Table of Contents
As businesses continue to deal with the impact of coronavirus and COVID-19, they face another unfortunate reality: Phishing scammers are working overtime to take advantage of the situation. We’ve already seen an emerging trend of phishing attacks related to the coronavirus, and these scams are likely to increase until the virus has been mitigated.
While security perimeters are scattered due to remote work, clever attackers are doing their homework in order to target some of the most vulnerable organizations. Posing as internal HR team members, government agencies, or global health institutions, attackers typically disguise malware email attachments as “helpful” coronavirus resources, or lure employees to fake landing pages and steal their credentials.
Certainly, these types of trending “zero-day” attacks, which are constantly iterating in order to prey on employees through social engineering, are not new. But this particular avenue of attack targets a potent emotional trigger, and businesses also face the prospect of recurring, seasonal remote work due to additional “waves” of COVID-19 until a vaccine is found. Given this new reality, many companies are being forced to ask themselves an important question: Can our phishing defenses quickly and thoroughly adapt to emerging or seasonal threats?
Who Should Be On The Lookout For A Coronavirus Phishing Attack?
Hospital staff and other healthcare workers are the most obvious target for this emerging threat. These employees are under incredible pressure and working long hours to treat COVID-19 patients, manage supply logistics, and limit the virus’ spread. It just takes one misclick from a tired, stressed out healthcare worker to put critical systems at risk.
However, other organizations also face a heightened risk. Everyone is eager to stay educated about the latest coronavirus updates, which means some employees may lower their guard if they think relevant information is being shared.
Hospitals And Healthcare Workers
According to the Electronic Frontier Foundation, hard-hit hospitals in New York have already been notifying staff about incoming phishing attacks. Some recurring attacks include:
A fraudulent email from cybercriminals pretending to represent international entities like the World Health Organization (WHO)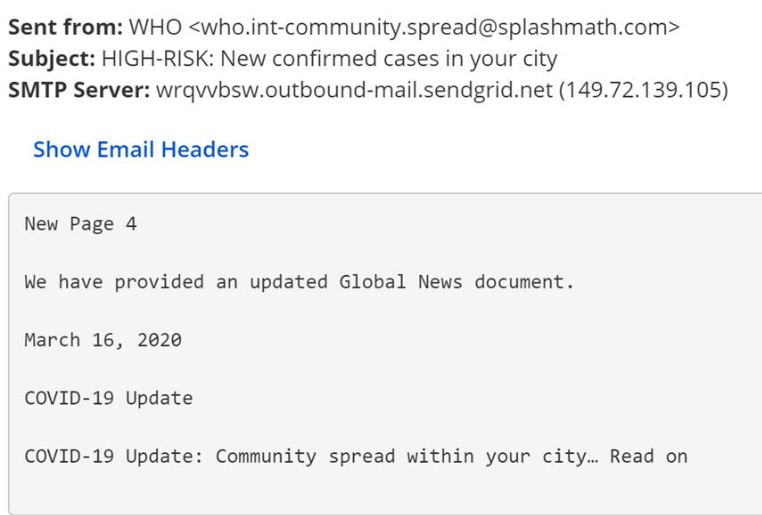
- A similar phishing scam where the “source” is a national governmental agency, typically the Centers for Disease Control and Prevention (CDC), and the email claims to provide critical info related to the prevention and treatment of COVID-19 within an attachment
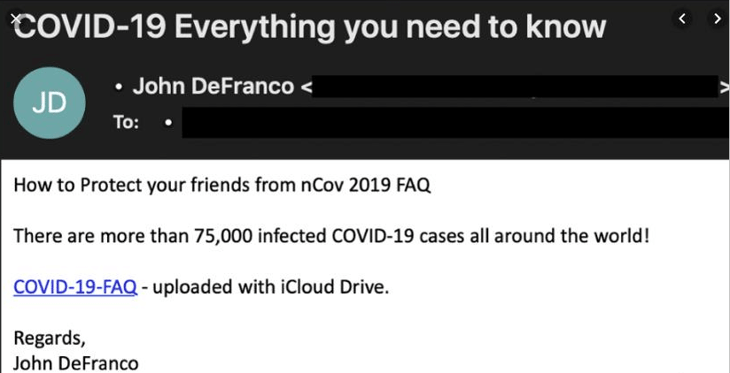
- A phishing email disguised as an urgent message from medical suppliers, which claims that employees need to take specific actions (usually some form of offering to gain their credentials) in order to ensure deliveries are made
Some of these emails will attempt to get users to download PDFs or Word documents – purportedly sharing “vital” coronavirus information – that are embedded with malicious code. Others attempt to drive users to a fake landing page in order to initiate credential theft or execute malicious code. This malicious code, or malware, typically comes in the form of a trojan (seemingly legitimate applications that act maliciously in the background) or ransomware (software that can lock down entire systems or hold an individual or company’s data for ransom).
While some ransomware groups targeting businesses have publicly pledged not to single out healthcare providers for the duration of the pandemic, attacks on medical care facilities have continued nonetheless. In late April, Parkview Medical Center in Pueblo, Colo. was hit in a ransomware attack that reportedly rendered inoperable the hospital’s system for storing patient information. And in May Europe’s Largest Private Hospital Operator Fresenius Hit by Ransomware.
What About Businesses Outside Of The Healthcare Industry?
As we mentioned in our intro, organizational security perimeters have been scattered by a tidal wave of remote work. Employees who are new to remote security protocols may find them cumbersome and be tempted to go around established processes, such as the proper use of VPNs and firewalls. And if you’re anti-phishing solutions don’t extend to your employees’ mobile devices, then you face another potential headache.
For business outside of healthcare, the most common scam we’re seeing involves fraudulent workplace policy emails. Norton cites a common example where a phishing email masks itself as an updated “Communicable Disease Management Policy” from HR. Users who click on the attachment then download malicious software.
What Can You Do About Trending Zero-Day Attacks?
First, it’s important to reinforce existing email security protocols with your employees. Sticking to the security plan while sheltering in place is more important than ever for WFH employees.
But it’s also important to ensure your anti-phishing measures are truly adaptive and offer multi-layered protection against emerging threats. Conventional phishing defenses simply won’t cut it during these unusual times (or during any trending and seasonal attacks in the future). Are you confident that your legacy solutions have the ability to automatically self-learn and adapt to emerging phishing attacks?
The IRONSCALES Platform offers a comprehensive, automated, and crowd-sourced solution. We designed our infrastructure to be particularly robust against trending threats by combining the best aspects of self-learning artificial intelligence with decentralized, democratized human intelligence. This means we have the capabilities you need to prepare for and protect against zero-days and trending phishing scams, including:
- Self-Learning Capabilities: Our powerful software doesn’t just learn your users’ mailbox and communication habits – it also shares anonymous data points across our entire client base to detect, analyze, and remediate trending threats while creating a true human-machine feedback loop. This way, it doesn’t really matter if you’re facing a “new” trend in phishing – our potent mix of human and machine intelligence will find the patterns.
- Crowdsourced Collaboration: A decentralized and democractized approach to email security means we crowdsource the best threat intelligence and expertise anonmously from IRONSCALES customers of leading security analysts and feed it back into our platform in real-time. Nobody else has as much real-time access and actionable intelligence about emerging trends, which helps our customers get extended visibility into zero-days threats and allows them to block those threats automatically or remediate them with one click – before they can cause damage.
- Robust Automation: Whether your SOC team is in the office or at home, IRONSCALES’ automated workflow makes it easier for security professionals to maintain performance and output during high-pressure situations. Manual detection and remediation can be reduced by up to 90%, and these automated processes are also backed up by an extensive support infrastructure. Respond to incidents from our convenient mobile app, or reach a security analyst whenever you need with our always-on in-app chat feature.
We’re happy to put IRONSCALES up against any competing product with a free, no-obligation demo. Request a demo today and see how you can have your own complete anti-phishing solution deployed in a couple of clicks and start seeing the value immediately.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)



