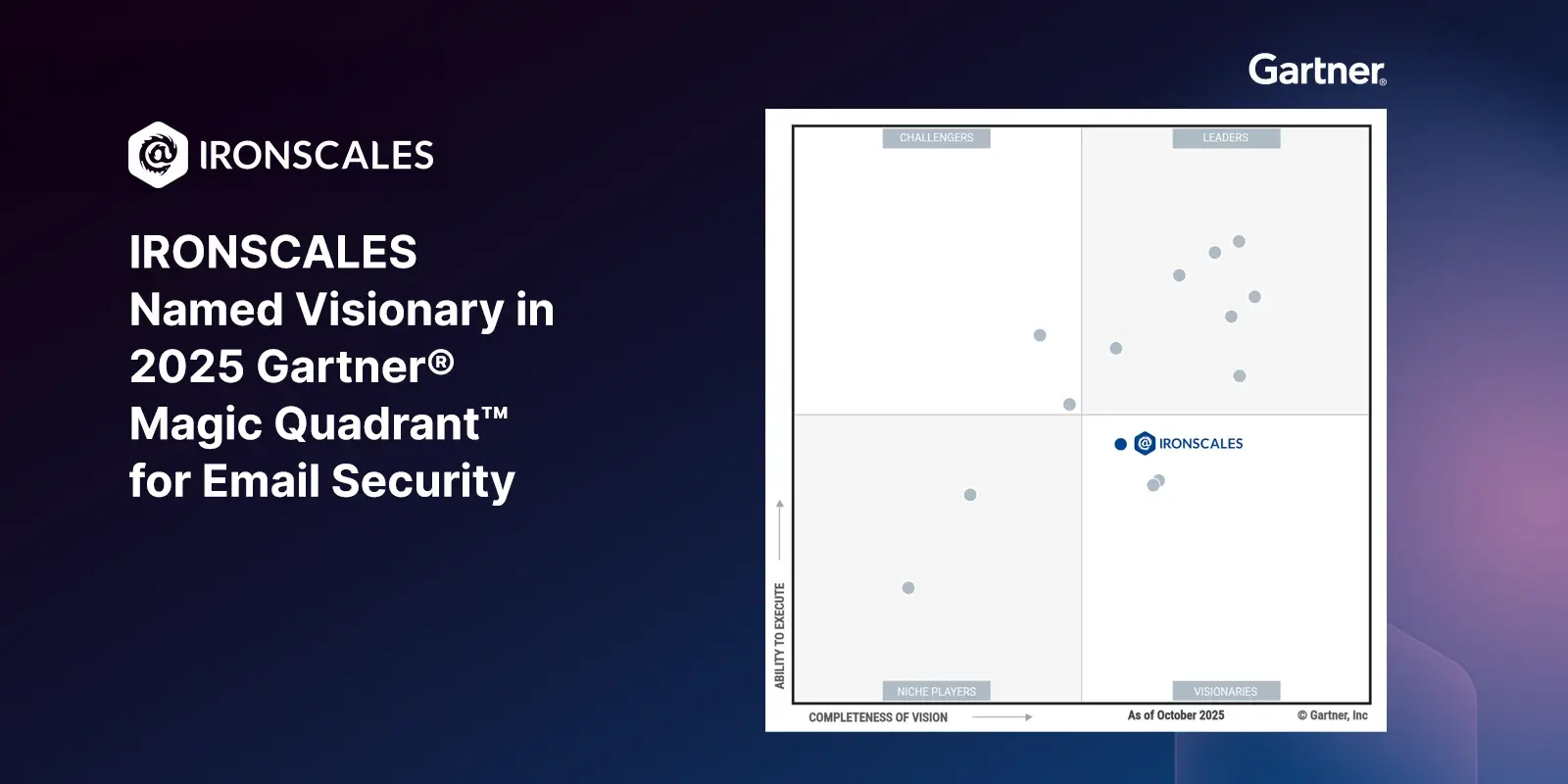
Google's November 2025 DMARC Crackdown: What Security and Marketing Leaders Need to Know

Google has moved past warnings. Starting November 2025, Gmail will reject non-compliant bulk email outright, ending the grace period that began in February 2024. For CISOs and marketing leaders alike,...
Read more
/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)