Table of Contents
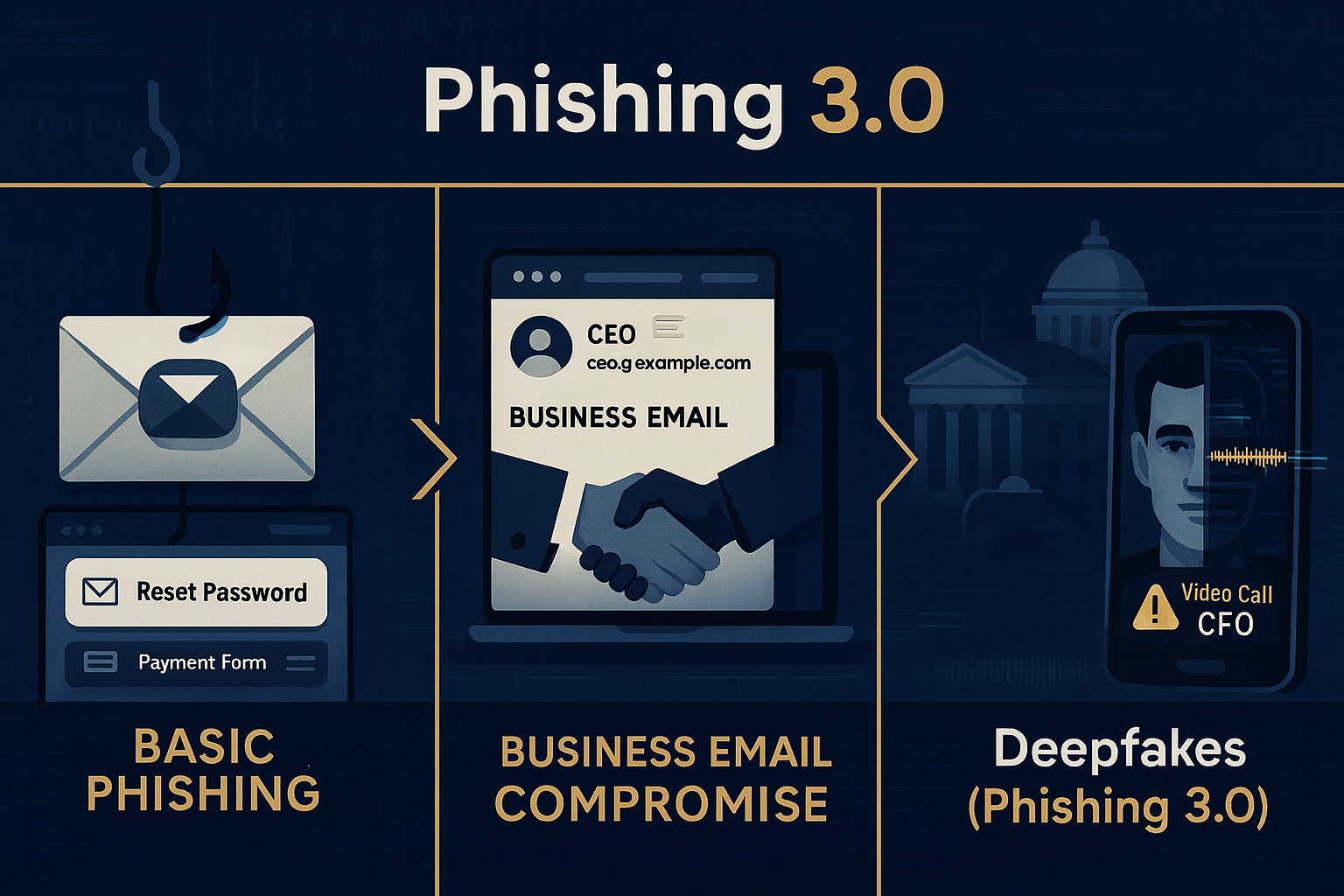
Earlier this year we warned that trust was cracking inside the inbox. Since then your inbox learned a new trick: acting. GenAI no longer just writes the lure; it manufactures the sender. With a few seconds of audio or a handful of images, attackers clone familiar voices and faces and insert them into everyday workflows: email threads, calendar invites, voicemails, quick chat notes. It looks routine because it comes through the tools you already trust. The objective is the same as classic BEC: move money, steal access, exfiltrate data. The difference is the level of social proof.
What’s accelerating the shift
GenAI has lowered the cost and skill needed to deceive. Short audio or video samples are enough to clone an executive, a customer, or a public official. Content sounds fluent in any language. Timing and tone can be tuned to match a calendar event or a quarter-end close. The result is a blended attack that looks and feels like normal business right up until a payment is sent or a privilege is granted.
Understanding Deepfakes
What they are. Deepfakes are AI-manipulated images, voices, or videos that impersonate a real person or create a synthetic one. The best examples are hard to distinguish from authentic media.
Common Deepfake Creation Methods
- Partial face morphing: Blends or alters parts of one face with another. Often used in ID photo fraud to pass a quick likeness check.
- Fully AI-generated faces: Entirely synthetic faces produced by modern generative models. Useful for creating convincing yet nonexistent identities.
- Face swapping: Replaces one face with another in images or video, mapping the “donor” face onto an impersonator.
- Face reenactment or lip sync: Changes expressions or mouth movements so a subject appears to say something new, or makes a still photo “speak.”
Why volume is rising? User-friendly apps and subscription tools make face swaps and avatar generation a few clicks away. We now see everything from crude Photoshop jobs to highly realistic media with few visible artifacts.
How They Enter Systems
- Presentation attacks: A fake is shown to the camera like a live person, for example a replayed video on a high-resolution screen. Robust face biometric systems use Presentation Attack Detection to spot signs of replay or flat images.
- Injection attacks: Manipulated media is fed directly into capture or network pipelines, bypassing the camera and normal recording steps.
Who’s Getting Hit Right Now?
- Government. Impersonations of senior officials and agencies are being used to drive clicks, harvest credentials, and push malware. These often arrive as urgent calls, voicemails, or messages that reference real programs or events.
- Financial institutions, including call centers. Classic BEC has evolved into deepfake-enabled fraud on live calls and in collaboration tools. Call centers deserve special attention. Voice clones are pressuring agents to bypass knowledge-based checks, reset accounts, or change beneficiary details.
- Social platforms and media networks. Deepfake videos and livestreams are promoting fake offers and investment scams using the likeness of well-known figures. These clips seed trust that is later exploited by email or direct messages.
- Celebrity and PR management firms. Unauthorized endorsements, fabricated statements, and miscaptioned clips are driving reputational crises and incident response. The speed of amplification on social turns a false claim into a headline before teams can verify.
How Deepfake Attacks Show Up In Your Org
- Email-delivered audio or video. The email looks routine. The attachment or link plays a “CEO update,” a “board announcement,” or a “customer voicemail” that asks for action.
- Real-time vishing with cloned speakers. Attackers call a help desk or a relationship manager using the voice of an executive or VIP client. The script is tight and urgent.
- Voice notes inside collaboration tools. A chat thread starts in email, then moves to a quick voice message in Teams, Google Chat, Zoom, or Slack. The escalation path is the point.
- Meeting invites with a synthetic participant. The calendar hold appears legitimate. In the meeting, a realistic voice or face asks for a wire, an MFA reset, or a file share.
- Social-to-email blends. A deepfake video runs as an ad or goes viral. The follow-up email or DM references that content to add credibility and push the target over the line.
Top 5 Recommendations for Government, Media, and Financial Institutions
- Assume voice and video can lie
Adopt a “no-voice approvals” baseline. Verify any request for money, credentials, or access using a known channel. Use shared passphrases for high-risk scenarios. Ban urgent changes via voice notes or meeting chat. - Lock down money and privilege changes
Codify dual authorization and mandatory callbacks for new payees, bank-detail edits, wires above a threshold, emergency access, and vendor-master changes. Require step-up verification for first-time or out-of-pattern transactions. - Add real identity checks to live communications
For finance reviews, privileged IT work, and emergency ops calls, require one of the following: MFA on join, a one-time PIN shared via a separate system, or liveness-checked biometrics where feasible. Default to “pause and verify” on any time-pressured request. - Harden the human layer across channels
Write policy that email or voice alone cannot move money or change access. Train to decision points such as callbacks and slow-downs, not gimmicks. Enforce least privilege and tighten controls for teams that move funds or grant rights, including call centers. - Make AI-enabled fraud a board metric and practice it
Track time to verify, percent of high-risk flows gated by step-up checks, first-time payment callback rate, and employee reporting rate. Run a quarterly tabletop. A realistic scenario is “executive voice note plus emergency wire.” Prioritize enhanced checks for high-risk personas such as executives, treasury, procurement, election or grants staff, and VIP clients.
The IRONSCALES Deepfake Solution
Deepfakes turn identity into an attack surface. We built protection that treats identity as a first-class signal and meets people where they work.
- Live deepfake detection for audio and video. Real-time analysis spots synthetic voices and faces and verifies the person behind the interaction.
- Artifact, biometric, and behavior analysis. Multiple detection methods look for synthesis artifacts, validate liveness, and compare tone and timing against known patterns.
- Inbox-level protection without MX changes. Connect to Microsoft 365 or Google Workspace with APIs. Protect the place where attacks start.
- Fast setup with automated remediation. Cluster and remove look-alike attacks across mailboxes in seconds. Free analysts from repetitive cleanup.
- AI plus human insights. Adaptive models learn from every mailbox and from SOC feedback. A global community of admins helps surface brand-new tricks faster.
- One platform for the full response. Reporting, banners, simulations, and remediation live in the same workflow. Your analysts do not need to pivot tools to move from detection to coaching to cleanup.
What this means for your end users?
- Identity claims in email, meetings, and voice are verified, not assumed.
- Employees get clear guidance in the moment, so they act with confidence.
- Analysts see fewer noisy tickets and more high-value signals.
- Rollout is measured in minutes, not quarters.
Deepfake Protection: The Next Frontier in Email Security
Deepfakes are here, reshaping the threat landscape faster than most defenses can adapt. IRONSCALES anticipated this shift and is leading with technology that stops synthetic impersonation before it ever reaches your people.
Our Deepfake Protection combines automated remediation with advanced identity validation to eliminate attacks that legacy tools miss. This is not experimental. It is the next evolution of email security, built to protect enterprises against phishing 3.0.
Visit our Deepfake Learning Center to learn more and see why IRONSCALES is setting the standard for tomorrow’s threats.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)
