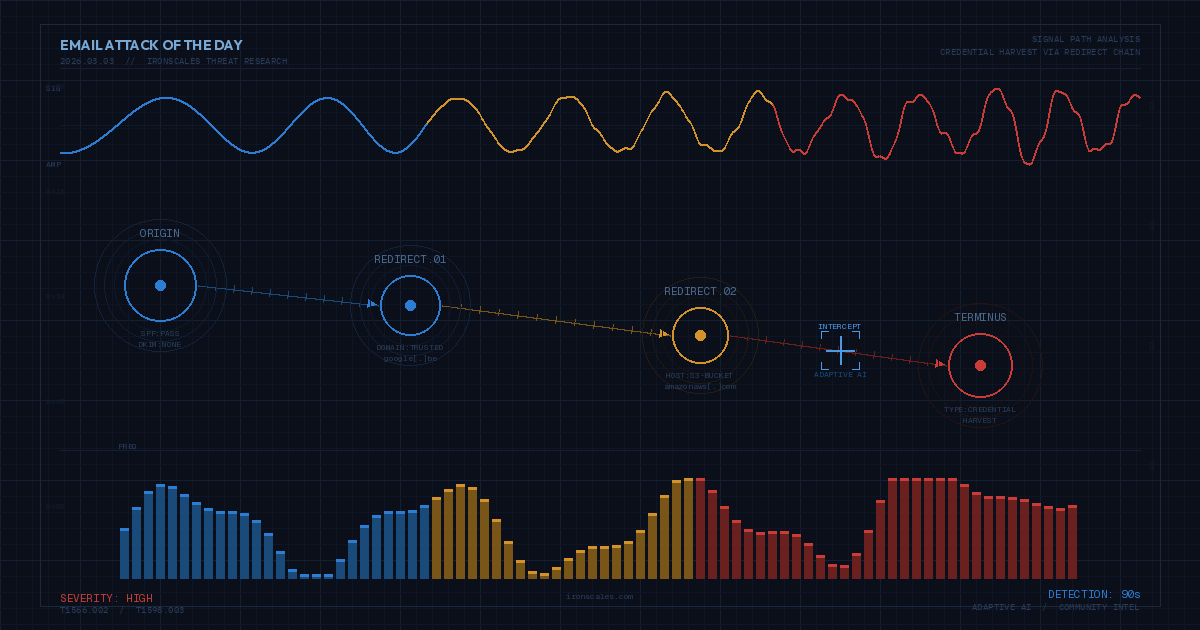
Table of Contents
A researcher at IRONSCALES recently discovered thousands of business email credentials stored on multiple web servers used by attackers to host spoofed Microsoft Office 365 login pages. The researcher found the credentials while investigating a new string of Vendor Impersonation phishing emails designed to execute Account Takeovers (ATO) and Business Email Compromise (BEC) attacks.
Vendor Impersonation Attacks Explained
Considered a form of business email compromise, Vendor Impersonation Attacks (also known as Vendor Email Compromise according to some definitions) are used to trick company finance departments into paying fake invoices, often to fake vendors or vendors they don’t even do business with. More sophisticated schemes are designed to intercept or redirect wire transfers to attackers.
The goal of vendor impersonation is to use the compromised account to defraud other companies or individuals or to launch Account Takeover (ATO) attacks. In this specific case, it appears that the attackers are trying to capture credentials to do both.
The Attack
Real estate-related transactions are often targeted for sophisticated fraud scams, especially transactions involving real estate title companies. This attack uses a vendor impersonation phishing email that appears to target people associated with real estate transactions including realtors, real estate lawyers, title agents, and buyers and sellers. The attack compromises the credentials of someone’s email account to either take control or monitor their email traffic and identify opportunities to exploit, like sending different wire instructions to intercept deposits, closing costs, or new mortgage pay outs.
This attack used emails to spoof two vendors in the real estate sector, First American Financial Corporation, and United Wholesale Mortgage. It’s possible that threat actors used information from a recent First American Financial breach in this attack. In 2019, it was discovered that First American had over 800 million documents containing personal information accessible to anyone with a web browser. The U.S. Securities and Exchange Commission fined First American $500k in 2021 for their mishandling of private information and a failure to respond to reports about the discovery.
The attackers sent their targets emails that used familiar subject lines and templates used by First American and United Wholesale Mortgage. The templates referred to either documents that needed to be reviewed or a new message hosted on a secure server—both of which have links that directed recipients to fake log-in pages requiring their Microsoft Office 365 email address and password. Each attempt to submit these O365 credentials returned an error and prompted the user to try again. Users will usually submit the same credentials at least one more time before they try variations of other passwords they might have used in the past, providing a gold mine of credentials for criminals to sell or use in brute force or credential stuffing attacks to access popular financial or social media accounts.
But wait, it gets worse. Our researcher noticed an unusual URL in the phishing emails that referred to a path that is normally used in a computer file directory (see image below). Exploring this directory uncovered clear text files containing every email address and password submitted to the fake O365 log in page. The fake webpage servers (and files) were quickly shut down or removed, but it’s likely the bad guys purchased the software they are using and will continue to make their stolen credentials available to the world. Even the bad guys forget to follow best practices.
A Closer Look at the Phish(es)
Here are the emails that recipients saw in their inbox:
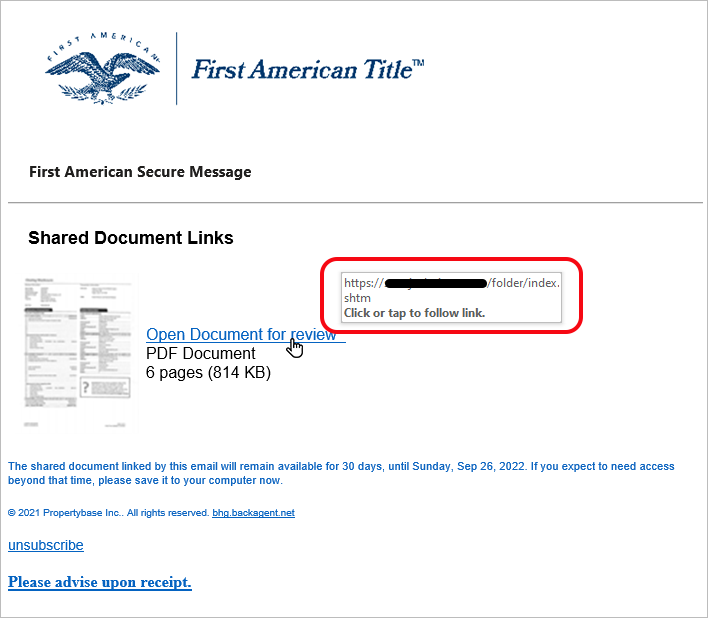
This appears to be a standard document review notification. Unlike most phishing emails, the URL displayed on mouse-over doesn’t even try to spoof a normal or familiar address. Instead, it displays, "https://phishingsite.com/folder/index.shtm", the actual URL of the phishing page.
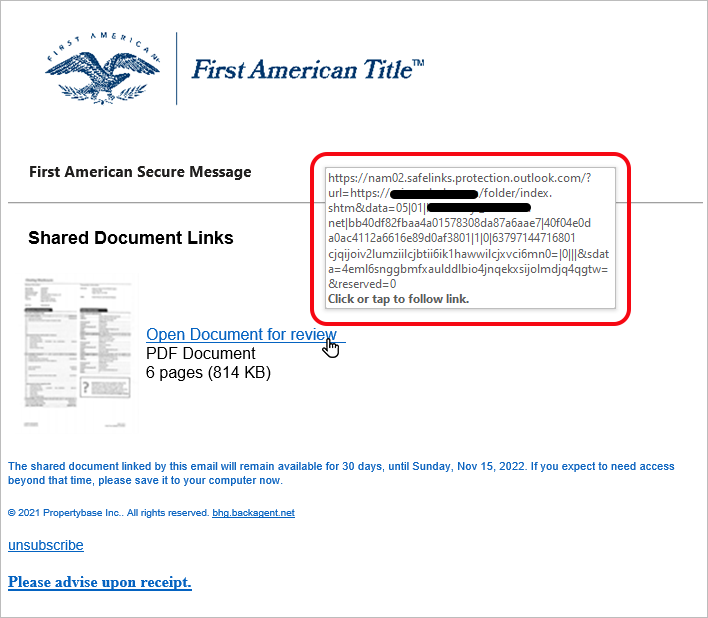
This email is from the same phishing attack, but the URL is now a Safe Link URL and the link still points to the original URL of the phishing site.
Safe links are a feature found in Microsoft Defender for Office 365. According to Microsoft, Safe Links provide URL scanning and rewriting of inbound email to help protect organizations from malicious links used in phishing and other attacks. It clearly didn’t work in this case. Worse though, is that it still rewrites the URL with a Safe link, making it harder to visually inspect the URL with a mouse over and generally gives users a false sense of security in their inbox.
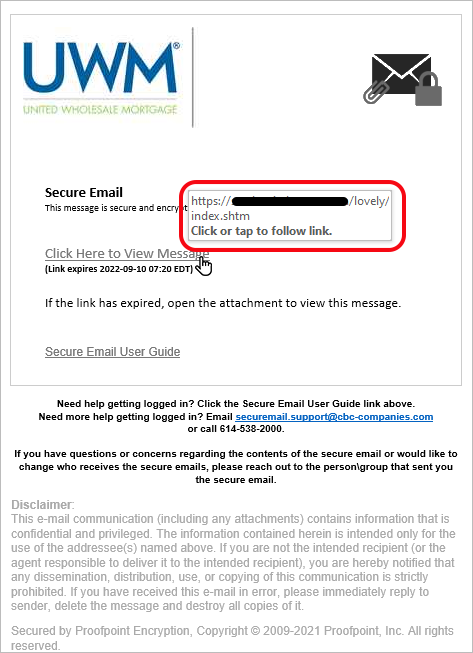
This email looks like a normal “Secure Email Notification” and it has the same conspicuous URL seen in the First American Title email - https://phishingsite.com/folder/index.shtm.
To make this email look a little more legitimate, the attackers included a confidentiality disclaimer and a “Secured by Proofpoint Encryption” signature.
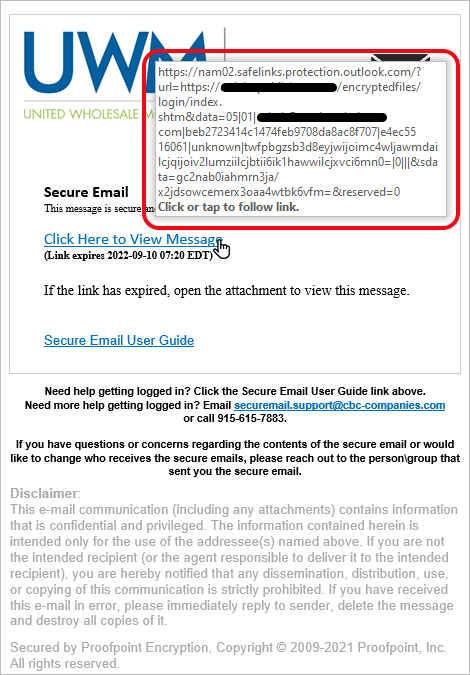
On this phishing attempt, the email is the same, but with the URL rewritten by Safe Link that still points to the original URL of the phishing site.
The Spoof
Here is a screen shot of the fake Microsoft O365 login page. As explained earlier, every attempt to log-in will results in an error message prompting the user to check their credentials and try again (and again, and again).
We’ve seen more sophisticated attacks that actually forward the user’s credentials to a legitimate O365 page and can then “proxy” the exchange a one-time SMS code (optional if an authenticator app is temporarily not available).

What Makes this Attack Work?
- Authentication - these emails will often slip right by most Secure Email Gateways (SEGS) and cloud email providers because the emails are coming from compromised, but valid, third-party servers that pass DKIM and SPF authentication checks. SEGS might catch these if the domain reputation is low, but not always.
- Social Engineering - the spoofed phishing messages are sent to people who are likely familiar with the vendor being spoofed, so they may not be as cautious about opening the email. Using a familiar message template can increases the likelihood of trust and a click, especially if they get a lot of these or are in a hurry.
- URL Rewriting - dangerous URLs that get re-written with a Microsoft Safe Link (or another security vendor) is just a free bonus for the bad guys.
How Did IRONSCALES Discover It?
IRONSCALES uses a combination of various AI and ML detection models. In this case, a new Semantic Analyzer Module (SAM) was quick to recognize this attack and stop it from reaching any IRONSCALES customers.
SAM is used to identify 24 classes of safe, spam, and phishing emails based on a combination of email content, subject, links, attachments, and sender information. Stay tuned for a future article that explains SAM in more detail and how it mimics the approach of a human analyst.
We invite you to download our new report "The Business Cost of Phishing", where you can discover the true cost of phishing on organizations as well as what IT and Security professionals believe is coming next. You can get the report at https://secure.ironscales.com/the-business-cost-of-phishing/report-download
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)