Table of Contents
Introduction
The cryptocurrency market has grown exponentially in recent years, with the total market capitalization of cryptocurrencies surpassing $200 billion. This rapid growth has caught the attention of cybercriminals who are now targeting end users with an array of email phishing attacks in an attempt to steal from investors. While this is a relatively new threat, it is rapidly growing in size as more people invest and store their assets in digital form. Fortunately, we are catching these attacks and protecting our customers before any damage can be done. Below is one recent example.
Background
In this attack, cybercriminals impersonated www.blockchain.com in an attempt to steal login credentials of a Blockchain cryptocurrency wallet. The attacker sent the targeted victim an email notifying them of an attempted login to their account. Once the victim cooperates with the attack, they are redirected to a malicious website that looks just like one belonging on blockchain.com.
The Phish
An impersonation of an email address is a tactic commonly used in phishing attacks to disguise the true sender. In this example, the attacker manipulated the sender name field to give the impression to the victim that the email was coming from blockchain.com. Upon closer inspection, it is clear that the email actually came from marketingsupport@sync-shup.com.
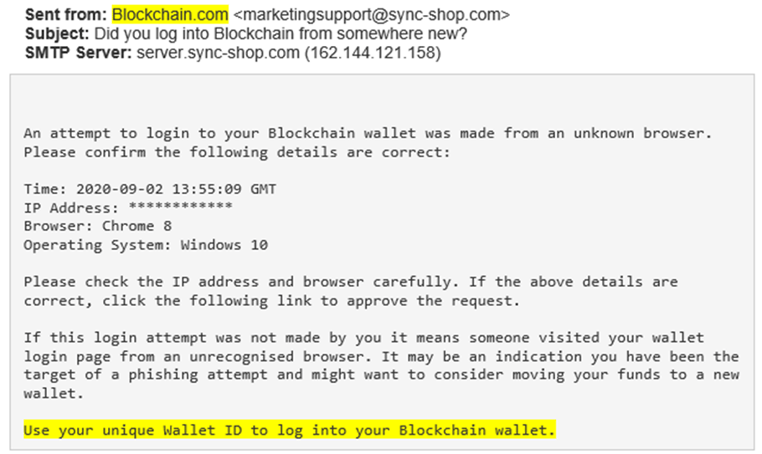 The Payload
The Payload
The payload of this attack is the malicious landing page that is designed to harvest the victim’s credentials. The link that directed to the landing page was embedded at the bottom of the email body: “Use your unique Wallet ID to log into your Blockchain wallet.” When the user engaged, they were directed to a fake login landing page. While the landing page appears similar to the authentic Blockchain login page, should the recipient input their credentials into the respective fields, they will be harvested by the attackers, potentially resulting in the theft of funds and account compromise.
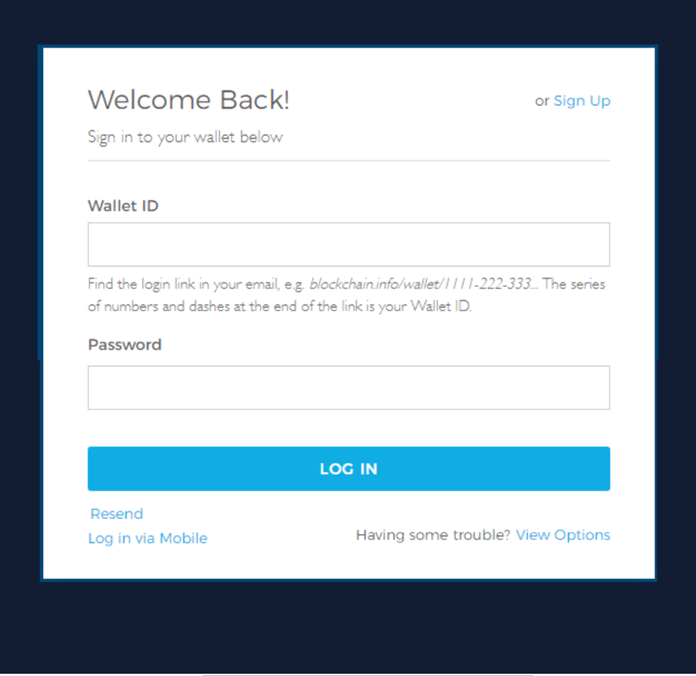
SEG Bypass
This attack bypassed the Secure Email Gateway (SEG) that was “protecting” the victim’s company because it was sent from a series of previously compromised email addresses and servers. Existing authentication technologies such as SPF and DMARC are not developed or are equipped to prevent email attacks from legitimate emails. Cybercriminals often take advantage of this with Account Takeover (ATO) attacks.
How we Identified the Attack
Themis, IRONSCALES’ AI, recognized and prevented this attack via a nexus of detection techniques. A combination of sender anomaly, sentiment analysis, and computer vision analyses culminated with a verdict that it was an attempted malicious phishing attack. Without Themis’ AI capabilities, this dangerous email would likely have reached the mailboxes of the targeted victims.
Identifying and Remediating Advanced Phishing Threats
This is an example of a clever and targeted phishing attack design to bypass a SEG as well as SPF and DMARC authentication technologies. These legacy technologies are good at detecting large scale phishing campaigns coming from suspicious/blocklisted domains and servers. However, they remain weak in their ability to identify more advanced email threats like the one described here.
We invite you to learn more about how IRONSCALES can fight against this and many other types of phishing attacks by combining human and machine intelligence by requesting a demo today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)













.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)
