Table of Contents
Background
Cybercriminals continue to innovate their attack methods. IRONSCALES recently identified a specific attack that affected over 90 of our customers. Specifically, the attackers tried to steal end-user credentials with a fake landing page. The attack featured a VIP impersonation of an employee at Stewart Title, a well-known insurance agency.
The phish
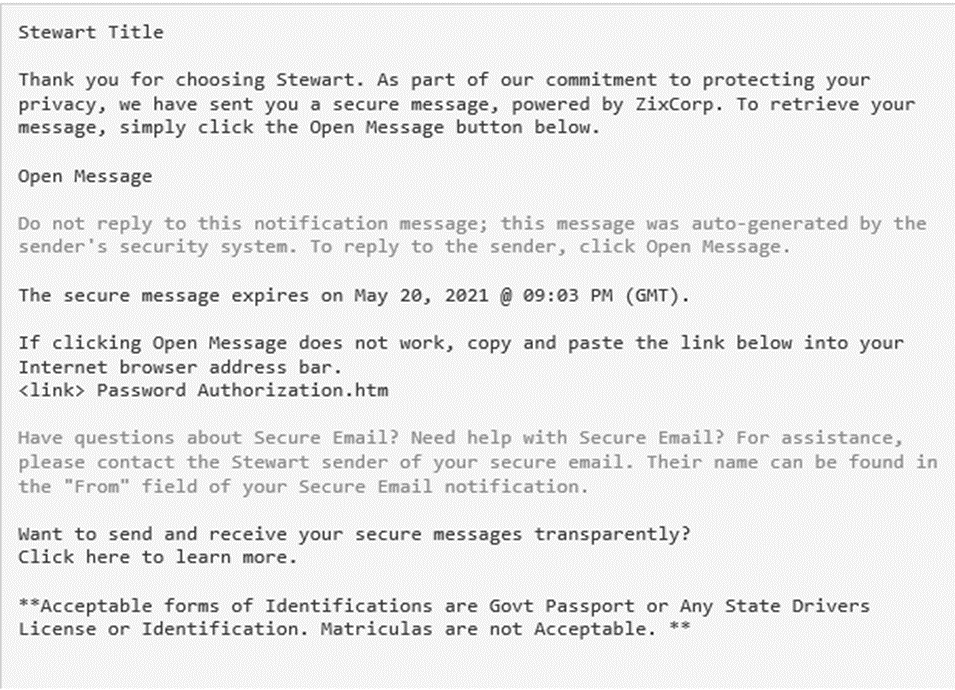
End-users received an email with the subject line “Encrypt- CD FINALIZED /WIRE BREAKDOWN/ Closing instructions”. The tone of this message creates a sense of urgency with the end-users, as it appears that the message contains information of a sensitive financial nature that requires immediate action. The text contained in the body of the email stated that a secure message needs to be retrieved to move forward with processing this transaction. To access the fake secure message, users are directed to click on a link in the email that says “Open Message” or to copy and paste the embedded link into their browser.
The impersonation
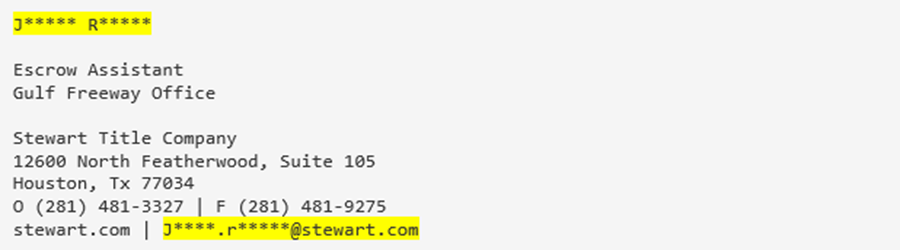
There are two indicators of impersonation in the email signature block that are both difficult for the unsuspecting end-user to identify.
- The email was shown as being sent from the name of an actual executive from Stewart Title. However, the domain of the sender’s email address (J******@cafangas.com) is not authentic.
- The signature block contains the correct email address of the executive who is being impersonated. However, this email address and the email address from number 1 above are different.
The payload
The link embedded in the “Open Message” portion of the email appears as if it would take the user to the Stewart Title web portal. Upon closer inspection, it turns out that the link actually redirects the user to a credential harvesting page with the domain [workshopmake.com]. Upon arriving at the fake Stewart Title portal (which visually appears to be identical to the actual Stewart Title registration page), the user is then asked to enter their Office 365 credentials. If the user does so, the attacker then can take over the user’s Office 365 accounts and be able to access sensitive information.
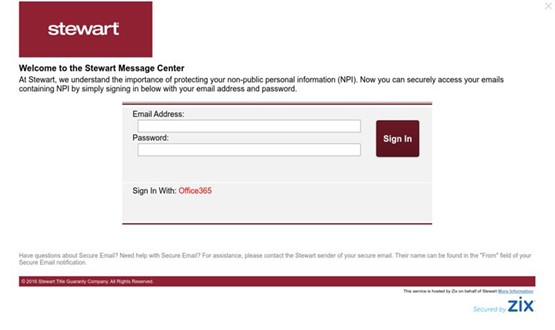
The email security tool bypass
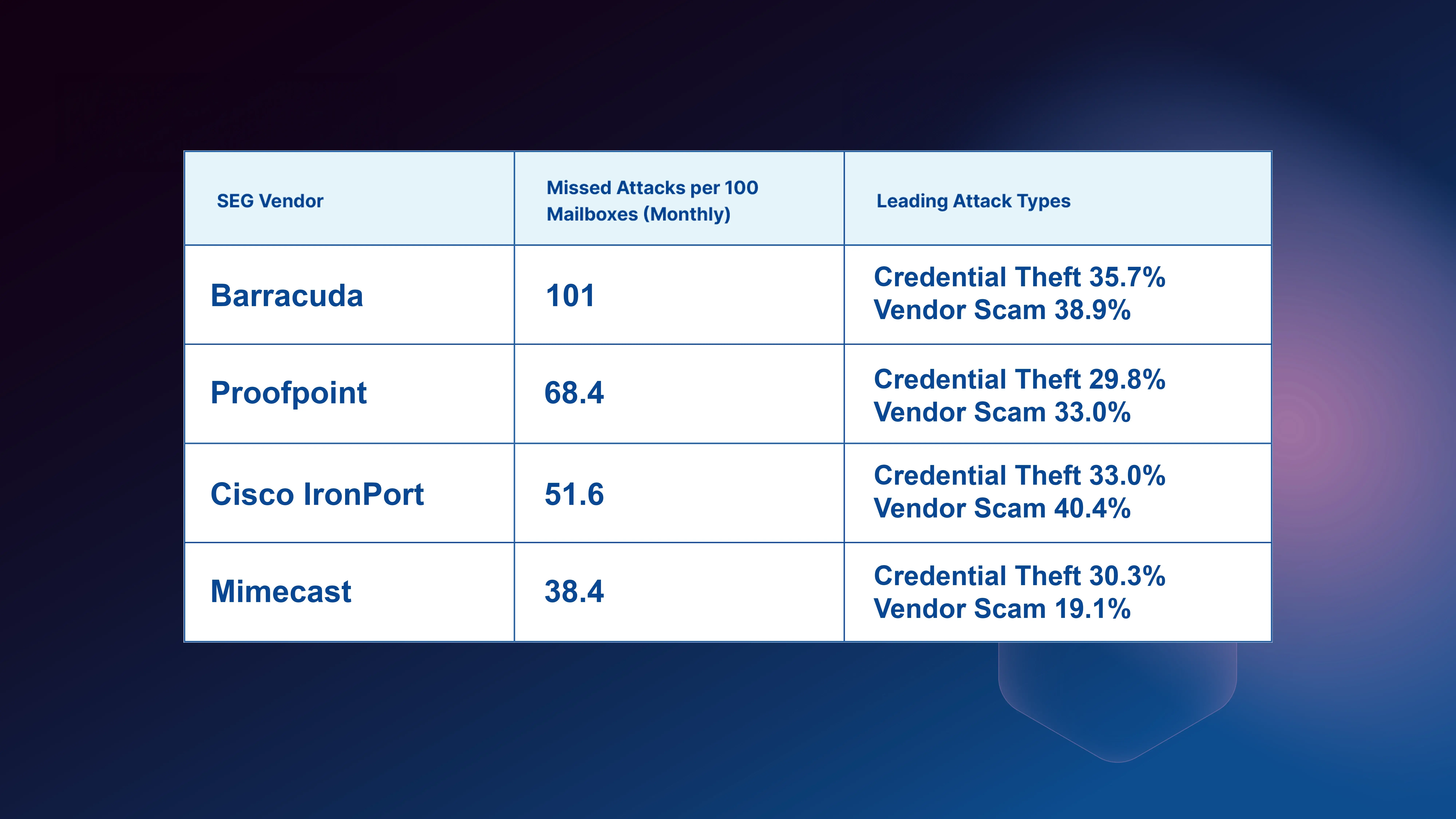
For the attack to be successful, the phishing email first had to get past the email security defenses of the victim’s company. In this case, the email was able to successfully bypass the customer’s Mimecast secure email gateway (SEG). There are three possible ways that this could have happened.
- A legitimate sender address/account with Mimecast had been compromise.
- The credentials of the sender address/account with Mimecast had been stolen
- The attacker manipulated the hostname/server/domain to make appear as if the email was sent from an O365 account
We believe the latter is most likely what happened, as there is a known flaw in the Office 365 Exchange Online Protection (EOP) product and our research into this attack showed that it was targeted exclusively at O365 clients.
As a result of the bypass, Mimecast inserted a message into the body of the phishing email that implied it had been scanned for viruses, implying that none had been found. As such, the email recipient almost certainly assumed that the email was safe and ultimately fell for the trap.
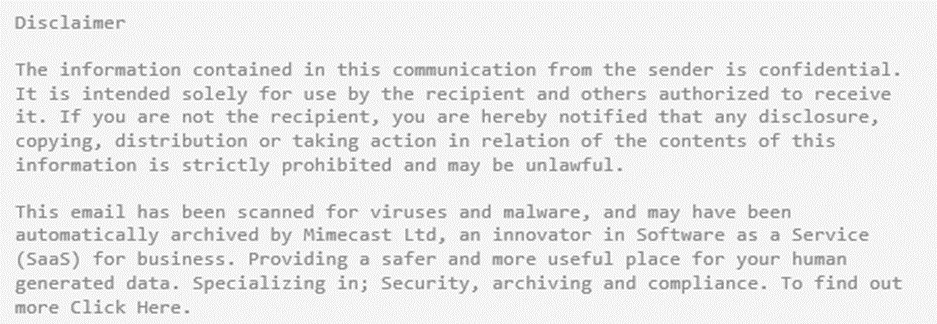
A textbook case of a successful phishing attack
- This phishing attack succeeded for several reasons:
- The bypass of the Mimecast SEG to get into the victim’s email inbox
- The use of VIP impersonation to give credibility to the identity of email sender
The email content containing a powerful combination of their being both sensitive information that needed to be accessed and a sense of urgency to take immediate action
How we identified that attack
This incident showcases the advantages of IRONSCALES’ mailbox protection technology. The incident was mitigated with a powerful combination of capabilities:
- Automated incident clustering triggered by community feedback
- Email anomaly detection
- Computer vision (visual scanner)
Community feedback: The investigation process began with a report of suspicious activity sent from our community of users. This initial report triggered an automated investigation of all emails in our system. Emails with identical or similar characteristics to the email that was reported were automatically pulled into a single cluster for further analysis.
Anomaly detection: The ability to recognize textual anomalies at a mailbox level is crucial in classifying, preventing, and mitigating threats such as these. In this case, we detected nuanced differences between the Display Name - Sender Address and the Name - Email Address found in the email body signature.
Computer vision: Once the incident was escalated our computer vision (visual scanner) analyzed the suspicious email. This resulted in us finding a malicious payload that had gone undetected by other third-party scanners.
Identifying and remediating advanced phishing threats
This is an example of a clever, well-crafted and targeted phishing attack against a legacy email security product and a distracted employee. Now imagine getting hit by hundreds, if not thousands, of these types of attacks every single day. Actually, you don’t have to, because that’s the reality facing every single company today. Forcing your employees to make judgment calls on whether or not to open each email they receive and whether or not to click on every link they’re presented is a recipe for disaster.
We invite you to learn more about how IRONSCALES can fight against this and many other types of phishing attacks by combining human and machine intelligence. Learn more at www.ironscales.com today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)