Table of Contents
Credential Harvesting Explained
Credential harvesting, also known as password harvesting or username harvesting, is a form of cyberattack that involves the theft of personal or financial data such as usernames and passwords, typically carried out through phishing, malicious websites, email scams, or malware but not always. Any social engineering techniques, digital scamming, and malware may be used to steal login credentials. By obtaining credentials to a user’s online accounts, the attacker can gain access to sensitive information and sometimes use the stolen credentials for fraudulent activities, like transferring money out of the user’s account. In some cases, credential harvesting is used to gain access to a company or organization’s network, enabling the attacker to steal data and spread malware.
How Does Credential Harvesting Work?
Most username harvesting and password harvesting attacks involve convincing the user to enter their login credentials into a malicious website or form. This is often done through phishing emails that direct recipients to a bogus version of a reputable site, like an online banking service or e-commerce store. When the user enters their username and password, the attacker can then use this information to access the user’s account and view or steal sensitive data.
In some cases, attackers may also use automated software tools to scan websites for vulnerabilities or scan networks for open ports (the latter of which can be used to gain access to a company’s internal network). Once attackers have gained access to a system, they can then install malware, or malicious software, that can be used to control the system or steal data.
How to Identify Credential Harvesting Attacks
Credential harvesting attacks can be difficult to detect, as cybercriminals use a variety of methods to acquire user credentials. These attacks even lure victims by mimicking real login pages (see example image below).
Organizations and individual users should look out for warning signs of credential harvesting, such as phishing attempts or suspicious activity on their accounts. Additionally, any sudden increase in the number of access requests from unknown sources should be viewed with caution. If a credential harvesting attack is suspected, organizations should immediately investigate and take steps to mitigate the threat.
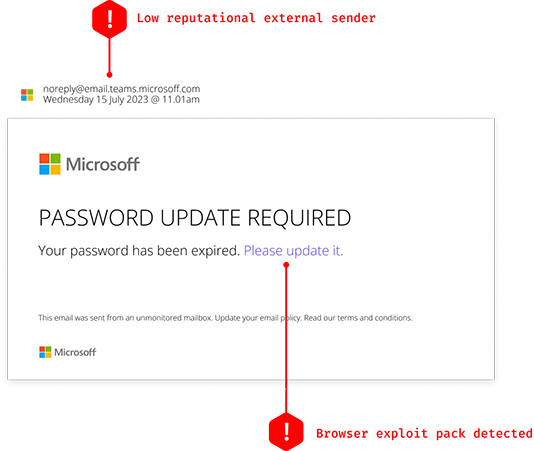
How to Prevent Credential Harvesting
Organizations can protect themselves from credential harvesting by implementing strong security protocols. These include:
- Two-factor authentication, which requires users to provide additional authentication steps before accessing the system
- Data encryption, which renders stolen information useless
- Regular security scans that look for suspicious activities on the network
- Employee training to recognize credential-harvesting attempts
See below to learn all about IRONSCALES™ award-winning credential harvesting protection tools.
Credential Harvesting Protection from IRONSCALES
IRONSCALES™ provides mailbox-level fraud and anomaly detection that conventional Secure Email Gateways (SEG) miss. Our credential harvesting solution:
- Creates a unique sender “fingerprint” for each employee. This is accomplished by analyzing “sent-from” IPs, communication context and habits, and other factors. Any deviation from the norm is detected immediately
- Leverages Natural Language Processing to flag commonly used BEC language
- Uses AI and machine learning to continuously study every employee’s inbox and detect suspicious email data and metadata
- Automatically quarantines any detected anomaly in real-time and visually flags the email subject line and body with guidance for the employee
- Adapts to sophisticated social engineering developments using AI, machine learning, and crowdsourcing techniques
- Provides automated phishing simulation testing and security awareness training to educate and train your employees to recognize credential harvesting attacks
Get a demo of IRONSCALES™ today! https://ironscales.com/get-a-demo/
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












