Table of Contents
Stop me if you’ve heard this before: Phishing threats are constantly morphing at scale and the vast majority of businesses simply don’t have the time, money and resources to investigate each and every suspicious email as quickly as phishing mitigation demands. In fact, 67% of organizations take 6-20 minutes or longer to identify and remove a single phishing email, according to a survey we commissioned with Osterman Research earlier this year. This timeframe from identification to remediation is staggering when considering that employees engage with phishing emails in 82 seconds or less, according to Aberdeen.
Today, around 350,00 new malware variants are derived every day and attackers are constantly improving their tools and techniques. As a result, traditional phishing incident response approaches and secure email gateways (SEGs) are becoming powerless. That’s because such tools rely on scripts and rules, which, are no match for the volume and magnitude of email attacks. For perspective, by the time a security analyst writes a rule, it is likely already redundant, and the odds are that an employee(s) has already clicked on the phishing email.
It remains true that 90% of all cyberattacks begin with email phishing largely because attackers continue to find new ways to defeat both human and technological controls. Fortunately, IRONSCALES has pioneered a new type of email security defense that is proven to dramatically reduce risk. Welcome to the era of self-learning email security.
Why self-learning email security thrives when other anti-phishing measures falter
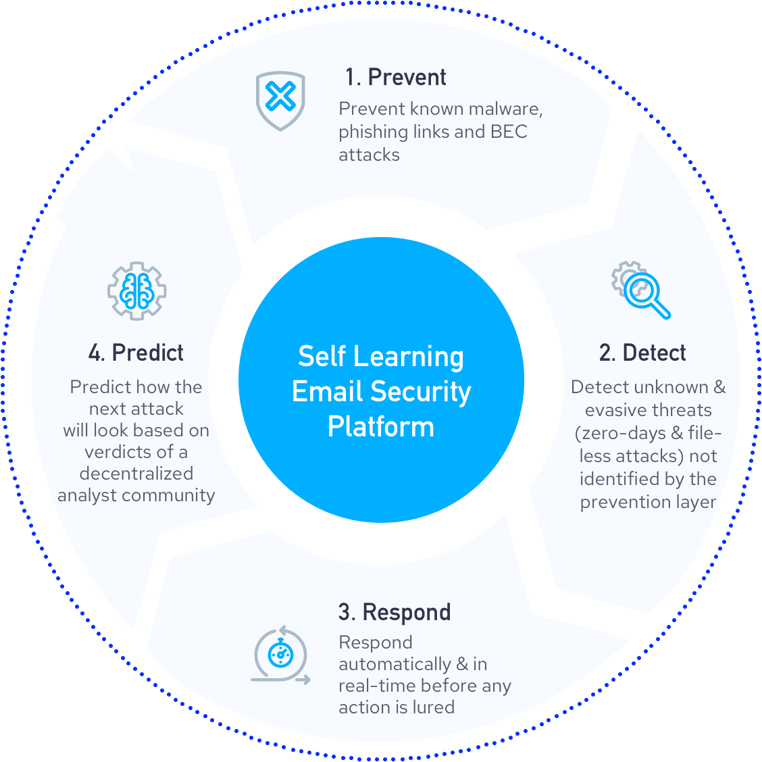
Self-learning email security technology applies a reinforced learning paradigm that blocks, monitors and responds to email phishing attacks. The blocking component acts as a filtering layer, attempting to stop attacks before they morph into major security events. The monitoring component constantly reinforces the blocking component by looking for filtering errors, which occur when an email was originally allowed to enter an inbox before subsequent layers determine that the message must be removed. The response component then informs the learning algorithms of the mistake so that such an error will never happen again.
This reinforced learning paradigm also makes it possible to predict what the next attack is likely to look like. In this scenario, prediction is possible because the model learns what phishing looks like in all its forms; thus it can project future variations with accuracy. This is important when considering that 42% of phishing attacks are polymorphic.
There are four essentials inherent to a successful self-learning email security tool. These include:
- Big Data – Accurate and recent data is essential, and machines cannot be trained on bad or biased data. On the same note, the date must be captured as close to the event(s) as possible, as fixing today’s problems cannot be reliant on yesterday’s data. The key here is to start at the individual mailbox-level (or thousands of them) and feed data into a machine learning model. When combined with meta data, it is possible for machines to learn what is good and what is bad.
- Reinforced Data – Both humans and technology need to quickly and as accurately help machines understand if they have failed so that the system can quickly be retrained on its errors. The reinforcement process of real-time data is the heart of a self-learning solution.
- Machine Learning – Drawing a clear line between good and bad emails is not easy, but if you have a good source of data then you are off to a good start. Machines help find and cluster similarities in phishing emails and known attacks at scale. This prevents broader polymorphic attacks or campaigns from going undetected and wasting security analysts time and resources, allowing automation to be applied to repetitive tasks.
- Closing the Loop – Providing machines with real-time and continuous feedback on all newly learned is a critical element for a self-learning platform. In fact, the self-learning model continuously learns from multiple sources, both internal and external and human and machine, in order to adapt and get smarter at predicting, preventing, detecting and responding to phishing attacks real-time
The IRONSCALES self-learning anti-phishing platform
Its easiest to envision the concept of self-learning email security through the prism of redundancies. That is, if one control fails to identify a malicious email, then other controls are invoked as a backstop. But how can we ensure that the layer which missed the malicious email in the first place doesn’t miss it again?
This is where machine learning, artificial intelligence and crowdsourcing come into place. When humans and machines work together, the risk of one layer failing to identify the same phishing attack on more than one occasion is greatly reduced. That’s because this layer is now learning from its counterparts - hence a self-learning email security platform.
Take a look at the flow chart below:
As you can see, IRONSCALES self-learning email security platform is comprised of different solutions to capture phishing attacks: end-user reports, advanced malware & URL protection, democratized threat protection, mailbox-level BEC protection, AI powered incident response and a virtual SOC analyst.
When an email penetrates the inbox, each of these layers analyze whether the messages appears malicious. So if Layer A misses the attack, but Layer B catches it, then Layer A learns and improves from the decision made by Layer B.
On some occasions, attacks do pass through every layer and land in the inbox. When this occurs, the last piece – the user –can mark the attack as suspicious. Upon doing so, the company’s security analyst can review the email and mark it as either:
- A phishing attack
- A false positive
- Spam
When this happens, all of the technical layers learn from the humans’ decision. This dynamic of humans learning from machines and vice versa is a large part of what makes our platform unique.
As we’ve argued before, there is no silver bullet in email security. But having a system that continuously learns based on the data that it’s fed, gives security teams a leg up against cyber attackers that are using the same technology to fire off attacks. That’s why in addition to having multiple layers, data is also a key component of a self-learning email security platform.
More information about IRONSCALES’ self-learning email security platform is available here.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.














.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)




