Table of Contents
With workforces largely remaining partially or fully remote, employees continue to rely on tools for greater efficiency and productivity. While we all know that software like Slack and Zoom have emerged in popularity in recent months, there are other technologies - both new and old - that have proven invaluable to employee’s as they ride out COVID-19 working from home.
One of those tools is the Private Branch Exchange (PBX), a legacy technology which enables voice message recordings to be sent directly to an employee’s inbox. As workers have little to no access to office land lines, PBX enables employees to retrieve important messages through integration with a company’s email client. Simply put - if an employee misses a call, then they instantly receive a recording or message in their inbox.
While this configuration has made it easier to connect and work from anywhere, it has also allowed cybercriminals to find another way to phish workers. That’s completely unsurprising: if we know anything about hackers, is that there is no current event that is out-of-bounds to try and exploit.
The voicemail email phishing scam taking on the world
In mid-May, IRONSCALES uncovered what has since evolved into a massive, global phishing trend in which attackers use custom subject lines to spoof the voicemail email as if it is coming from a PBX integration. As you can see in Figure 1 below, the cybercriminals are using very targeted subject lines that often include a company name or recipient’s name, a proven tactic to trick employee’s into believing that an email is legitimate.
Figure 1
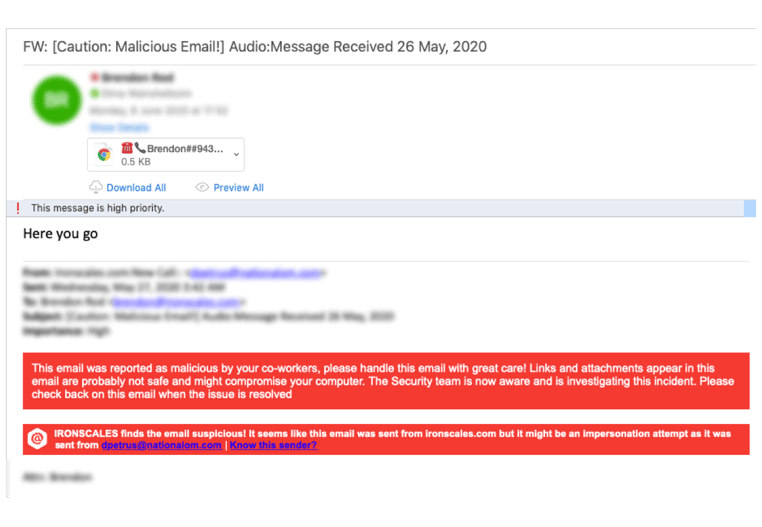 In total, the voicemail phishing or “vishing” scam has threatened almost 100,000 mailboxes worldwide, targeting hundreds of enterprises across all industries, including real estate, oil & gas, engineering, IT, healthcare, financial services and more.
In total, the voicemail phishing or “vishing” scam has threatened almost 100,000 mailboxes worldwide, targeting hundreds of enterprises across all industries, including real estate, oil & gas, engineering, IT, healthcare, financial services and more.
Fortunately, IRONSCALES self-learning platform automatically detected and marked each email as fraudulent email attachment scanner, leveraging computer vision designed specifically to look for fake O365 sign in pages and other inside html/html files.
What’s the motivation for this phishing attack?
It may seem odd for attackers to create phishing websites spoofing PBX integrations as most voicemails are quite benign in the information shared. However, attackers know that the credentials could be used for multiple other logins, including for websites with valuable PII or business information. In addition, any sensitive information that is left in the voicemail could potentially be used for a social engineering attack.
While the body of the emails is light (See Figure 2), the highly personalized subject lines prey on people’s curiosity as they seek to answer missed calls from their vacated offices.
To make each attack more believable, cybercriminals are adding customization to personalize the sender name as well. This type of sophistication partially explains why these email attacks are bypassing secure email gateways and the DMARC authentication protocol, as neither are designed to detect or respond to spoofed emails without a malicious payload.
Figure 2
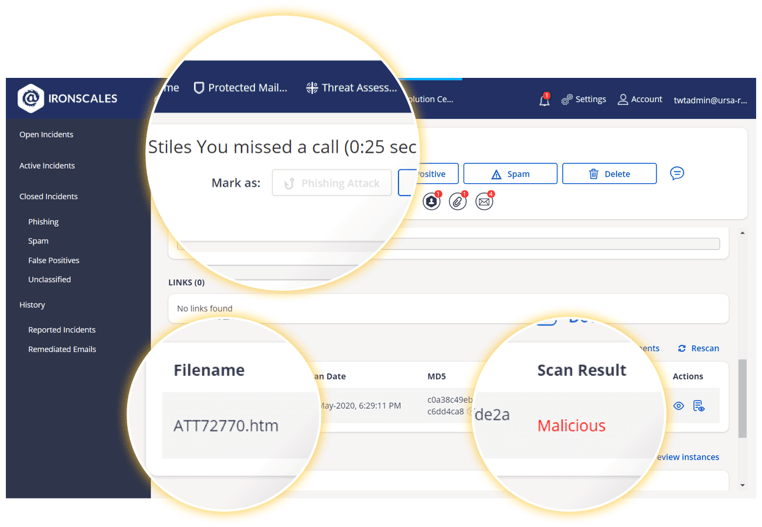 Figure 3
Figure 3
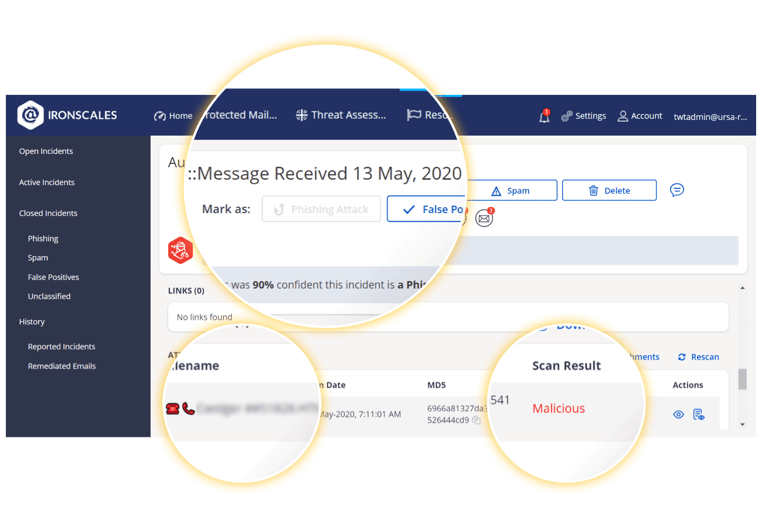
Reducing risk from vishing
If your organization automatically sends voicemails to workers inboxes, then your company is at risk of falling victim to this scam. As we know, if an email looks real then someone will fall for it. A couple of steps you can take to reduce risk:
- Inform your employees and make them aware of such a trend. Make it top of mind for them so that they can catch such abnormalities.
- Invest in technologies can that detect such sophisticated phishing scams. In both the examples above, a computer vision-based scanner was able to detect the nature of these emails and mark it automatically as phishing.
To learn more about how IRONSCALES self-learning email security platform provides mailbox-level BEC protection & anomaly detection, click here .
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)


