Table of Contents
“I know I hear you talk about this all the time, but what is ransomware exactly?” my wife asked as we watched the evening news. Apart from being a great question, it’s one that a lot of folks have been pondering lately. And so, in this this blog we will demystify and define the phenomenon. We will discuss its history, how the term grew to be so common, and offer some ideas of what the future might hold as ransomware evolves.
Before we dive deep into explaining the technology, it is important to understand some basic facts and dispel a myth or two. Ransomware may be featured in the news more frequently these days, but it has been around at least 30 years. It is a common misconception that ransomware is fairly new, or that cryptocurrencies are now enabling something that was previously impossible. These assertions are simply inaccurate.
The first major recorded instance of ransomware was the PC Cyborg Trojan in 1989, which would hide directories and encrypt file names on a computer. To reverse the damage, users had to mail $189 cash to a post office box in Panama. This type of attack is not new and unfortunately has evolved over the years — from cash in an envelope to methods like e-gold, direct cash transfer through services like Western Union or MoneyGram, or today’s cryptocurrency.
Let’s take a step back from the headlines and try to break down this basic concept very simply. We start with the concept of software, a collection of instructions (aka “code”) and data that tells a computer how to work. Next, there is software with malicious intent, i.e., software intentionally designed to cause damage to a computer, server, computer network, mobile devices, etc. Malicious software is commonly referred by its portmanteau, “malware.” There are many different varieties of malware, classified generally based on the intended result. These include viruses, worms, spyware, adware, scareware, and the focus our discussion, ransomware.
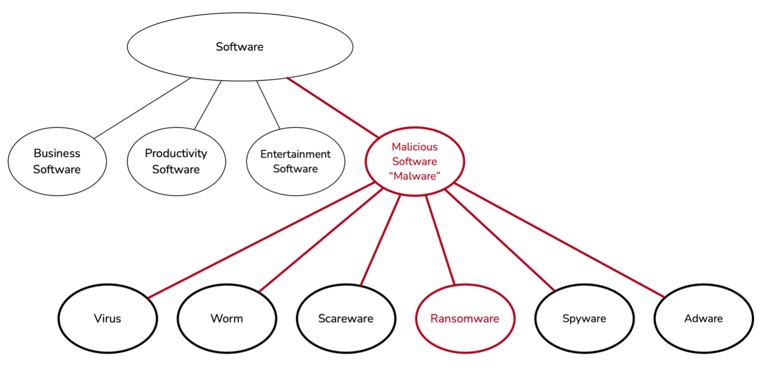
Now let’s return to our original question: what is ransomware? In simple terms, ransomware is a specific type of malicious software that takes data it finds on a device or a set of devices, processes that data with an algorithm, and changes its structure so it is no longer recognizable or usable. The process is called encryption, it is the same basic underlying technology concept that secures almost everything you interact with on the internet.
Ever purchased something on Amazon? That traffic was encrypted with a technology called Transport Layer Security (TLS) to keep your purchases safe. The hard drive on your work computer was likely encrypted before it was handed to you or was taken back at some point because it needed to be encrypted.
Encryption isn’t inherently malicious; it is simply a tool that evolved from the practice of cryptography. But because modern cryptography is so strong, trying to break it can take huge amounts of time — sometimes years. The good news is that with most encryption algorithms, including those used by ransomware, there are other algorithms to reverse the encryption, known as decryption algorithms.
Decryption restores the data to its previous state, as if was never touched in the first place, by using a key. Depending on the type of encryption used, more than one key could be necessary. A key is usually a long string of text that allows the decryption process to run properly. Think of it as a missing jigsaw puzzle piece; without that missing piece the data will never come back together clearly or completely.
With ransomware, you have the encrypted data in your hands, and to reverse that process you need the key to decrypt the data. The ransomware attacker is effectively holding your data hostage but doesn’t need to physically remove the data. The attacker just needs to make your data inaccessible unless and until you comply with their demands.
Now that you have a better understanding of what ransomware is and how it works, let’s review how it cripples businesses at scale. To do this we need to understand two concepts common in ransomware incidents: the delivery mechanism and the payload. Using the Amazon analogy again, in this scenario the shipping service driver is the delivery mechanism, and the payload is the package being delivered. In a ransomware attack, these pieces of software are chained together to achieve a goal, and, in some cases, they are even combined into a single package.
Now, let’s go back in time to revisit the incident that made ransomware a household name: CryptoLocker. A sophisticated piece of malware that originated in 2013, CryptoLocker targeted Microsoft Windows. It spread through the delivery mechanisms of infected email attachments and what is called a botnet. When the payload activated, it would encrypt select files on the local computer and mounted network drives. The malware then made an offer to pay a ransom via prepaid cash voucher or bitcoin.
The impact of CryptoLocker isn’t fully known, but the data indicates that about a half million people were impacted by it. The impact was so great, a large group of international law enforcement agencies, cybersecurity companies, and various academic research institutions launched Operation Tovar to investigate and ultimately shut down the botnet CryptoLocker used. In short, it was a big deal and gave cybercriminals a blueprint they are still innovating on to this day.
At this point, you may be thinking, “What can I do to prevent my business from being negatively impacted by ransomware attack?” The good news is there are opportunities to develop a strategy to harden your organization’s assets and promote the proper security culture within your organization. Start as soon as possible because the absolute worst time to figure out your security strategy is during an incident.
We always recommend putting the human at the center of our strategy, which means 1) using tools that provide regular training to harden the psychology of your end users and 2) give your administrators tools that act as a force multiplier to help them detect and respond to incidents in real time. Spend some time studying the standard attack patterns and you’ll soon discover that the person is the new endpoint and social engineering is on the rise. This means, as important as putting tools in place is (and it really is), you also must invest in developing user security awareness.
The two instruments that will help reduce your risk are email security tools and a solid backup tool. There are other approaches that will help with network prevention, network isolation, server hardening, privilege reduction, and identity access management. However, email remains the number one infiltration point for attackers, the front door to your organization.
Look for an email phishing tool that will promote security awareness and perform threat mitigation. Search for a tool that can assess your organization’s risk level, educate users on the attacks, provide contextual awareness education, and give your users a way to report potential threats. This will help you accumulate actionable data and turn your users into a new layer of defense.
On the threat mitigation side, you want tools that use that valuable data for threat mitigation. You want that data directly fed into an email threat mitigation solution that uses artificial intelligence (AI) to enhance your human administrators. You want a layered defense, with AI leading a constant watch for malicious URLs, attachments, and behavioral anomalies by analyzing natural language and social interactions behaviors inside and outside your organization.
With this ability you get to take that real threat data to target simulation and awareness campaigns that you know your company is defending against. Plainly put, one of the strongest defenses against ransomware is a proactive strategy based around the combination of human and artificial intelligence that helps prevent ransomware from getting a foothold in your organization.
To learn more about IRONSCALES’ award-winning anti-phishing solution, please sign up for a demo today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)





.png)