Table of Contents
We recently published a report named “The Business Cost of Phishing” that provides insights into the challenges faced by IT and Security teams in their fight against this highly prevalent type of cyber-attack.
We divided the report into three key sections:
- The Threat of Phishing: We asked respondents about the prevalence and types of phishing attacks in their respective organizations.
- The Cost of Phishing: Organizational phishing attacks are on the rise and it's costing organizations more than ever to fight back. This report provides insight into the amount of time spent at the team level, as well as estimating the cost incurred for each individual phish.
- The Outlook for Phishing: We surveyed our respondents to find out what they think will happen with the phishing problem in 12 months.
In this blog, we’ll discuss the results of “The Threat of Phishing” portion of the report
Organizational data, finances, and reputation can be lost to phishing. Our recent study found that one-third of organizations feel as though they are facing a significant threat from this type of attack on their organization's information assets. Some of these specific threats include:
- Loss of account credentials: Popular brands like Microsoft, Amazon, and Apple are often used in phishing scams that request users check their accounts for irregular activity. The malicious link in this phishing email takes the victim to a fake website that allows the bad guys to steal user account credentials, which gives them full access and privileges to their victim’s account.
The sophistication of phishing attacks is increasing, and they're increasingly able to bypass multi-factor authentication (MFA) protection. - Tricking users into paying fake invoices or diverting payroll: The use of targeted spear phishing emails to trick employees into authorizing fake invoices or changing payroll details is a common technique used by Business Email Compromise (BEC) attacks.
- Compromise of corporate data: Phishing emails that install malware can result in the theft of sensitive information, as can messages that compromise account credentials. Phishers gain corporate data, triggering data breach notification procedures, the risk of identity theft for customers, loss of customer trust, and reputational damage.
 Our research revealed that 80% of respondents felt that the various dynamics of phishing attacks had gotten worse or remained unchanged over the past year. This creates a serious challenge when trying to use legacy email security technologies to stop this ever-evolving, never-ending type of attack.
Our research revealed that 80% of respondents felt that the various dynamics of phishing attacks had gotten worse or remained unchanged over the past year. This creates a serious challenge when trying to use legacy email security technologies to stop this ever-evolving, never-ending type of attack.
The three most highly concerning characteristics reported were:
- Use of adaptive techniques by threat actors to create unique attributes for each phishing message: Adaptive techniques, also known as polymorphic attacks, vary each phishing message slightly as a method of increasing sophistication and decreasing the likelihood of being detected as a phishing message. Polymorphic attacks create unique messages that must be evaluated one by one, rather than being able to match using signatures or other known or trained identifiers. The use of polymorphic attack methods is ranked as the issue of the highest concern.
- Use of compromised account credentials by threat actors to hijack current email threads to send phishing threats Account credentials obtained from an earlier phishing message—or purchased on the dark web—are then used to spread subsequent phishing messages on current email threads. This is a sophisticated attack since social dynamics in the thread are already established, assuring a level of interpersonal trust and rapport that is more difficult to create between unknown parties. It is also likely to bypass detection since the messages are sent from the organization’s own email infrastructure, removing many threat signals that can be evaluated when messages originate externally.
- Use of advanced obfuscation techniques by threat actors to hide phishing threats A related method of increasing sophistication and decreasing the likelihood of being detected is advanced obfuscation, where payload and link threats are nested, initially presented as benign, or subsequently downloaded. Phishing defenses must then evaluate messages for threat signals at multiple points in the lifecycle of the message.
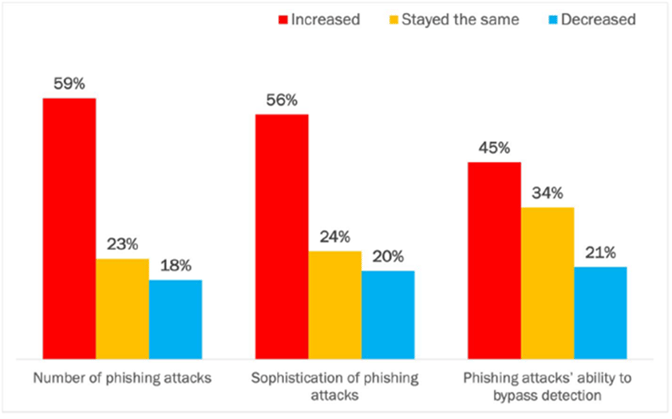
Attacks are getting more sophisticated
In addition to the key concerns listed above, the survey revealed evidence of the growing sophistication of attacks and the ability to bypass legacy secure email gateway technologies:
- Phishing in tools other than email—rendering detection capabilities focused solely on the email channel as ineffective. Examples include text messages, collaboration platforms, and messaging tools.
- Internal phishing using compromised accounts—which decreases the detection likelihood since messages are coming from a legitimate company email address.
- Leveraging current themes in news media and government announcements— thereby increasing sophistication and the temptation for a targeted victim to open the message, attachments, and any links.
The threat of phishing remains a serious concern across organizations of all sizes, industries, and locations. IT and Security teams admit that they are struggling to keep up with the tsunami of high quantity and quickly adaptive phishing techniques employed by threat actors.
In our next blog post, we will discuss what our respondents said phishing attacks were costing their organizations from a time and money perspective.
Download your copy of the Business Cost of Phishing report today!
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)













.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)