Table of Contents
Synthetic media isn’t just something out of the 1984 classic The Terminator anymore.
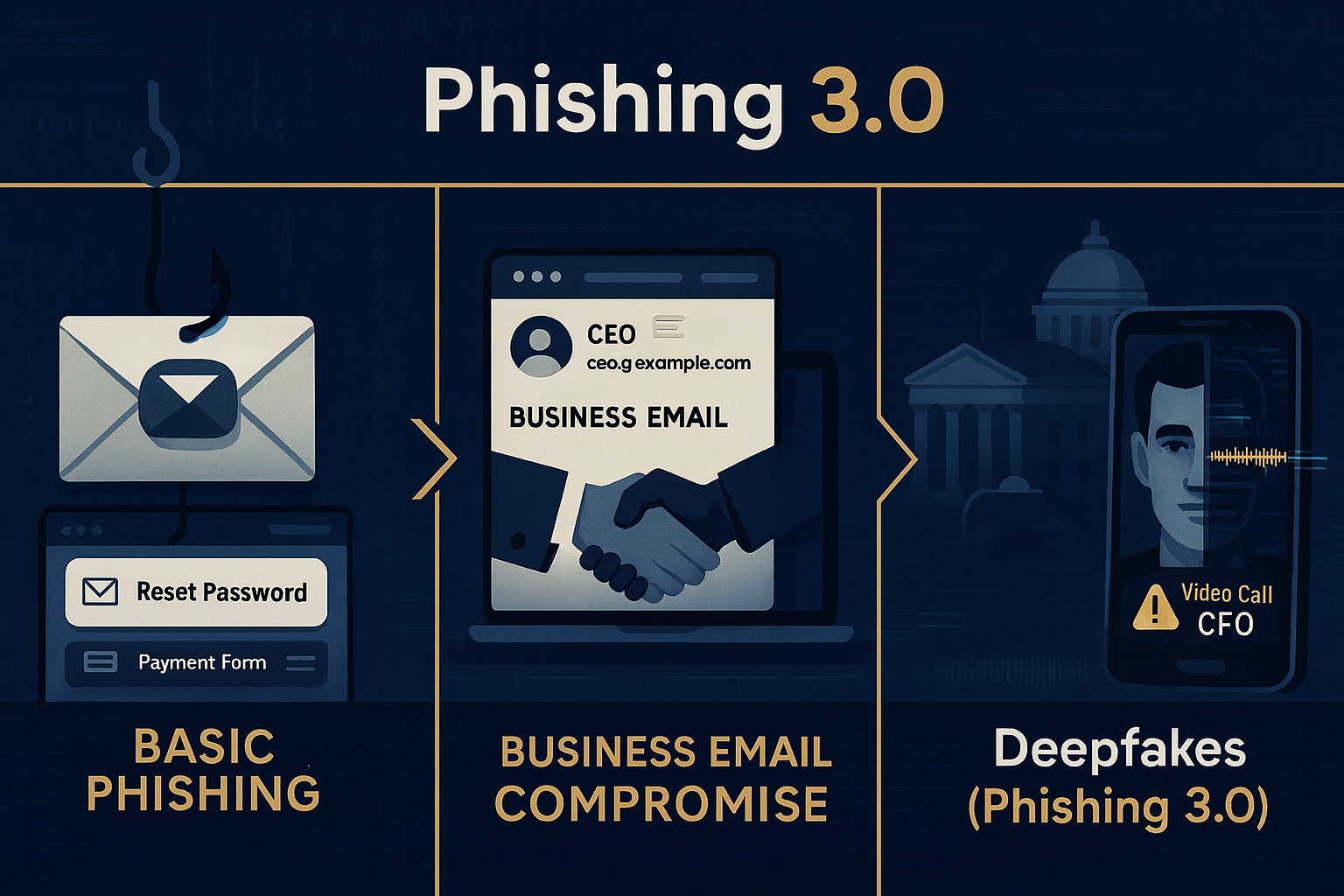
As deepfake technology becomes more accessible and convincing, criminals are weaponizing it to craft persuasive content that easily bypasses traditional email security defenses. With the line between real and fake increasingly blurred, you might be asking yourself, “How big of an issue is this?”
Well, that is exactly what we’re going to unpack in this blog.
A New Layer of Deception in Email Threats
Historically, phishing emails have relied on poor grammar, suspicious links, or spoofed domains to trick recipients. But with deepfakes, threat actors now craft hyper-realistic content, shifting the nature of social engineering into something far more persuasive—and much harder to detect. These synthetic assets—audio, video, and text—are often customized using publicly available data, making each attack more targeted and believable.
Voice Deepfakes
- What is it?
These attacks leverage AI-generated audio to mimic the exact tone, cadence, and speech patterns of a trusted executive or colleague. Criminals use these synthetic voicemails to pressure employees into authorizing payments, sharing sensitive credentials, or bypassing established security procedures. - Scope of Adoption:
The technology is now readily accessible, with open-source voice synthesis tools requiring only a short voice sample—often pulled from public interviews or social media—to recreate a convincing impersonation.
Synthetic Videos
- What is it?
Attackers can now produce fabricated video clips using AI-driven facial reenactment and lip-sync technologies, creating footage of someone appearing to speak in real time. - Scope of Adoption:
These videos are increasingly used in high-stakes phishing attempts where visual confirmation adds credibility—such as fake video calls from C-suite leaders authorizing wire transfers or emergency actions. As deepfake video production becomes faster and less resource-intensive, email-based video impersonation could become a mainstream tactic in BEC and spear-phishing operations.
Deepfake Emails
- What is it?
This is a deceptive email that incorporates synthetic media or AI-generated content—such as fake voice recordings, videos, or hyper-personalized text—to impersonate someone the recipient knows and trusts. - Scope of Adoption:
Deepfake emails are becoming a serious and rapidly escalating problem in cybersecurity, especially within phishing and business email compromise (BEC) campaigns.
These tactics create a false sense of authenticity that makes traditional phishing detection methods less effective. A forged voicemail from a CEO, for instance, urging a finance employee to expedite a payment, is much more compelling when it sounds exactly like the executive.
Why Deepfakes Matter for Email Security
Traditional phishing once relied on volume and unsophisticated lures—a spray-and-pray methodology, if you will. Deepfakes enable criminals to execute highly targeted, highly convincing attacks at scale. This evolution makes it easier to impersonate authority figures, exploit urgency, and manipulate human trust in ways that SEGs and rule-based filters were never designed to detect.
According to a 2024 report from the FBI’s Internet Crime Complaint Center (IC3), business email compromise (BEC) attacks involving synthetic voice or video elements rose by over 25% year-over-year. These attacks increasingly combine AI-generated content with compromised email accounts, creating multi-layered threats that appear internally initiated. Victims aren’t just falling for malicious links—they’re responding to realistic audio prompts or video messages that mirror real conversations or leadership directives.
The most alarming aspect? Deepfake-enhanced phishing is context-driven, not payload-based. It doesn't rely on attachments, malicious URLs, or malware that can be flagged by traditional tools. Instead, these attacks manipulate behavior through realistic impersonation—making them inherently harder to detect using static rules, keyword filters, or domain checks.
Deepfake Incidents
Here are real-world examples showing how deepfakes are already impacting organizations and individuals:
Hong Kong-Based Multinational Firm Loses $25 Million
In early 2024, a finance worker at a multinational company participated in a video conference call with individuals appearing to be the company's CFO and other executives. Unbeknownst to the employee, the participants were deepfake avatars created by scammers. Trusting the authenticity of the call, the employee authorized a $25 million transfer. This case demonstrates the sophisticated use of deepfake technology to manipulate corporate procedures.
Senator Targeted with Deepfake Video Call
In September 2024, U.S. Senator Ben Cardin was targeted in a deepfake video call by an individual impersonating Ukraine's former foreign minister, Dmytro Kuleba. The imposter used AI-generated visuals and audio to closely mimic Kuleba, attempting to extract sensitive political information. Senator Cardin became suspicious and reported the incident—highlighting how deepfakes are entering the world of political deception.
Financial Analyst Impersonation in Investment Scam
In March 2025, scammers created a deepfake video of Michael Hewson, a well-known financial analyst, to promote a fraudulent investment scheme. The deepfake convincingly replicated Hewson's appearance and voice, misleading viewers into believing he endorsed the scam. This incident shows how deepfakes can exploit trusted figures for financial fraud.
What Cybersecurity Teams Can Do
To counter deepfake-powered phishing, security teams must evolve beyond perimeter-based defenses. That includes investing in adaptive, AI-powered solutions that understand behavioral context, communication patterns, and anomaly detection.
Four strategies to stay ahead:
- Leverage AI for AI
Use machine learning-driven email security platforms that flag suspicious tone shifts, sender behavior anomalies, and unnatural communication flows—even when the content itself appears legit. These systems learn internal communication norms over time, making it easier to detect subtle deviations introduced by attackers using synthetic content. - Promote Deepfake Awareness Training
Security awareness programs must now include education on synthetic media. Train employees to question unusual voice notes, urgent requests via new channels, or inconsistencies in communication styles. Real-world simulations and exposure to AI-generated content can help staff build a mental model of what deception looks—and sounds—like today. - Implement Multi-Channel Verification
Encourage “trust but verify” practices across departments. Voice request from an exec? Confirm via Slack, Teams, or text. Embedding verification steps into standard workflows—for example, requiring second-channel confirmation for financial approvals—can prevent split-second decisions made under pressure. - Monitor for Executive Impersonation Attempts
Tools that track and detect impersonation of known individuals—especially high-risk personas like CFOs or IT admins—are key to stopping targeted spear-phishing attempts. Continuous monitoring of email metadata, communication cadence, and behavioral fingerprints can reveal subtle signs that an identity has been faked or hijacked.
The Road Ahead
Deepfakes represent the next phase of phishing. As attackers become more sophisticated, the response can’t be static. Cybersecurity leaders must understand that relying on traditional defenses like SEGs or static filters is no longer enough. The key to resilience lies in adaptive security, educated users, and an AI-augmented workforce.
The threat may be synthetic, but the damage is very real. It’s time to treat deepfake risk as a core part of your email security strategy.
Explore real-world examples, detection strategies, and evolving threats on our Deepfake Learning Page.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)