Table of Contents
It may be wrong to admit, but I love a good con. It is the art of deception that fascinates me the most. Watching a con artist at work is enthralling and fills me with a mix of surprise at their audacity and elation that it didn’t happen to me. To gain the mark’s confidence, the con artist systematically exploits their psychology.
In the world of cyber-security, we simply refer to the con artist as a cybercriminal, much less of a romantic term. While the art of a deceptive phishing email is constantly evolving, the principles remain the same—to gain the confidence of the mark (phishing recipient) for financial gain.
What is a Nag Attack?
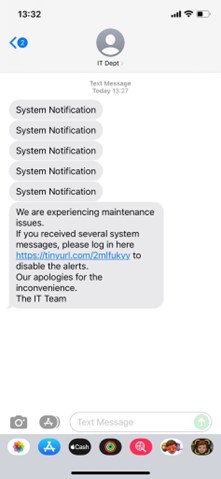
One of the recently emerging and increasingly popular phishing techniques is the “Nag Attack.” This social-engineering technique is a hybrid between the classic Phish, where an attacker sends a malicious email designed to trick the mark into revealing sensitive information, and Scam, a more elaborate con that initially appears harmless but is designed to pull the mark in and eventually cheat him or hear out of money.
The Makings of a Nag Attack
A Nag Attack always starts with “the Nag,” a repeated, seemingly innocent message or push notification sent to the target. The most common nags are MFA pushes (called “MFA-fatigue”) and System Error notifications. The Nag is always followed by “The Scam,” where the criminal impersonates someone (typically from IT) that is aware of an issue and needs some information to solve it. Once the information is provided, the criminal has free-range within the organization. Recently, several well-known organizations, including Microsoft, Cisco and Uber, fell victim to this attack technique employed by, among others, the infamous Lapsus$ and Yanluowang.
What Makes it Successful?
The brilliance behind the Nag Attack lies in the Nag that both wears down cyber-security resilience and functions as a piece of “intimate” inside information the criminal can refer to and reinforces the impersonation.
How To Prepare Your Organization
IRONSCALES recently developed the Nag-Attack Simulations to raise awareness and train users for these types of attacks. In addition, IRONSCALES’ Account Take-Over (ATO) detects and alerts users of the spray-attacks that typically precede the malicious MFA pushes. At IRONSCALES, we believe a truly cyber-resilient company is one that capitalizes on Artificial Intelligence as the first line of defense while empowering users with tools and training to build awareness as the last line of defense.
We invite you to download our new report "The Business Cost of Phishing", where you can discover the true cost of phishing on organizations as well as what IT and Security professionals believe is coming next. You can get the report at https://secure.ironscales.com/the-business-cost-of-phishing/report-download
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)