Table of Contents
Picture this: Accounts Payable gets a “new remittance instructions” email from a frequent supplier. The sender name is right, the thread is a real PO reply‑chain, and the tone mirrors past messages. A shift supervisor is warning about line‑down risk. It looks safe because it feels familiar.
Believability comes from context: trusted names and domains, realistic timing, real subject lines, and language lifted from prior exchanges. That’s why the inbox is where supply‑chain attacks slip through—and where defenses need the most context.
Why Attackers Love Your Supply Chain
Manufacturing runs on trusted email: POs, invoices, shipment notices, drawing reviews. Attackers know it. Sector‑specific reporting shows just how often the first step is social engineering, not malware.
Over the last year, manufacturing breaches were driven by system intrusion, social engineering, and basic web attacks in the majority of confirmed cases, with ransomware present in nearly half. Stolen credentials factored into a third of incidents, and third‑party involvement in breaches across industries doubled to ~30%, putting suppliers and logistics in the blast radius.
Response windows are shrinking too—eCrime breakout times now average under an hour, with the fastest measured in seconds. And when things go wrong, the average breach now runs in the multimillion dollars.
Translation: If an attacker can nudge one payment, hijack one reply‑chain, or swap one drawing link, they can choke a line without ever dropping a payload.
The graphic below was created by Viswanath Chirravuri, the Software Security Director at Thales, to cover the attack chain for manufacturing-focused attacks. This is a great depiction of how attackers target something susceptible within a third-party supplier (like a network, web application, or hardware), and exploit these organizations.
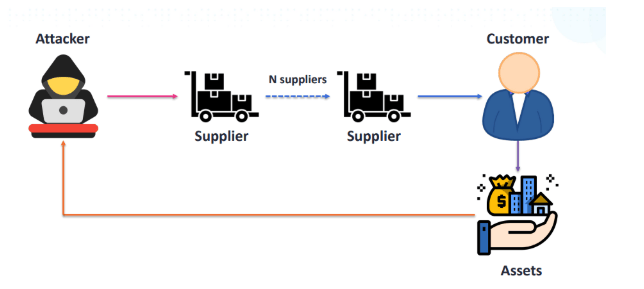
The Real Problem is Not Email. It’s Assumptions.
We trust familiar names, known domains, and routine workflows. But modern supplier fraud and BEC skip obvious telltales. No malware. No dodgy zip. Just a “can you rush this?” that mimics your actual language, timing, and approval chains.
On the plant floor, seconds matter. In the inbox, context matters more.
How Manufacturers Can Secure the Supply Chain
Our solution focuses detection and response inside the mailbox, where decisions happen (AP@, buyers@, engineering@). Our Adaptive AI combines relationship context, reply‑chain history, behavior patterns, and analyst feedback to spot and stop believable scams.
Here’s what changes when you put detection and remediation where the work is:
1) A social graph of your supply chain, not the internet
We baseline your buyer–supplier–logistics patterns to learn who talks to whom, about what, and when. From there we flag:
- First‑time bank changes on invoices from a vendor who never changes banks.
- New or mismatched reply‑to domains (the classic vendor‑lookalike trap).
- Anomalous payment timing and out‑of‑cycle requests masked as “urgent line‑down.”
These are the email equivalents of a loose bolt on the assembly—easy to miss until the machine shakes.
2) Catch the pretext, not just the payload
BEC/VEC lures are payload‑less on purpose. We combine language intent analysis with that relationship graph to surface messages that sound like your vendor…but don’t behave like them. Think: tooling deposit asks, freight reroutes, quote/PO tampering, or hijacked reply‑chains where the only thing that changed is the bank number.
3) Autopilot when seconds count
Once one variant is confirmed, we cluster and automatically remove every copy across the tenant—shared mailboxes included—so you’re not playing email whack‑a‑mole while parts are in transit. Our agentic AI assistant, Themis, handles triage, escalation, and quarantine based on your preferences—hands‑off when you want it, hands‑on when you don’t.
4) Protection that fits how engineers work
Email isn’t just AP; it’s CAD/BOM/ECO collaboration with contract manufacturers and tooling vendors. We apply identity and intent analysis to drawing reviews and change‑notice threads, with time‑of‑click checks for late‑clickers and account‑takeover signals (weird inbox rules, risky OAuth, impossible travel) that often precede IP theft or ransomware pivots.
5) Harden your own identity (quietly)
Supplier trust starts with your domain. Built-in checks, plus optional DMARC/SPF/DKIM management, help stop brand spoofing without a side quest in DNS wizardry. Record flattening, guided onboarding, and health monitoring keep deliverability steady while you ratchet up enforcement.
What Good Looks Like in Practice
- A first‑time bank‑change request on an invoice from a vendor who never changes banks triggers an inline warning and a guided verification workflow.
- A reply‑chain hijack with a subtle domain shift (vendor‑name.co → vendor‑name.com‑billing) is flagged for mismatched reply‑to and relationship anomalies; copies are clustered and removed across shared mailboxes.
- An engineering change notice that inserts a new file‑share link mid‑thread is checked at time‑of‑click; suspicious OAuth scopes or inbox‑rule changes on the sender account trigger account‑takeover remediation.
- A freight reroute request outside normal hours pings as out‑of‑cycle for that lane and contact; Themis opens a case, notifies the buyer, and quarantines similar messages.
Outcome: Your end users keep moving, and fraud doesn’t.
What This Means For Your Plants and Partners
- Fewer stoppages. You prevent the email‑to‑ransomware and vendor‑fraud pivots that derail schedules.
- Cleaner audits. Identity anomalies and bank changes are flagged, explained, and remediated in seconds.
- Operationally light. Fast start with native integrations and policy-light controls.
- People included. Dynamic banners, a one‑click report button, and targeted phishing simulations train the exact users who touch money and drawings—without slowing them down.
A simple way to start
Pick three flows that keep you up at night—bank changes, reply‑chain hijacks, and drawing reviews. We’ll baseline those relationships, start guidance in the inbox, and automate tenant‑wide remediation for anything that even rhymes with fraud.
Because the real supply chain isn’t trucks and pallets. It’s trust in motion.
Why IRONSCALES for Manufacturers
- Inbox-level protection that reads context, not just content.
- Fast setup. Automated, tenant‑wide remediation.
- AI + Human insights (your users, our community) catch the intent‑based attacks others miss.
- Unified platform with awareness training, simulations, and DMARC management to strengthen both identity and behavior.
Ready to secure the links that matter—AP, buyers, engineering, suppliers—without slowing the line?
Want to Learn More?
Visit our Manufacturing Industry Page to discover how we're helping secure the supply chain. Or reach out to one of our experts to find out how we can help secure your organization's inboxes.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)




