Table of Contents
We’ve been writing a lot about Business Email Compromise (BEC) attacks lately (six blogs and one research whitepaper since Jan 1st). So, I thought it would be good to provide some historical context.
What is Business Email Compromise (BEC)?
To set the stage, let’s touch on the basics, like what is a Business Email Compromise (BEC) attack. Short and sweet, it’s a type of targeted phishing attack where a threat actor accesses or spoofs a business email account to defraud a business. A more in-depth version can be found on our glossary page on BEC attacks.
Attackers typically follow three steps to launch a Business Email Compromise (BEC) attack:
- Research: Attackers research organizations to target and identify key employees, such as executives, finance staff, or human resources personnel.
- Strategize: They then configure methods to launch their attack, such as a spoofed domain, compromised account, or look-alike address—to make it appear to come from a trusted source.
- Execute: Attackers craft a compelling email with a strong “call to action” for the recipient, such as wiring money to a new account, updating payment details, sending payroll information, or verifying account information and credentials. The attacker may use social engineering techniques to create a sense of urgency or pressure on the recipient.
Before Business Email Compromise (BEC) attacks
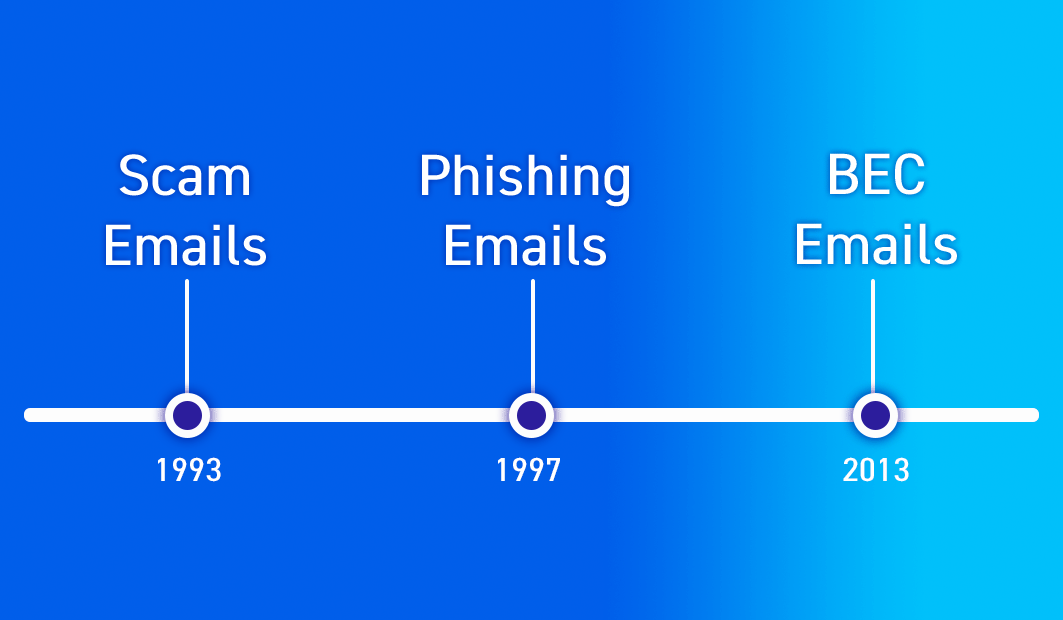
Email Scams – One of the first email scams everyone is familiar with is the Nigerian Prince scam. This email scam became infamous in the mid-’90s, but the concept of the scam dates back to the late 18th century with The Spanish Prisoner trick. It’s basically an “advanced fee” or “419” scam, which is when a victim pays money to someone in anticipation of receiving something of greater value, such as cash, an investment, or gift—and then receives little or nothing in return.
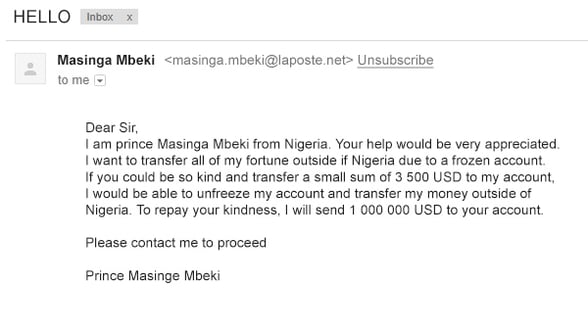
Phishing - The first significant instances of phishing emails targeted AOL users. In the late 1990s, cybercriminals adopted spoofed email addresses and websites to impersonate AOL employees and “lure” users into sharing their account passwords and credit card details. These bad actors exploited the obtained AOL credentials to launch spam and attacks on other AOL users, or they would utilize algorithms to generate random credit card numbers to make fraudulent transactions.
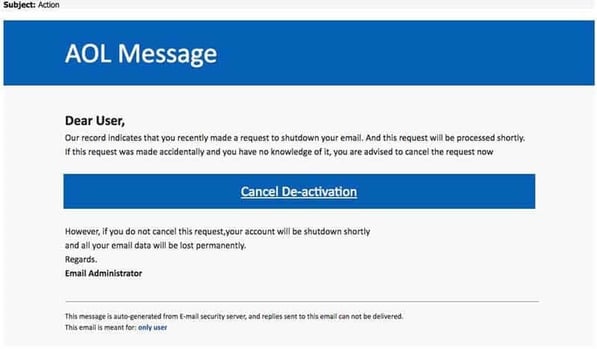
The AOL phishing emails inspired similar schemes pretending to be official PayPal and eBay messages warning of account suspensions, transaction disputes, and random purchases that were unfamiliar to the victims.
Early Business Email Compromise (BEC) attacks
The first recorded Business Email Compromise (BEC) attack is difficult to pinpoint as the term "BEC" was not widely used until around 2013. However, email scams targeting businesses and organizations have been around since the early days of email—oftentimes with spear phishing and whale phishing attacks. The FBI started tracking “emerging financial cyber threats” in 2013, calling them business e-mail compromises.
Remember our infamous Nigerian Prince? It turns out that a massive amount of the Business Email Compromise (BEC) attacks the FBI tracked in the following years were attributed to a handful of organized crime groups, including Gold Skyline (Nigeria), Gold Galleon (Nigeria), and Cosmic Lynx (Russia). The success and profitability of these BEC attacks inspired an explosion of attacks from organized and individual cybercriminals around the world.
The nature of BEC attacks, compounded by their highly-relevant construction, makes them difficult to differentiate from genuine emails, as the cybercriminals often incorporate accurate information about their victims, which they have obtained via previous intrusions or data scraped from social media and other online sources.
Warnings from the FBI explained, “Often, the emails contain accurate information about victims obtained via a previous intrusion or from data posted on social networking sites, blogs, or other websites. This information adds a veneer of legitimacy to the message, increasing the chances the victims will open the email and respond as directed.”
Related Article
Current and Future Business Email Compromise (BEC) attacks
Cybercriminals are known for being early adopters of emerging technologies which has led to the exponential growth of recorded BEC attacks as well as remarkable evolution in the quality of their email content. Some of the technologies include:
- Data Breaches – There is a shocking amount of breached information available on the internet and dark web, including user names and passwords, personal and financial information, email records, and more. It is accessible, organized, and productized on the dark web. There are over 4 billion passwords in the latest version of the RockYou2021 file.
- Automation – This allows attackers to scale their attacks by combining user names, email addresses, passwords, and email templates to conduct phishing, BEC, and credential stuffing attacks. The availability of phishing kits and services eliminates the need for technical expertise. These kits have the ability to circumvent or intercept multi-factor authentication (MFA) and carry out supporting nag attacks.
- Artificial Intelligence – AI is a game-changing force multiplier. It enables the development of highly personalized, contextual, and targeted BEC attacks. AI can also be used to create “deep fake” voice synthesis to mimic the voice of a VIP or executive and make phone calls to supplement email requests.
- Blockchain – Cybercriminals can use blockchain technology to make it even harder for law enforcement agencies to track stolen funds or ransomware payments
High-Profile Incidents Involving BEC
Facebook and Google
Serving as a warning that even tech giants are susceptible to BEC scams, Facebook and Google lost out on $123 million in 2016 to a Lithuanian cybercriminal. Mr. Evaldas Rimasauskas registered a company in Latvia with the same name as the Taiwanese electronics manufacturing company Quanta Computer.
Knowing that both Facebook and Google used Quanta Computer’s hardware in their data centers, Rimasauskas sent fake invoices to targeted employees and deceived them into transferring the money. He siphoned the funds to bank accounts located in various countries, but authorities eventually caught him and extradited him to the United States.
Toyota
In this incident, scammers targeted a European subsidiary of Toyota to the tune of $37 million. The pretext created was that the hacker impersonated a third-party business partner. The impersonator sent convincing emails to the accounting and finance departments where approval was given to transfer the sum of money.
Government of Puerto Rico
A successful BEC attack against the government of Puerto Rico demonstrated that this threat is not limited to for-profit businesses. Details emerged pointing to the attacker taking over an email account belonging to a government employee working in the pensions department. The scam involved informing recipients in other government departments about a change in banking details for remittance payments, which resulted in over $3 million being transferred to the threat actor’s own bank account.
Xoom
In one of the earliest high-profile examples of BEC, money transfer company Xoom got conned out of over $30 million in 2015. The attack seemed relatively simplistic with spoofed emails sent to the company’s finance department requesting the payments. This incident led to the resignation of the company’s chief financial officer (CFO).
How to Protect Against BEC Attacks
Business Email Compromise (BEC) attacks are difficult to detect and prevent because they rely on human error rather than technical vulnerabilities. However, there are some best practices that organizations can follow to reduce their risk of falling victim to BEC scams:
- Training: Use Security Awareness Training to regularly educate employees about the signs and methods of BEC attacks and how to report suspicious emails.
- Authentication: Implement strong authentication methods for email accounts and financial transactions, such as multi-factor authentication (MFA). The most secure MFA option is FIDO2 Security Keys that generate time-based one-time passwords (OATH TOTP); these can’t be intercepted by phishing kits as they require physical presence at the endpoint requesting authorization.
- Policies & Procedures: Establish clear policies and procedures for verifying requests involving money transfers or sensitive data disclosure. For example: requiring phone confirmation; using pre-approved payment lists; limiting wire transfer authority; etc.
- Security Configuration: Review email security settings and configurations regularly and update them as needed. For example: enabling anti-spoofing features; blocking external forwarding; flagging external emails; etc.
- Advanced Email Security Software: Add an AI-based email security technology to your stack that can identify subtle differences between fake (BEC) and genuine emails that slip past security technologies that depend on domain reputation or the scanning links and attachments for detection (like IRONSCALES).
93% of enterprises receive advanced BEC attacks that go undetected every year. Defend your enterprise from BEC attacks with the latest research from Osterman. Learn who's most at risk, which variants are used, and new tactics in the latest Osterman Research report, "Defending the Enterprise: The Latest Trends and Tactics in BEC Attacks."
Other Frequently Asked Questions
How common is business email compromise (BEC)?
Business email compromise is becoming increasingly common and the attacks are evolving into sophisticated and complex scams, making it more difficult for individuals and organizations to detect. According to the FBI's Internet Crime Complaint Center (IC3), BEC attacks have resulted in losses totaling billions of dollars worldwide. In 2023, the IC3 received 21,489 complaints related to BEC attacks, with reported losses totaling over $2.9 billion, averaging $134,952 per incident.
Is BEC the same as phishing?
BEC is not the same as phishing but rather is a specific type of phishing attack. It differs from other types of phishing attacks in that BEC usually doesn’t include the typical malicious links or attachments found in phishing emails but instead includes malicious requests (intent) targeted at specific organizations. These requests are generally aimed at redirecting financial transactions or stealing credentials or sensitive information.
Does cyber insurance cover BEC?
The specific coverage provided by a cyber insurance policy can vary, but many policies include coverage for losses resulting from business email compromise attacks, including the cost of recovering stolen funds, the cost of investigations and legal fees, and other related expenses.
It is important to carefully review the terms of your cyber insurance policy to understand the specific coverage provided, as well as any exclusions or limitations that may apply.
IRONSCALES Fights BEC For You
The most advanced email security solutions can do much of the work for you in preventing business email compromise. Our self-learning platform uses machine learning and user behavior analysis to rapidly detect any anomalies that are indicative of BEC scams.
To learn more about our award-winning anti-phishing and BEC detection and protection solution, please sign up for a demo today at ironscales.com/get-a-demo.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)