Table of Contents
As cyber attackers evolve, so do their methods (and their disguises). Lately, one of the emerging techniques used by these attackers is the use of images in the body of an email that appears to be text, which serves as a new bypass method to evade traditional language processing analysis for detection. To make matters worse, attackers are now incorporating QR codes into these image-based attacks, further complicating detection and blocking efforts. IRONSCALES data analysts have observed that between Q1 2023 and Q3 2023, there was a staggering 215% increase in these image-based phishing attacks. Our response? We are enhancing our ability to detect and defend against the spread of image-based and QR-code (quishing) email attacks. As part of our recently announced fall release, we’ve included improvements for deep image-based threat detection using a multi-modal approach.
Below are two examples of image-based phishing strategies that IRONSCALES captured recently. In the first example, the cyber attacker attempts to bypass language scanners by sending a phishing email that only includes an image but appears to be a legitimate invoice. The next thwarted threat shows an attacker's credential harvesting attempt through the use of a QR code. In both cases, IRONSCALES was able to automatically detect and remediate those threats.
Example 1: Image-based phishing email
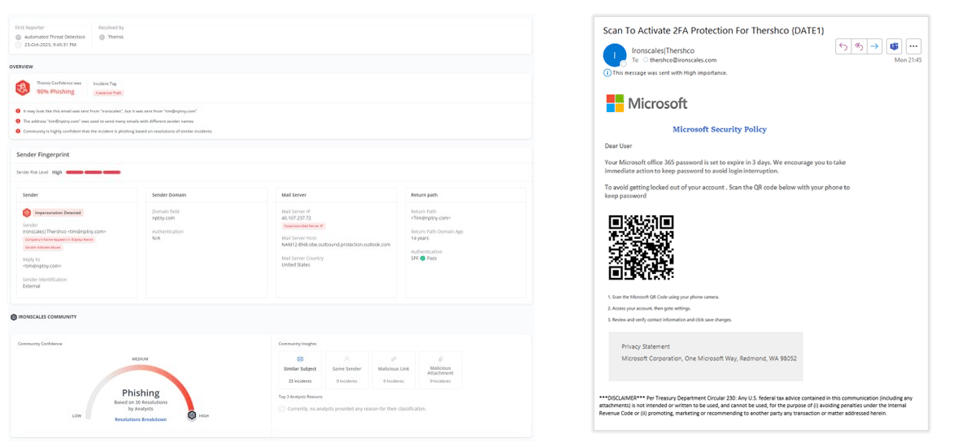
Example 2: QR code (Quishing) email discovered by IRONSCALES
In this blog post, we'll explore how you can defend your business against emerging quishing attacks using multi-modality.
Defending Against Quishing with Multi-Modal Protection
Our innovative multi-modal approach not only reads but also sees through image-based text attacks to safeguard your business from the growing threat of these attacks, including quishing attacks. By integrating Optical Character Recognition (OCR), deep-text and image processing, and natural language models, our solution ensures that nothing slips through the cracks.
OCR (Optical Character Recognition)
OCR technology allows our system to recognize text within images, even when it's hidden or obfuscated. This capability is crucial in identifying malicious intent from the text in the image as well as QR codes that may be concealing malicious content.
What is OCR? Optical Character Recognition (OCR) is a technology that converts printed or handwritten text within images into machine-readable text. In the context of our multi-modal protection system, OCR plays a crucial role in identifying and extracting text from images.
How OCR Works: OCR first identifies areas in an image where text is present. It does this by recognizing patterns, shapes, and variations in contrast that indicate the presence of text. Once text regions are identified, OCR algorithms analyze the pixels within these regions to convert the visual characters into digital text. This extracted text can then be processed further for analysis. OCR uses character recognition techniques to accurately interpret and convert the visual characters into machine-readable text. This ensures that even if the text is obfuscated or stylized, OCR can still decipher it.
Role in Phishing Defense: By converting the text within images into a machine-readable format, OCR enables further analysis to determine whether the content is legitimate or a phishing attempt.
Deep-Text Analysis
Deep-text analysis dives deep into the content of emails and attachments, examining not only the visible text but also the hidden content within images. It can uncover hidden phishing links or malicious instructions that traditional methods might overlook.What is Deep Text Analysis? Deep Text Analysis involves using advanced machine learning and natural language processing (NLP) techniques to analyze the content and context of textual information. It goes beyond simple keyword matching and delves into the semantics and meaning of text.
How Deep Text Analysis Works: Deep text analysis delves into language with NLP models that decipher text structure and meaning, tackling everything from grammar to sentiment. It grasps the intent of words and phrases by examining them in their sentence context. This nuanced analysis extends to scrutinizing the surrounding text for red flags or irregular patterns that could signal phishing. Moreover, it's adept at spotting the hallmarks of deceit—like misleading language or hidden URLs—thanks to machine learning models trained to detect and interpret such deceptive patterns.
Role in Quishing Defense: Deep text analysis is vital for scrutinizing the textual content within emails and attachments. It helps in uncovering hidden phishing links, malicious instructions, or social engineering tactics that attackers may use within the text of an email, even if they are concealed within images.
Image Processing
Our image processing component ensures that images, including QR codes, are thoroughly analyzed for any suspicious elements. This layer of security is crucial in detecting hidden threats that rely on visual deception.
What is Image Processing? Image processing involves manipulating and analyzing images to extract useful information or detect specific features. In our multi-modal protection system, image processing is used to ensure that images, including QR codes, are thoroughly examined for potential threats.
How Image Processing Works: Image processing refines images to reveal obscured content by tweaking contrast and sharpness, setting the stage for deeper analysis. It then extracts key features, like the distinct shape of a QR code, to assess authenticity. Beyond feature identification, it's also vigilant in spotting anomalies—unusual patterns or concealed text that might be cloaked within an image—serving as a critical line of defense against hidden threats.
Role in Quishing Defense: Image processing ensures that images, especially those containing QR codes, are carefully examined for any signs of tampering or malicious content. It assists in verifying the authenticity of QR codes and identifying any hidden threats within images.
As cyber threats continue to morph, our vigilance and adaptive technologies must outpace them. With our multi-modal approach and unique blend of AI and human insights, you're equipped with a sophisticated arsenal against the most cunning of quishing attacks.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)













.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)


