Table of Contents
Analysis of Microsoft O365 Credential Phishing with Employee Manual Updates
Attack Summary Details
- Impacted IRONSCALES customer mailboxes: 506
- Impacted IRONSCALES customers: 269
- Security Bypass: SPF, Visual Scanners
- Technique: Social Engineering, Malicious Payload, Spoof Phishing
Background
Credential phishing is one of the most common types of phishing attacks and it’s been on the rise in the past few years. According to a recent report on cybersecurity statistics, stolen credentials and compromised passwords were responsible for 61% of security and data breaches in 2022.
Cyber attackers never stop looking for new and innovative ways to access their victims' credentials, but sometimes they will combine two or more existing methods to catch their targets off-guard.
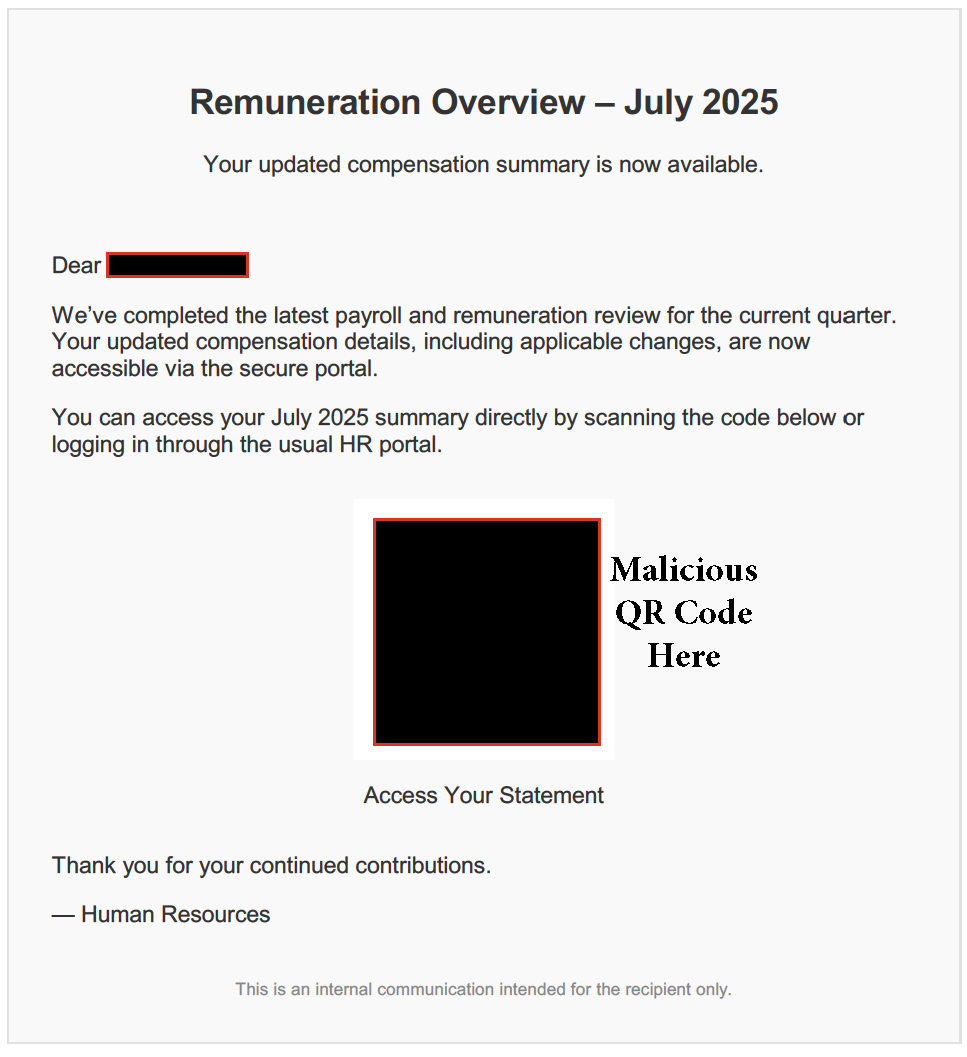
In this case, we are featuring a phishing campaign that uses a social engineering attack combined with a spoofed internal email address in the email header of messages to employees about updates to an employee manual. The message includes an attachment that appears to be a copy of the employee manual—opening the attachment prompts the victim to provide their Microsoft Office 365 password—leading to compromised credentials.
The Attack
The attack combines a phishing email and social engineering to facilitate credential theft.
The attacker sends an email with a display name that adds the recipient's employer name to “Help Desk.” For example, if the recipient worked at Google, the sender's display name will read as “Google Help Desk."
The body of the email message is designed to capture the victim's attention by referring to Employee Manual Updates and "other policy information" that can be found in an attachment. When the recipient opens the attachment, they are asked to verify their Microsoft O365 password. The attacker can now pair the victim's email address with the password they provided and do a lot of damage with those compromised credentials.
This attack occurred to more than 250 different companies, and the damage potential is huge! It just takes one employee's compromised credentials for an attacker to have access to the employee's email messages, Microsoft Team messages, company files, and their system. The attacker can then extort money from the company or the employee or execute credential attacks on other employees by sending email messages on behalf of the victim (emails that don't even have to be spoofed since the attacker has full access to the victim's account).
A Closer Look At The Phish
This is what most recipients will see in their inbox (the highlighted text is personalized for each attack):
From: ACME Help Desk <noreply@acme.com>
To: Joe Smith <jsmith@acme.com>
Subject: 21/12, Employee Manual
SMTP Server: a59-199.smtp-out.us-west-2.amazonses.com (54.240.59.199)
The ACME Employee Manual has been amended and is in effect as of 21/12. The manual and other policy information can be found in the attachment sent with this email.
Changes have been made to the following sections:
- Section 6: Complaint Procedure
- Section 8: Vacation, Sick leave, and other Time
- Section 9: Health and Medical Care Plan
- Section 10: 401k Plan
- Section 17: Working Hours
- Section 22: Cell Phone Use
- Section 23: Expense Reports, Automobile Expenses, Transitchek
Following sections have been newly added:
- Section 8: "Banked Vacation Time"
- Section 25: References
For any questions related to the ACME Employee Manual, please contact Management.
Тhаnk Үоu,
Payload
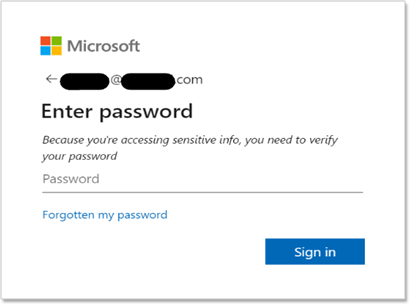
In the attachment of this email, there is an HTML file that leads to a phishing login page:
What makes this attack work?
The attackers are creative enough to spoof the display name of the sender and the company name in the email body to match the victim’s actual company name to make the email look like it really was sent from the company's help desk.
This kind of spoof will often make the recipient feel like it's safe to open the attachment. That level of trust is extended to the phishing log-in page that asks for the recipient to "verify your password." Further, challenging the recipient to prove their identity subtly implies that the sender is legitimate.
A critical element is the content. Referring to Employee Manual and Policy changes will get a lot of employees' attention and compel them to open the attachment because the subject matter could have direct and personal implications to the employee.
How did IRONSCALES discover it?
The IRONSCALES impersonation protection model recognized this attack as an impersonation attempt and alerted the recipient of this email that this is an impersonation attempt and automatically classified this email as phishing.
By classifying this incident as phishing, this type of email and similar emails will automatically be classified as phishing for everyone in the IRONSCALES community, and will not reach their mailbox.
To learn more about IRONSCALES’ fully integrated anti-phishing and security and awareness training solution, please sign up for a demo today at https://ironscales.com/get-a-demo/.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)