Table of Contents
Outbound Email Protection Explained
Outbound email protection is a security measure implemented by organizations to prevent data breaches originating from emails sent within the organization to external entities. It ensures that sensitive data, whether shared intentionally or by mistake, doesn’t fall into the wrong hands. This protection can either be driven by machine learning algorithms that learn and determine what is typical behavior for a user or by static rules, which are defined based on compliance and internal policies.
Types of Outbound Email Threats
-
Human Error: Often unintentional, human error remains a significant threat to data security. Examples include:
- Sending emails to the wrong recipient.
- Misusing Bcc function in emails.
- Attaching incorrect or sensitive files to emails.
-
Interception: Interception is the malicious act of accessing emails intentionally, commonly at these points:
- Sending Device: The device used to send the email.
- Network: While the email is in transit.
- Email Server: The server where the email is stored temporarily.
- Recipient Device: The device used to receive the email.
How Does Outbound Email Protection Work?
-
Machine Learning (ML) Techniques: Modern email security solutions utilize ML to understand normal and abnormal behaviors within an organization. When an irregular activity or potential mistake is detected, the system can intervene, often triggering warning pop-ups or blocking the email.
-
Data-Loss Prevention Policies: These are predefined rules that specify what content is permitted to leave an organization. For example, certain confidential documents or specific terms might be flagged for review before being sent out. These rules can help organizations meet compliance needs, especially in regulated industries.
-
Email Encryption: By automatically encrypting emails containing sensitive content, organizations can ensure that, even if intercepted, the content remains confidential.
-
Content Scanning: Advanced systems, like Perception Point, scan 100% of email content in real-time to detect anomalies and malicious behaviors, ensuring nothing harmful or sensitive is sent out.
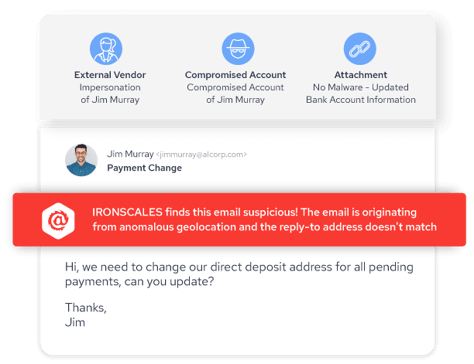
Outbound Email Protection Can Protect Against Internal Threats
Traditional email security solutions are designed to protect against external threats. However, with the rise of account takeover attacks and social engineering techniques, internal threats are more prevalent than ever. Outbound email protection ensures:
-
Protection from Account Takeover: Even if an insider’s email account is compromised, outbound protection can detect unusual sending patterns or content and halt potentially malicious emails.
-
Brand Integrity: Sending harmful or mistaken content can tarnish an organization’s reputation. Outbound protection prevents this by ensuring only safe and intended emails are sent.
-
Compliance Assurance: By monitoring outbound emails, organizations can prevent unintended sharing of regulated or sensitive information, ensuring they remain compliant with industry standards.
-
Reducing Human Error: While it's impossible to eliminate all human mistakes, outbound email protection serves as a safety net, catching most unintentional errors before they cause harm.
In conclusion, with the constantly evolving landscape of cyber threats and the ever-present human factor, implementing outbound email protection is not just an option but a necessity for modern businesses. By understanding its components and working principles, organizations can better safeguard their data, reputation, and compliance.
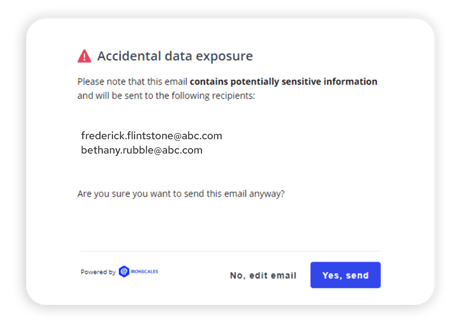
IRONSCALES Protects Against Accidental Data Exposure and Account Takeover
IRONSCALES helps prevent email-driven accidental data loss with real-time alerts. These mailbox-level alerts increase employee awareness and safeguard against the inadvertent transfer of sensitive data. The IRONSCALES Accidental Data Exposure capability utilizes advanced technologies to promptly identify and notify employees about emails that may leak sensitive data—enhancing their security awareness and proactively preventing potential data leaks in real-time.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












