Table of Contents
Background
The IRONSCALES research team has recently identified a social engineering phishing scam that leverages confusion and disinformation about people and corporate COVID vaccine requirements to trick victims into providing their Microsoft Outlook credentials to the attackers.
The Phish
In this attack, the threat actors send a phishing email to the victims at a specific company under the guide of being from the company’s HR team. The phishing email contains a form that employees are directed to complete to provide their COVID vaccination status in order to prevent being hit with “significant fines”. Given the threat of financial consequences for non-compliance, victims are likely to take action on the phony request.
.png?width=762&name=vax-email-scam-image1%20(1).png)
The Payload
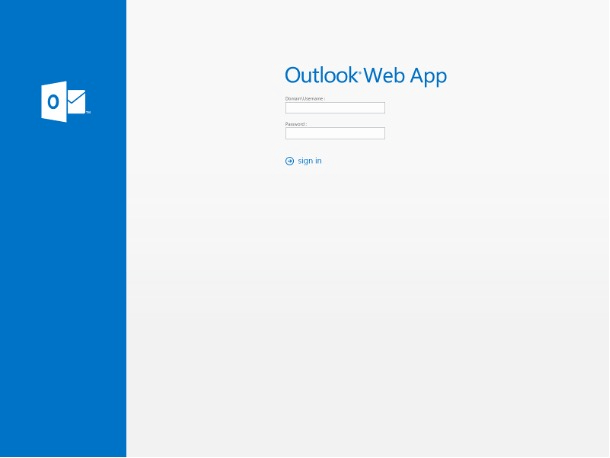
In this attack, the payload is a fake landing page that appears very similar to a legitimate Microsoft Outlook landing page. Should the victim enter their credentials the attackers will be able to harvest their details and use them as a launching pad for further nefarious activities.
How We Identified the Attack
IRONSCALES was able to identify the attack in several ways. First, our visual scanner (i.e. “Computer Vision”) was able to detect that the Outlook login page was not legitimate. Our AI was also able to recognize language within the phishing email that was suspicious (particularly the urgent tone in the email. Finally, our platform identified a discrepancy between the name in the Sender field and the name used to sign the email. All these indications of suspected phishing resulted in the IRONSCALES platform automatically flagging the email for further investigation.
How to Protect Yourself from Credential Theft Attacks
- Do not open any links or attachments that you receive in emails from unknown sources.
- If a colleague sent you a link or shared a file with you that you believe is suspicious, confirm with them by phone or in person that they really are the sender.
- Hover on the links with your mouse cursor to see the address it links to. If the link doesn’t look familiar, report the email to your security team.
- Hover your mouse over the email sender’s name. If the address displayed does not match the real email address of the sender report the email to your security team.
To learn more about IRONSCALES’ award-winning anti-phishing solution, please sign up for a demo today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)



