Table of Contents
Background
The IRONSCALES research team has recently noticed an alarming increase in the exploitation of legitimate file sharing services to deliver phishing attacks. Specifically, we are seeing activity with Microsoft OneDrive and Sharepoint, as well as other services like Dropbox, WeTransfer and Google Drive. Given the widespread use of Microsoft Office 365 and SharePoint, the potential damage of this phishing campaign is significant. Companies should be on high alert for these phishing attacks.
The phish
Employees at a number of companies have started to receive emails from legitimate looking sender addresses with a spoofed display name (which usually contains the recipient’s domain). The spoofed display name appears to be a Sharepoint file coming from someone from within the recipient’s company with a subject line similar to “Staff Report” or “Bonuses”. The return-path address of the attackers contains the variations of the word “referral” and uses top level domains including the domain “com.com”, which is commonly used in phishing campaigns for spoofing. The body of the email includes Microsoft branding to make it look like a trusted and legitimate message.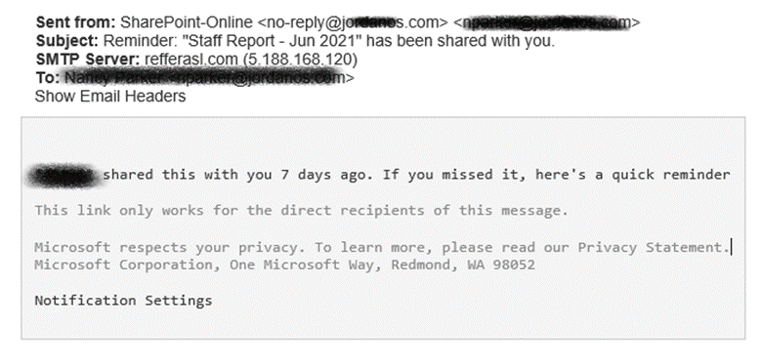
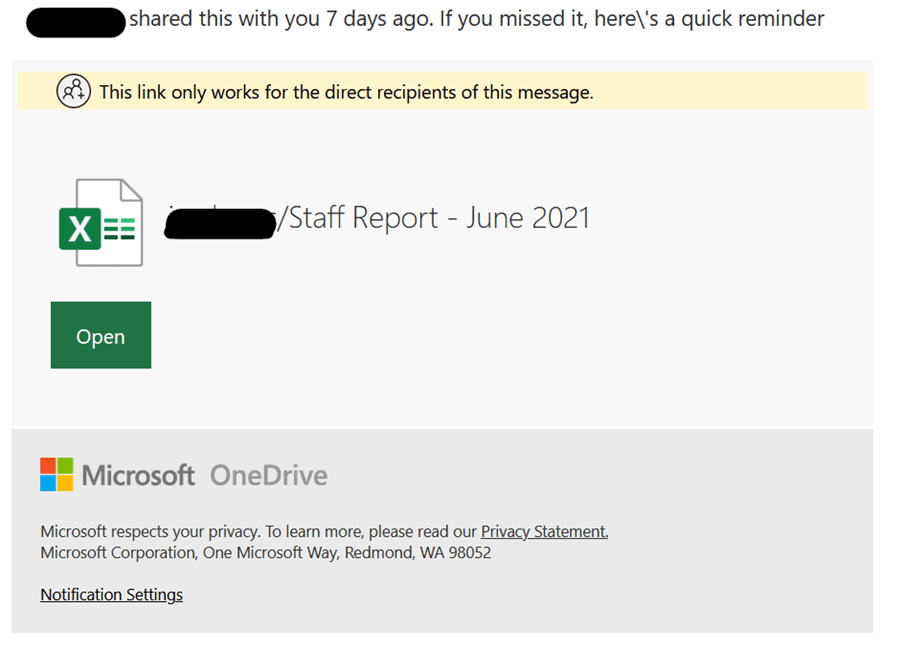 This message contains links that are detected as being malicious due to the exploitation of the legitimate service that the attackers are using. In addition, these messages also contain legitimate Microsoft links to give the impression of authenticity.
This message contains links that are detected as being malicious due to the exploitation of the legitimate service that the attackers are using. In addition, these messages also contain legitimate Microsoft links to give the impression of authenticity.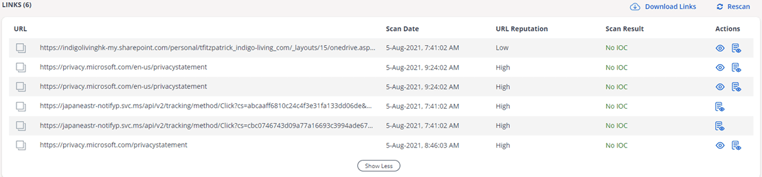
The attackers didn’t stop there. They also used a technique to render the link undetectable by legacy email security technologies. In the image above, you can see the links that were detected. However, there is another link in the body of the email that was missed because of the address malform. This link then leads to a fake Outlook login page.
https:/\\storage.cloud.google.com/dnqnenqsa00qd0080dswawa.appspot.com/index.html
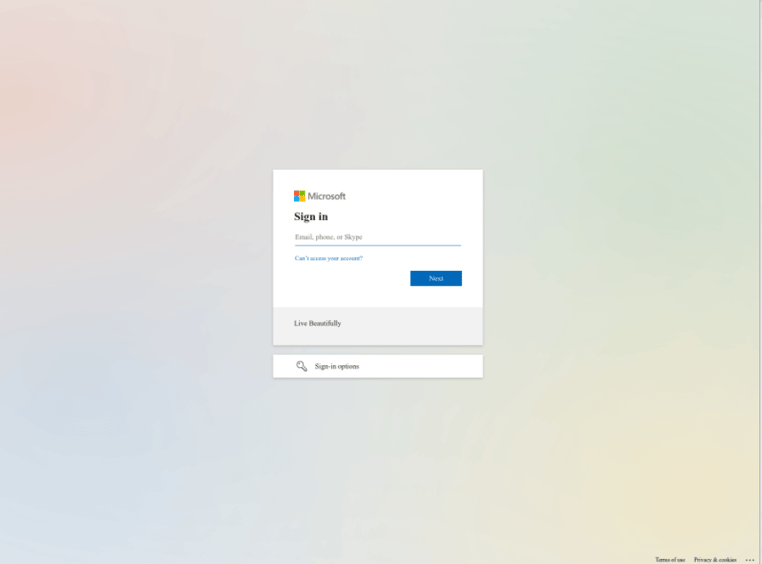
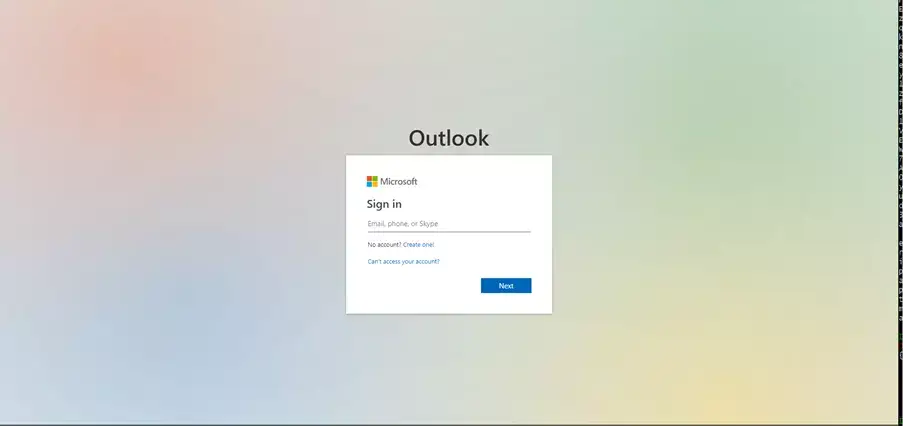
Once at the fake Outlook login page, the victim is asked to enter their credentials.
If the recipient presses “Open” within the phishing email, they are directed to this login page:
.webp?width=762&name=outlook%20login%20(1).webp)
Should the victim hit the “Notification Settings” link in the phishing email they are taken to this login page:
How we identified the attack
The initial notification of this incident came from our customer Community, which acts as an early warning system for zero day and other previously unknown phishing attacks. After receiving the Community notification, our AI (named Themis) began scanning all emails across our entire 4,500+ customers to look for this attack type. Themis automatically pulled all infected emails out of the end users’ mailboxes to prevent them from falling victim to the attack.
How to protect yourself from credential theft attacks
- Do not open any links or attachments that you receive in emails from unknown sources.
- If a colleague sent you a link or shared a file with you that you believe is suspicious, confirm with them by phone or in person that they really are the sender.
- Hover on the links with your mouse cursor to see the address it links to. If the link doesn’t look familiar, report the email to your security team.
- Hover your mouse over the email sender’s name. If the address displayed does not match the real email address of the sender report the email to your security team.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.












.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)




