Table of Contents
A recent report from Gartner showed worldwide IT spending is expected to reach $3.5 trillion this year, a 7.3% drop from 2019 due to COVID-19 – and yet it’s more important than ever for companies to protect their employees from malicious social engineering and business email compromise (BEC) attacks, which have seen a considerable uptick since the pandemic began, according to Microsoft.
Earlier this year I wrote about the concept of inattentional blindness, a psychological phenomenon in which people fail to perceive an unexpected change even when it’s in plain sight. While attackers have always sought to expose human vulnerabilities such as inattentional blindness, COVID-19 has accelerated social engineering attacks designed to deceive targets into taking an action.
A new phishing attack aims to exploit inattentional blindness and anti-phishing logo detection technology at the same time.
How It Works: A new phishing attack exploits remote workers
In early July, IRONSCALES first uncovered a series novel social engineering attacks built to avoid both human controls and image detection anti-phishing defenses. These attacks spoofed a variety of popular business applications including:
- Microsoft Office 365
- Microsoft One Drive
- Microsoft SharePoint
- Adobe
- DocuSign
What makes this social engineering campaign different from the many others that have targeted these brands is that they are not just focused on beating human training or email protection technology – but both simultaneously. Because there are no malicious links or attachments, the sender and message both pass all email defenses, such as DMARC, secure email gateways and spam filters. Once the threat actors bypass the most common email security controls, all that’s left is to defeat the human element – getting users to enter their credentials.
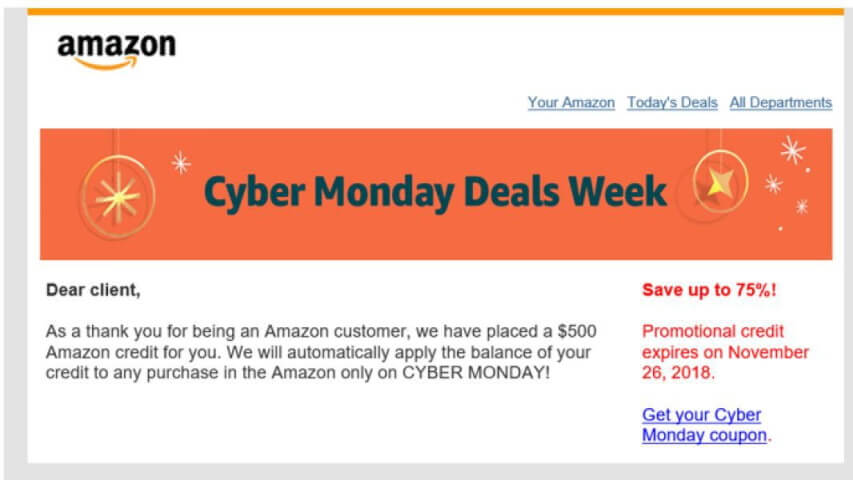
To do so, as you can see below in Figures 1 and 2, the cybercriminals have developed a fake login page that actually looks identical to a real login page except that the brand logo appears to not load. Whereas a lot of times fake login pages have somewhat obvious identifiers (blurred or resized images), the only abnormal feature on this login page, when compared to a legitimate one, is that the logo appears as if it is unable to load. When in reality, this image is intentionally embedded the way it is to help beat both logo detection technology and human controls.
For remote workers constantly dealing with bandwidth issues, an unloaded or slow to load logo likely doesn’t rise to an elevated level of suspicion. If anything, it’s just another example of inattentional blindness.
Figure 1
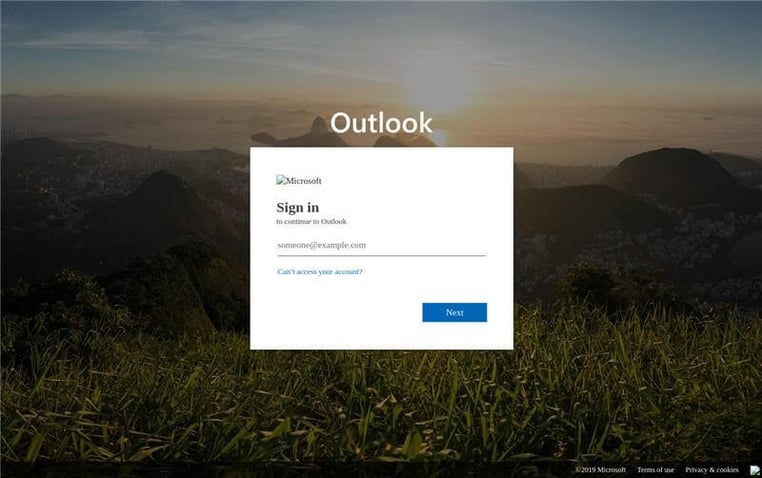
Figure 2
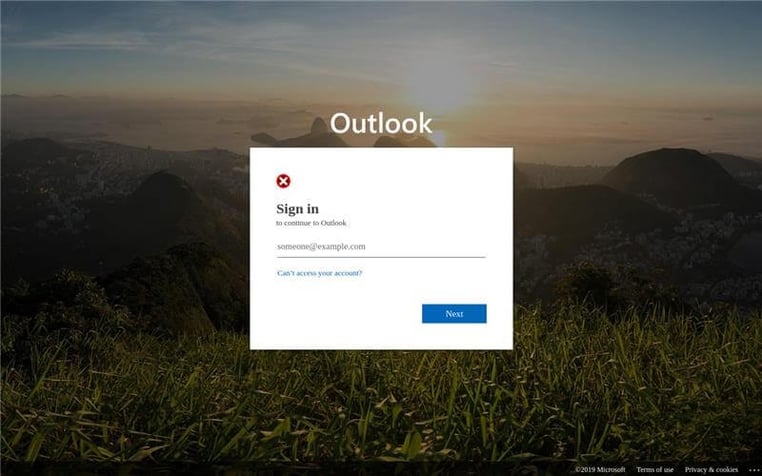
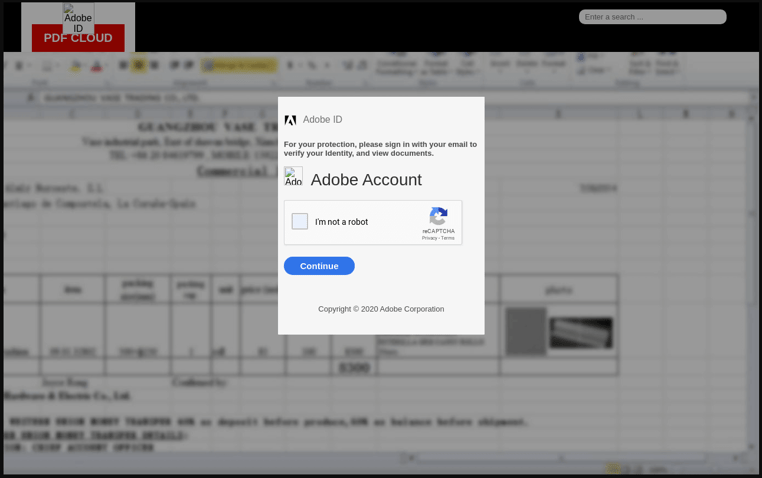
Another wrinkle: Captchas add unfounded legitimacy
Some of these attacks add another layer to make them even more believable: captcha forms when users first click on a fake login URL (see Figure 3). This gives additional authenticity to the process as captchas are mistakenly believed to only belong to authentic web pages, when in fact they are simply an added security layer to prevent bots from accessing a form or page. In this scenario, this is a clever way for the cybercriminals to enhance the experience to seem “normal” and secure.
Some captchas even asked users to checkmark similar images (as in “select all the images with chimneys”), a more sophisticated version of captcha than “I’m not a robot,” adding even greater purported legitimacy to the fake login pages.
Figure 3
What’s the motivation for this phishing attack?
As usual, the end goal for these phishing attacks is credential theft. Once employees enter their usernames and passwords, attackers have the information they need to login to a real account and commence with illegal activity, such as account takeover, which could ultimately lead to credit card fraud, data extraction, ransomware and more.
Fortunately, the IRONSCALES self-learning email security platform automatically detected and marked each email as fraudulent leveraging computer vision and natural language processing. The platform is designed to identify phishing attacks with links to fake login pages even when such messages appear as legitimate to other legacy email security controls.
Reducing risk from visual similarity attacks
Traditional signature-based email gateway security solutions are challenged to stop these types of sophisticated social engineering attacks as they were designed to scan the source code that lays behind the HTML page in order to match the signatures of previously known attacks. That, coupled with inadequate phishing awareness training, are among the most common reasons that these attacks breach defenses and are successful.
To learn more about how IRONSCALES self-learning email security platform provides mailbox-level BEC protection & visual anomaly detection click here.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)













.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)