Table of Contents
Earlier this year, FireEye reported that 86% of phishing attacks observed in Q2 did not contain malware. Subsequently, the annual Verizon Data Breach and Incident Response (DBIR) report concluded that nearly 70% of all phishing attacks now lack a malicious payload, such as a link or attachment.
These reports square with what IRONSCALES researchers have witnessed firsthand for at least the past 18 months. That is, the overwhelming majority of email phishing attacks are now driven by social engineering messages aimed at prompting an action, and distributed via advanced phishing techniques such as business email compromise (BEC), VIP/CEO impersonation and other forms of email spoofing and fraud.
From an attackers perspective, the transition from spear-phishing emails packed with malicious payloads to social engineering was a no brainer.
That’s because, as we’ve written about before, the most commonly deployed secure email gateways, such as Microsoft Advanced Threat Protection (ATP), Mimecast, Proofpoint and others, were not built to analyze the language within an email and decipher a message’s context and intent.
Advanced phishing attacks bypass leading SEGs at nearly 50% clip
In Q3 2020, IRONSCALES researchers turned to Emulator, our recently launched next-generation breach and attack simulation tool, to learn more about how Microsoft ATP and other commonly used SEGs are faring against modern phishing attacks.
Syndicating real-world phishing attack emulations allowed us to test technical controls and review any gaps within our customers email security infrastructure. Based on current threats, we exposed holes at the SEG level with unmodified attacks taken straight from the wild in real-time.
Over three months, we emulated 162 emulations against the top five SEGs, equating to 16,200 malicious messages sent.
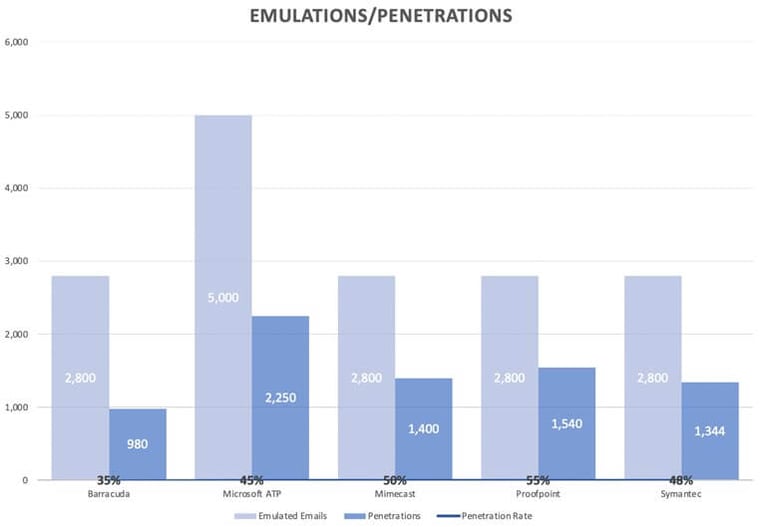
In total, our phishing emulations revealed a penetration rate of 47%. In other words, 7,614 emails bypassed the SEG and landed inside the inbox. Interestingly, both Proofpoint and Mimecast incurred a greater penetration rate than Microsoft ATP.
The below chart represents a breakdown of the penetration rates per SEG:
Social engineering phishing techniques have highest penetration rates
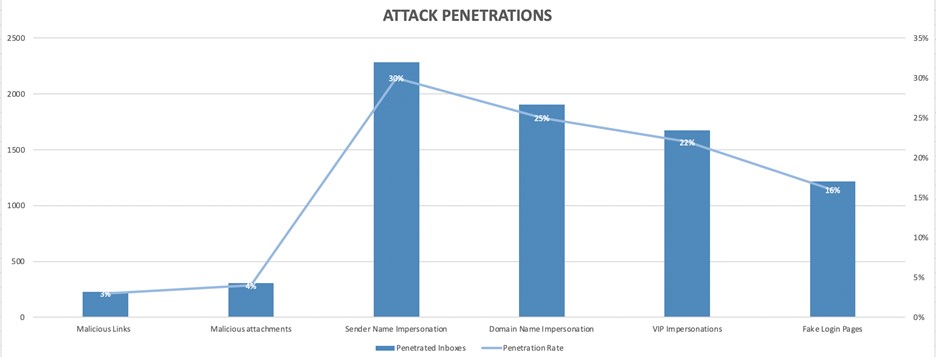
As expected, the SEGs were mostly successful at thwarting phishing emulations containing malicious payloads. Emulations with links had a penetration rate of only 3%, while those with attachments had a penetration rate of just 4%.
The phishing attack technique with the greatest penetration rate was sender name impersonations, which occur when an email masquerades as coming from a trusted source, such as a colleague, friend or family member. Sender name impersonations accounted for 30% of all SEG penetrations, which represents a 6% increase from our 2019 analysis.
Domain name impersonations, which occurs when an email is from a similar domain, in which attackers register the domain to set the right authentication records in the DNS, accounted for 25% of penetrations. This represents a 23% increase from our 2019 research.
VIP impersonations, such as CEO spoofs, and fake login pages came in at 22% and 16%, respectively. The below chart represents a breakdown of the penetration rates per attack technique:
The inability to discover, analyze and immediately respond to the majority of social engineering emails is just one of many reasons as to why thousands of organizations around the world have chosen to supplement their SEGs with IRONSCALES.
Our mailbox-level self-learning email security platform is purposefully built using AI, natural language understanding, computer vision and machine learning to help stop the types of advanced phishing attacks that Microsoft ATP and other leading SEGs cannot.
For more information, check out our phishing simulation training
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)









.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)





