Table of Contents
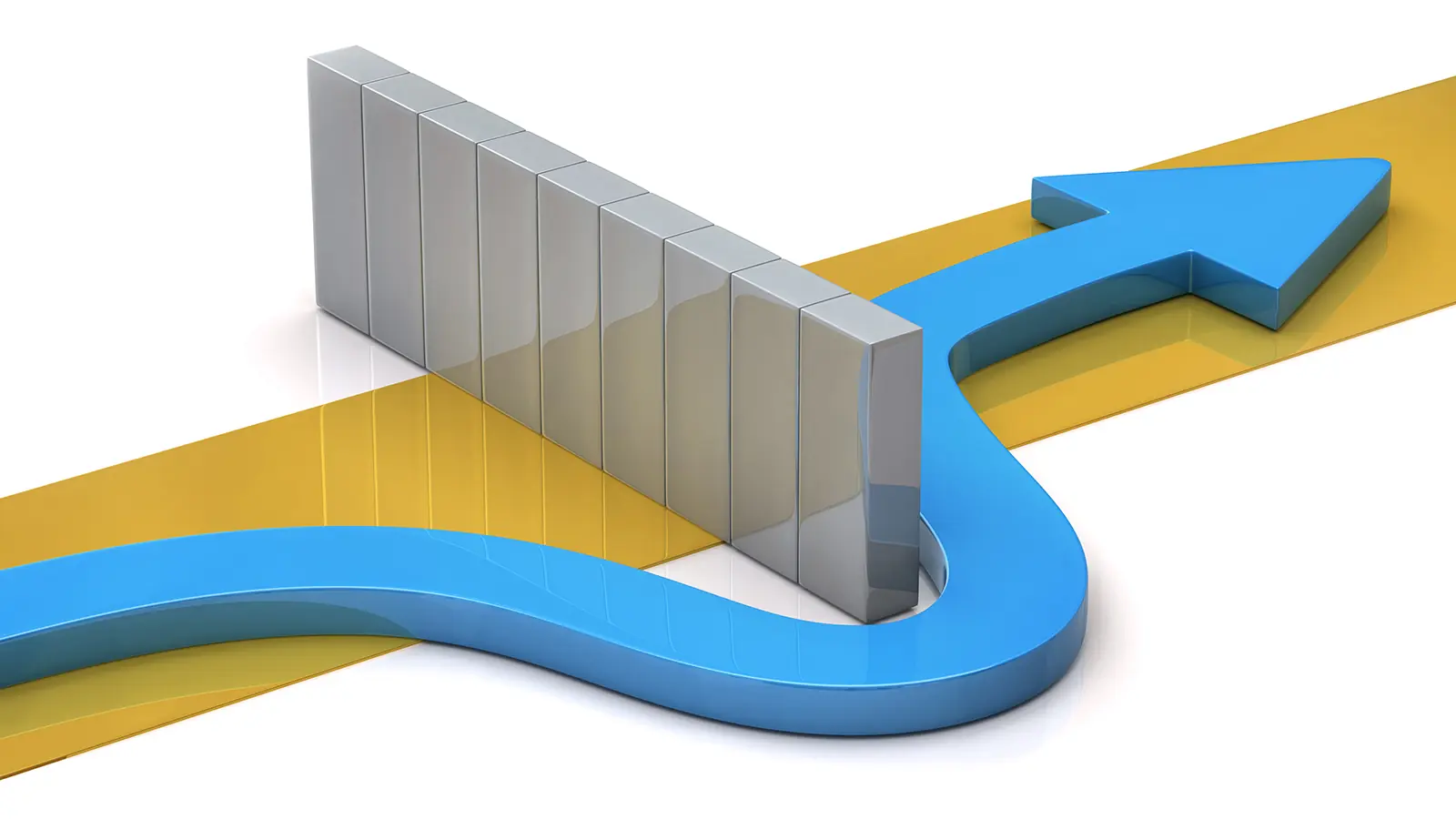
For organizations dealing with phishing attacks, it may seem like an easy solution to stopping the attacks is just to block the attacker. Turns out that isn’t the case. Let’s look at why this approach actually creates more work for your already overburdened security team.
Blocking an attacker results in them receiving a bounce back or undeliverable message when they attempt to phish your newly blocked domain. This lets the attacker know to stop targeting that domain and create a new one to target you with. This creates an ongoing, never-ending cycle of blocking, new attack, blocking, new attack, etc.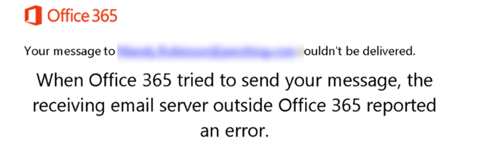
Let's look at an example to understand this in a bit more detail. I'm an attacker. I'll spam/phish your domain using spam@spammer.xyz. You decide to block the spamming domain spammer.xyz. Now suddenly, I (the attacker) get NDRs/ Bounce Backs. These “Non-Delivery Receipt” (NDRs)/Bounce Back messages will be my signal to now change my domain and start spamming you with spam@newdomainforyoutoblock.xyz. You block this "newdomainforyoutoblock.xyz." The same cycle continues on and on, ending in no actual protection from the attacker.
We think there’s a better way. To ensure you are not helping the attacker and preventing this block cycle from starting, our platform can create incidents to notate the attacker is targeting your organization, but the attacker does not get notified or become aware that we have discovered their attack.
For example, I'm an attacker. I'll spam/phish you using spam@spammer.xyz. IRONSCALES identifies the attack and creates an incident and automatically quarantines this message across all of your company’s inboxes. I (the attacker) will not receive an NDR/Bounce Back. I have no clue if my message reached you or not. So, I'll keep spamming you. However, IRONSCALES just keeps clustering my messages to the same incident you created the first time, and you don't have to take any action.
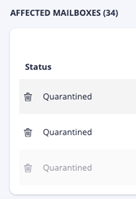
The benefits of not having a blocklist are evident. IRONSCALES helps security teams by clustering incidents from the same attacker, so the security team knows what the attacker is doing. However, the attacker has no idea we are onto them.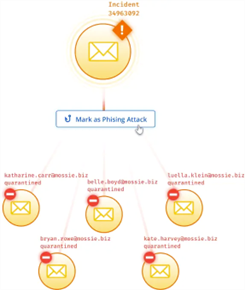
Using this technique gives your security team the upper hand when it comes to both common and advanced attackers. It’s a win-win!
We invite you to download our new report "The Business Cost of Phishing", where you can discover the true cost of phishing on organizations as well as what IT and Security professionals believe is coming next. You can get the report at https://secure.ironscales.com/the-business-cost-of-phishing/report-download
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)








.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)





