronSchool. Again, while there are benefits to running these programmes, we’re the first to admit that organizations cannot rely on this alone to solve their phishing challenges. However, for these mock phishing attacks to be as effective as possible, training emails must be as realistic as humanly practicable. So, you can imagine our disappointment to receive a ‘cease and desist’ communication from a government organization informing us that we must not use its brand in our training programme because of the false reports it receives as a result. If companies use mocked phishing messages, with brands substituted for similar but not quite exact logos etc., then there will be obvious indicators to the majority of recipients. For us, its akin to a person learning to drive a car in a simulator and then allowed to drive on public roads unsupervised – it’s not going to end well.
What Will End Spoofing?
I’m sorry if you’re looking for a magic cure – at this point there isn’t one that can 100% detect and prevent spoofed messages being delivered to a user’s inbox. But we’re working on that and, rest assured, if there’s a way to make it possible we’ll be the first to tell you about it! But there is a way to stop them clicking on it. In fact, there’s quite a lot you can do to protect users, stamp out spoofed messages and keep the enterprise safe.
We actually recommend you think about email security differently and instead of the focus being completely on preventing messages getting into mailboxes, we suggest taking a bottom-up approach and focusing efforts on the Mailbox. After all, that’s where the threat is either realized or quashed.
Using machine learning algorithms and deep scans in the mailbox itself, phishing attacks that make it through to a user’s inbox can be identified, flagged and even removed.
By examining user communications and meta data to establish a baseline, anomalies in communications are easily spotted and automatically flagged as suspicious, to help people make smarter and quick decisions regarding emails within the mailbox. This must be supported with a mechanism for employees that do spot something amiss in a message to report their findings via inmail alerts combined with the ability for the security team to remove confirmed malicious messages from mailboxes enterprise-wide. This stance not only gives employees the necessary intelligence to detect bogus messages, but helps all parties defend the organizations from the most prevalent attack vector
We help organizations to do this with IronSights, the first and only phishing detection technology that combines human intelligence with machine learning to detect anomalies and communication habits at the mailbox level. Instead of the user scanning the message to see if they can spot spoofing indicators, IronSights has already determined the authenticity of the message and made a judgement which it then visually flags for the user to review. While someone may miss subtleties within a message, a large red banner across the email that warns that the message has been deemed suspicious is hard to ignore.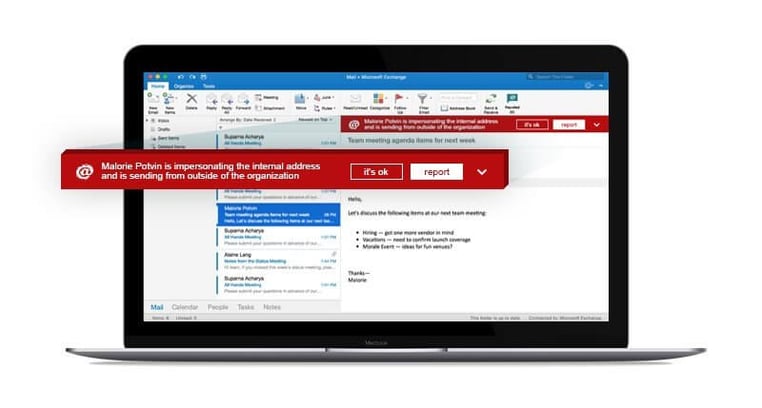
To compliment this, we offer IronTraps, the fastest, fully automated, phishing incident response. It can detect even advanced phishing threats automatically based on its analysis of multiple sources of intelligence - such as end user reports, internal and external verified attacks using proprietary and 3rd party multi anti-virus and sandbox engines. Once a phishing email is detected or reported, an immediate automated deep forensics scan is triggered, followed by an enterprise-wide remediation response which includes the removal of emails from other inboxes which significantly reduces the time malicious messages lie idle in employees’ inboxes. As messages are removed, it reduces the risk of another distracted or uneducated users interacting with the message, but also prevents reinfection from advanced threats – such as polymorphic attacks.
Test results have shown that in most cases it takes under 60 seconds for companies using IronTraps to report an attack, and just seconds for IronTraps to eliminate the threat entirely enterprise wide. This is compared to hours or days for competitive alternatives to eliminate the threat.
While DMARC will stop some spoofed messages, it’s not going to stop everything evading gateway detection, so let us take a look at your incoming mail and warn your users before they click on a link or open an attachment or wire a large sum of money.
Call us now to find out more and book a demonstration.

April 26, 2018