Table of Contents
The pandemic has reshaped the world in many ways, from how we work and how we shop. As their workforces went remote, companies rushed to move their applications to the cloud. As lockdowns forced millions to stay home, people turned to online shopping to buy groceries, consumables and more. One company that sat at the nexus of these two major trends was Amazon. Cyber criminals launched an array of VEC (vendor email compromise) attacks, taking advantage of Amazon’s vast customer and cloud user bases. Here are just a few examples of what we identified:
Example 1 – Attempted theft of AWS user credentials
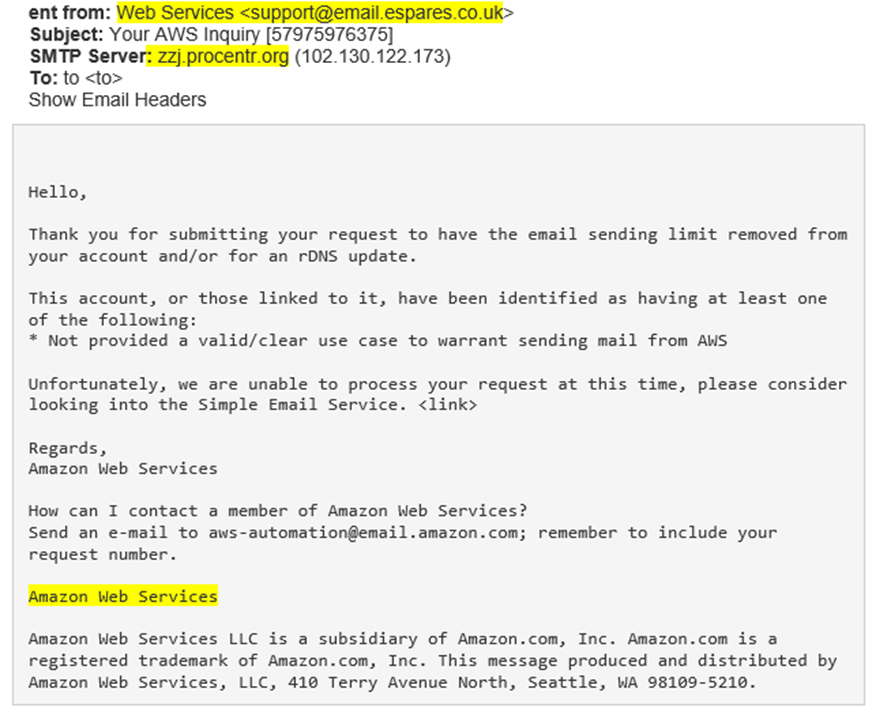
In this example, an AWS cloud user received an email stating that a technical limitation had been placed on their account and that they needed to provide their user credentials to remove the limitation. To do so, the victim was asked to click on a link, which sent them to a lookalike AWS login page. The victim was then asked to enter their user credentials. If they did so, the criminal would be able to harvest the credentials.
%20(1).png?width=762&name=picture1%20(1)%20(1).png) Example 2 – Attempted theft of Amazon retail customer credentials
Example 2 – Attempted theft of Amazon retail customer credentials
In this example, we identified an attack that attempted to convince an Amazon retail customer to give up their user credentials. The victim first received an email saying that their method of payment details needed to be updated to continue using the service. Should the victim click on the link, they would be taken to a fake landing page and asked to enter their payment details. These details would then be harvested by the criminals.
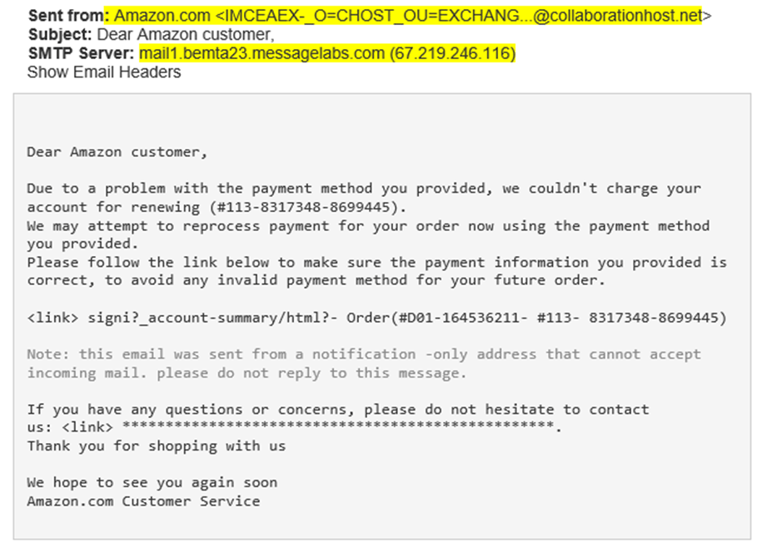 Example 3 – Attempted theft of Amazon retail customer credentials using a fake customer support telephone number
Example 3 – Attempted theft of Amazon retail customer credentials using a fake customer support telephone number
In this example, the victim received an email asking them to validate an order by calling the telephone number provided in the email. Should the victim dial the number, they would be directed to a fake customer representative, who would attempt to manipulate the victim into paying a transaction fee.
.png?width=682&name=picture1%20(1).png)
Why These Attacks Work
The success of these attacks relative to other phishing attacks, stems from a combination of social engineering and attack scalability. While targeted phishing attacks such as BEC and VIP Impersonations are known to be some of the most dangerous, they are not easily executed at scale. This is due to extensive research needed from the attacker’s perspective and the necessary personalization frequented in these attacks. Vendor impersonations on the other hand, such as these iterations of Amazon scams, take advantage of the reality in which most individuals have an Amazon account. Thus, when an end-user receives an email claiming “Update Credentials,” “Account Suspension,” or “Undelivered Package,” they are inclined to proceed with the call-to-action and fall for the scam. To be worth the investment in time and effort, these attacks must target companies with a large customer base who wouldn’t suspect that something was wrong. With over 200 million Amazon Prime members and thousands of AWS cloud users, Amazon customers were the perfect target. The frequency of communications between customers and Amazon retail customers on a variety of topics (e.g., orders placed, orders shipped, orders delivered, update Prime payment details, undeliverable packages) and the trust that shoppers place in Amazon, opens several opportunities for criminals to slip in attacks without notice.
How can you tell if you’re the target of a scam?
Detecting scams can be difficult, but not impossible. Here are a few things you can do:
- Awareness – Just knowing that Amazon customers are being targeted is important. Be suspicious of any email you receive. Educate yourself on how Amazon does and does not communicate with their customers.
- Anomaly Detection – Most scams contain some anomaly within the email itself. Oftentimes there are spelling or grammatical errors, inconsistencies between the sender’s name and sender address, business emails sent from personal domains such as Gmail, URLs with non-vendor domains and more.
- Sense of urgency – One of the methods criminals use in phishing emails is to create a sense of urgency to take action. This could be telling you that your payment details have expired, that your account has been locked, that a shipment has been delayed, etc. Approach emails like this with caution. Don’t be overtaken with emotion.
- Technology – Equip yourself with AI and machine learning driven technology such as IRONSCALES’ Themis, which can perform anomaly detection and behavior analysis automatically. Successfully mitigating such attacks before they reach the mailbox.
What should you do if you fell for a scam and gave out your personal or work credentials?
Regardless of whether you accidently gave out your personal or work credentials, time is of the essence to stop the criminal from using your information. If you gave out your personal details you should consider resetting all your passwords, request that the credit bureaus freeze your credit, and contact your financial institutions to inform them what happened so they can focus on detecting the attempted fraud.
If you gave out your work credentials, immediately notify your corporate security team. They will likely force a reset of your password and freeze your user accounts across all impacted business applications until they can determine that there were no compromises.
Once the dust has settled, you might also consider the use of an encrypted password manager and setting up multi-factor authentication on all your personal accounts (nearly every web-facing service has this as an option today).
We invite you to learn more about how IRONSCALES can fight against these and many other types of phishing attacks by combining human and machine intelligence. Learn more at www.ironscales.com today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)