Table of Contents
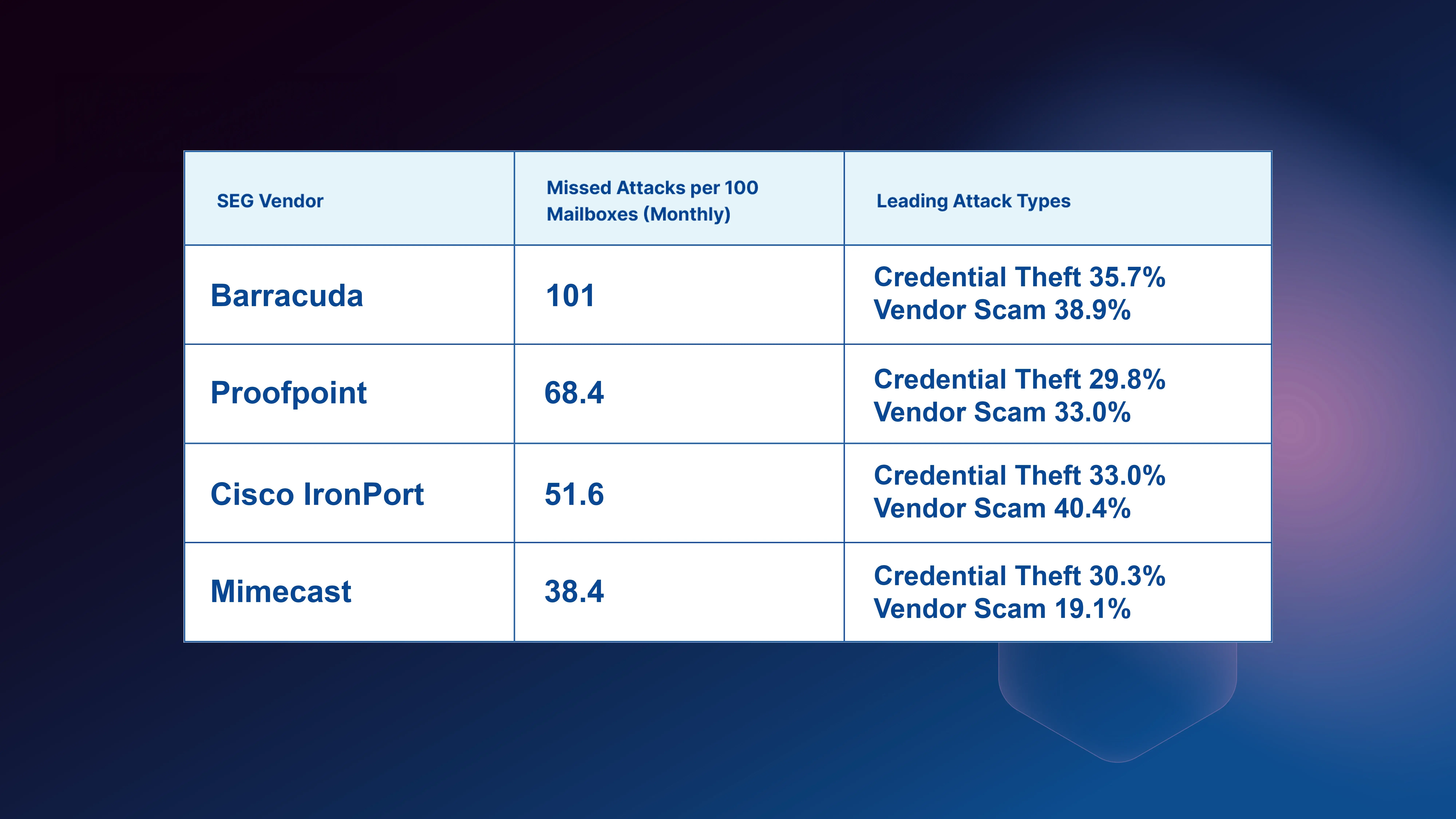
Attack Summary
- Attack Description: FileShare Platform Credential Theft
- Impacted Mailboxes: 210
- Number of Impacted Customers: 42
- Security Bypass: SPF, DMARC, Third-Party Visual Scanners
- Payload: Malicious Link
- Technique: Social Engineering
Attack Background
Legitimate filesharing services have increasingly become the vehicle of large-scale phishing attacks. This is because of their positive reputation with users and their ability to host malicious payloads while bypassing visual scanners.
Attack Details
In this attack, the perpetrators utilize a compromised email address to send a credential theft malicious email. The attack starts by a sender name field manipulation, in which the recipient receives an email form “Accounts Receivable” – some impersonation of a vendor’s financial team. Next, they are notified that they have received a fax and are directed to review the document in the attached “pdf” file below. Finally, once engaged, they fall for the trap and are taken to the payload.
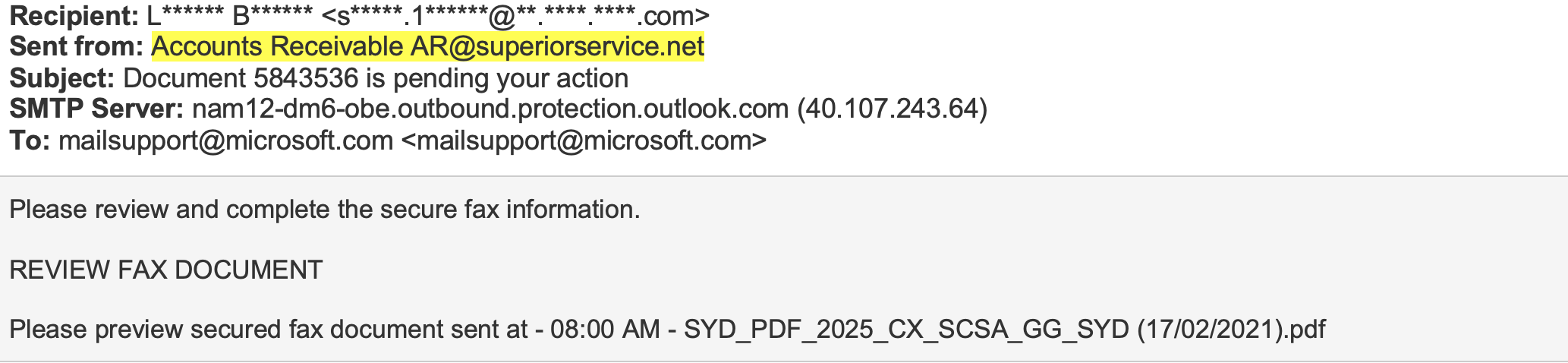 Payload:
Payload:
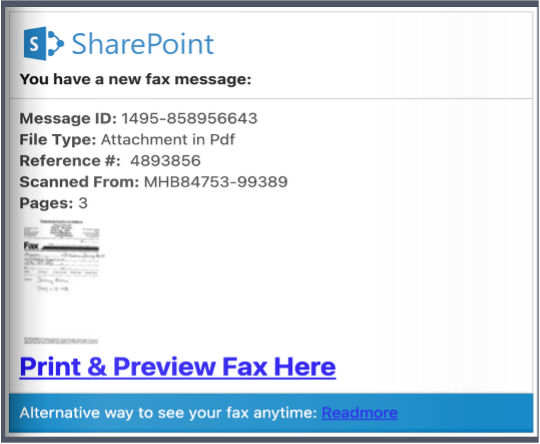
.png?width=540&name=share%20point%20%20print%20%26%20preview%20fax%20screenshot%20(1).png) The payload of this attack starts with a redirection to a flipstack webpage – a platform designed for publishers to host magazines and other content. Here the attackers abuse the platform to host a “SharePoint” file that appears to be a financial document. In the screenshot for “Print & Preview Fax Here” you can see that there is an embedded link that redirects the malicious payload.
The payload of this attack starts with a redirection to a flipstack webpage – a platform designed for publishers to host magazines and other content. Here the attackers abuse the platform to host a “SharePoint” file that appears to be a financial document. In the screenshot for “Print & Preview Fax Here” you can see that there is an embedded link that redirects the malicious payload.
The malicious payload is a credential theft landing page that impersonates an Adobe Cloud document. To access the document, the recipient is asked to input their Microsoft account credentials, and in doing so, the credentials will be stolen and hijacked by the attackers. The payload itself is dangerous and such attacks often lead to ATO (account takeover), a popular method uses by threat actors in targeted phishing attacks.
.png?width=592&name=adobe%20cloud%20login%20screenshot%20(1).png) Email Security Bypass:
Email Security Bypass:
This attack circumvented standard email security measures, such as authentication protocols (SPF and DMARC) and visual scanners, via sending the email from a compromised email address and hosting the payload on a legitimate-high-reputation platform. By doing so, such measures, of which are designed to recognize behavioral anomalies and low reputation entities, are not well equipped to perform scanning and recognizing intent.
IRONSCALES Detection:
IRONSCALES was able to detect this attack at the mailbox level with the help of our AI named Themis. She identified the attack using behavioral analysis and with input from our users (the Community).
What to Look For:
As with all cyber security attacks, some important steps that an individual can take are: awareness and attention-to-detail. Know that such attacks are there and learn what to look for. Furthermore this particular attack demonstrates that oftentimes an attack may appear to be legitimate and is able to bypass security tools like a SEG, authentication protocols and visual scanners.
To learn more about IRONSCALES’ award-winning anti-phishing solution, please sign up for a demo today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)








.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)