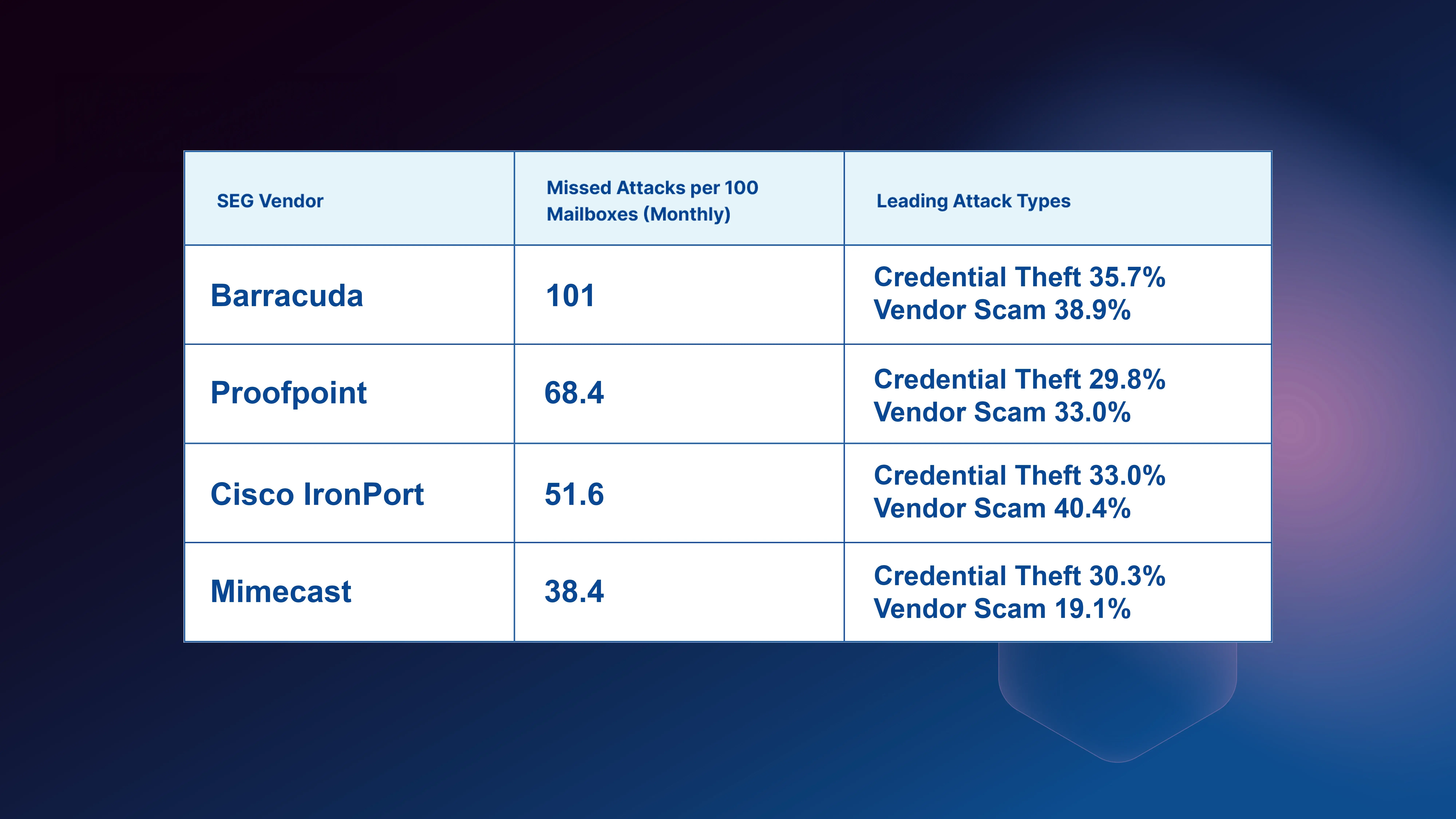
Table of Contents
A new phishing campaign highlights the need for modern email security approaches in combating account takeover and credential theft.
Launched in July and still active as of this writing, the advanced phishing campaign probed email inboxes and scraped the targets’ company-branded Microsoft Office 365 login pages to produce realistic credential harvesting pages. Once unsuspecting users logged in, attackers could steal their account credentials.
Clearly, traditional email security approaches like signature-based detection, advanced behavioral runtime-based technologies, static protocols, and blocklists are no match for increasingly sophisticated attacks like these. You can’t simply scan the HTML code behind a web page or email attachment to detect these kinds of malicious emails and websites.
Automated scraping of Office 365 login pages
Attackers used an automated email check for each target against a list of validated email addresses. Once validated, attackers scraped their targets’ company login pages, including custom backgrounds and banner logos, then inserted them into the phishing campaign landing page.
The cybercriminals hosted phishing landing pages on Microsoft cloud storage solutions, making them even more convincing to end-users because they were signed with a Microsoft SSL certificate. That’s especially concerning because many end users cannot distinguish a fake login page from a real one – let alone one with an SSL certificate.
Why legacy URL scanning technology can’t stop credential theft attacks
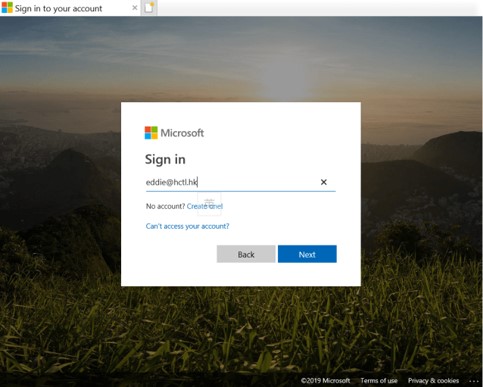
Traditional URL scanning technology was designed to scan the source code behind a suspicious HTML page and look for signatures of known attacks, as well as automated malicious code downloads. Attackers have learned how to work around this by creating polymorphic versions of a fake landing page, making it impossible for signature-based solutions such as malware and URL scanners to detect the threat. These pages also don't even try to download malicious code, they just wait for credentials to be entered. Here is an example of a credential theft attack using a fake Microsoft login page
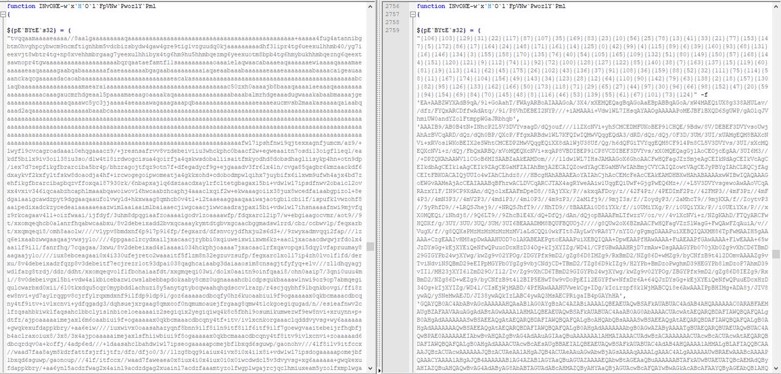
 Here is an example of what is an obfuscated code or in other words a polymorphic example of 2 different HTML codes that produce the same visual output:
Here is an example of what is an obfuscated code or in other words a polymorphic example of 2 different HTML codes that produce the same visual output:
 That is why visual similarity/computer vision is the answer, it does not rely on code scanning or signatures to detect fake/malicious login pages, instead, it visually compares the page to known existing legitimate landing pages such as O365 and tries to answer a simple question – does this page look similar to a legitimate page while directing them to a non authenticated/trusted URL. If the answer is yes, it is probably a phishing attack.
That is why visual similarity/computer vision is the answer, it does not rely on code scanning or signatures to detect fake/malicious login pages, instead, it visually compares the page to known existing legitimate landing pages such as O365 and tries to answer a simple question – does this page look similar to a legitimate page while directing them to a non authenticated/trusted URL. If the answer is yes, it is probably a phishing attack.
So, if traditional email security methods aren’t good enough anymore to protect your enterprise, what’s the answer?
CISOs should consider deploying smarter email security platforms that provide new layers of threat detection and intelligence against malicious emails and websites that “look so real.
Using AI-Based Computer Vision to Prevent Credential Theft Attacks
Attackers do their best not to vary too much from the look and feel of Office 365, as the visual representation is critical to getting end users to believe they are logging into the software.
Today, advanced anti-phishing protection requires more than simply inspecting inbound links and attachments. It requires advanced deep learning algorithms and computer vision to detect in real-time visual deviations and determine whether or not a login page is legitimate.
Anti-phishing solutions like the IRONSCALES advanced phishing threat protection platform can automatically detect visual deviations and warn end-users and SOC teams about potentially dangerous websites. Using artificial intelligence-based computer vision and neural network technology, the IRONSCALES platform can identify and block fake login pages in real-time that traditional email security approaches are simply unable to detect.
To learn more about IRONSCALES’ award-winning anti-phishing solution, please sign up for a demo today at https://ironscales.com/get-a-demo/.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)