Table of Contents
Over the past three months, our threat analysts have noticed a significant spike in attackers abusing Microsoft 365’s Direct Send feature—a tool intended for devices like printers or scanners to send internal emails without authentication. Unfortunately, threat actors have found a way to exploit this convenience, slipping past critical email security checks like SPF, DKIM, and DMARC.
Since May 2025 alone, attackers have compromised over 70 organizations across the U.S., hitting hard in sectors like manufacturing, consulting, and healthcare. These emails appear completely internal, often evading Microsoft’s built-in defenses and traditional Secure Email Gateways (SEGs).
The below information is intended to help you avoid this sort of compromise and take the necessary precautions to protect your organization from this growing risk.
How Direct Send Phishing Works
Exploiting Direct Send doesn't require advanced hacking skills. Here’s how attackers do it:
- Spoofing Internal Formats: Using easily accessible staff directories or predictable naming conventions to make emails appear legitimate.
- Leveraging PowerShell Scripts: Automating the sending of emails through Microsoft’s infrastructure.
- Skipping Authentication Checks: Emails sent via Direct Send bypass essential security checks (SPF, DKIM, DMARC), making them appear trustworthy to both users and security systems.
Since Direct Send doesn't validate SPF, DKIM, or DMARC, emails sent using this method often appear trustworthy to both systems and users.
Evasion Techniques IRONSCALES Is Tracking
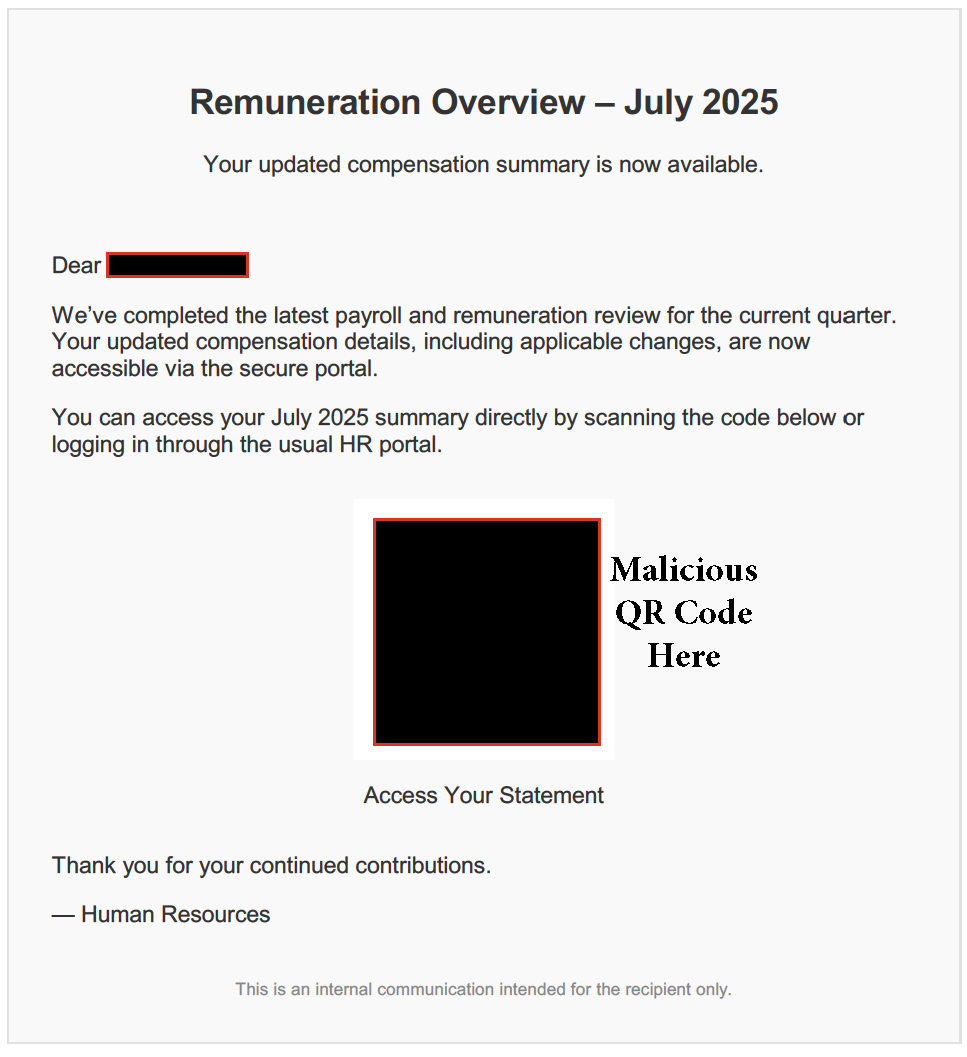
Empty Body with Malicious Attachments
This technique is particularly dangerous because it closely mimics legitimate operational email behavior. Since many organizations permit unauthenticated devices like scanners and copiers to utilize Direct Send for internal convenience, the malicious traffic easily blends in. This makes it challenging for traditional SIEM or EDR tools to identify anomalies in real-time.
The attached PDFs often imitate fax notifications, voicemail alerts, or financial documents—formats recipients rarely question. Given their Microsoft-based origin and the absence of URLs or malware, these emails consistently evade standard email filters and Secure Email Gateway (SEG) policies.
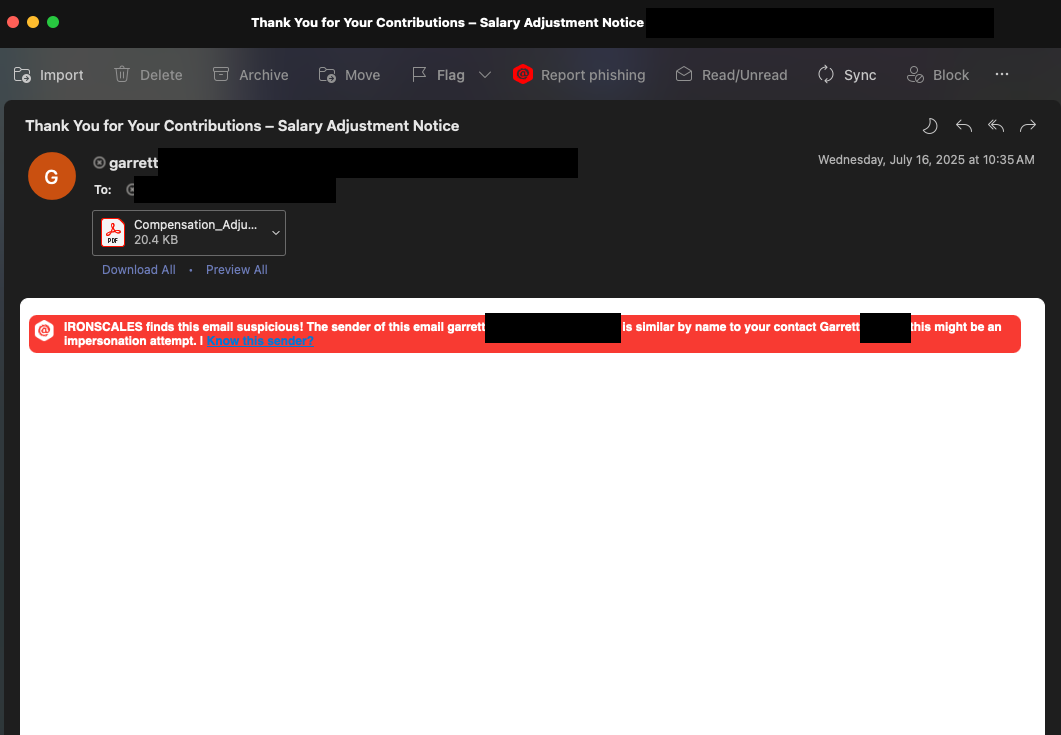
PowerShell-Based Internal User Spoofing
Attackers exploit Microsoft 365’s Direct Send feature, which originally allowed internal devices like printers to email without authentication. Using publicly available tenant naming conventions and predictable email formats, threat actors deploy PowerShell scripts to send internal-looking spoofed messages.
This method does not require compromised accounts or special privileges, just knowledge of common internal sender naming conventions. Because these spoofed emails originate from familiar-looking addresses without clear compromise indicators, they're highly effective at bypassing built-in security measures.
AI-Generated Spoofed Messages
Certain variants of this campaign utilize synthetic or AI-generated content, including fraudulent HR announcements and fake executive communications. Some attachments even contain manipulated audio files or convincing SharePoint links to boost user engagement rates further.
These carefully crafted messages exploit inherent human trust in internal communications by featuring visually polished formatting and recognizable branding. Since these messages rarely contain detectable malicious code, traditional text-based and signature-based detection methods frequently fail to flag them.
All three of these tactics are purposefully designed to slip past text-based filters and signature-based detection.
Why Traditional Defenses Fall Short
No authentication enforcement
Direct Send bypasses core validation checks like SPF, DKIM, and DMARC because it’s designed for trusted internal devices. As a result, threat actors can send spoofed emails that appear legitimate without triggering authentication-based security controls.
Microsoft source IPs
Since these emails originate from Microsoft’s infrastructure, they often inherit trusted sender status by default. Many native and third-party tools interpret this traffic as internal, which limits the scrutiny applied during scanning and routing.
Non-scannable payloads
QR codes and image-based links embedded in PDFs or HTML files often go undetected by traditional scanners. These payloads sidestep typical defenses that rely on visible URLs or known malicious signatures.
Familiar formatting
Attackers mimic legitimate internal email patterns, such as short messages or blank bodies with expected attachments. This lowers suspicion from end users, who are conditioned to trust internal communications that look routine.
A Growing Trend of Internal Impersonation
IRONSCALES has identified a broad trend emerging across Microsoft 365 environments: attackers impersonating internal communications to deliver credential theft or initiate business email compromise (BEC). Direct Send is a key enabler of this trend.
These attacks are:
- Highly targeted, often hitting HR, Finance, or executive users.
- Missed by Microsoft Defender and traditional SEGs.
- Scripted or AI-assisted, not mass-blasted.
- Frequently used as the first step in credential harvesting or wire fraud attempts.
How to Defend Against Direct Send Attacks
Restrict or Disable Direct Send
- Use Exchange Admin Center policies to disable unauthenticated Direct Send capabilities or tightly control its usage to authorized devices only.
Strengthen Authentication Protocols
- Enforce DMARC with strict policies (p=reject or p=quarantine) and tighten SPF configurations to enforce hardfail.
- Require DKIM alignment for all legitimate internal traffic, reducing the likelihood of successful spoofing.
Implement Advanced Security Monitoring
- Closely monitor email headers and sender IP addresses. Emails with SPF/DKIM failures originating externally but appearing as internal should be flagged for immediate review.
- Detect and analyze emails with unusual user-agent strings, indicative of scripting or automated activity.
Specialized Attachment and QR Code Scanning
- Deploy advanced email filtering solutions capable of scanning and detecting embedded QR codes within PDF attachments.
- Use sandboxing technology to safely detonate and inspect potentially malicious attachments.
User Education and Awareness
- Educate users about the dangers of scanning QR codes from unsolicited emails.
- Encourage users to verify unexpected or unusual internal communications through direct, independent contact methods.
- Highlight the unusual combination of empty emails with attachments as a potential red flag.
You Can’t Block What You Don’t See
Microsoft 365’s Direct Send is increasingly being exploited by attackers who understand how to leverage overlooked infrastructure gaps. These attacks often use minimalistic tactics, such as empty email bodies and QR-coded PDF attachments, specifically designed to evade traditional email security tools.
To mitigate these threats, organizations should enforce strict email authentication policies, disable or tightly restrict the use of Direct Send functionality, and implement advanced scanning technologies capable of detecting hidden malicious content within attachments. Regular training sessions to educate employees about evolving phishing techniques can further strengthen your organization's defenses.
Have questions about safeguarding your organization from Direct Send abuse? Reach out! We’re here to help.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)