Table of Contents
In the first blog of this series on image-based and QR-code phishing attacks, I explored the security-confidence dichotomy that Osterman Research uncovered—where organizations overestimate their defenses against these sophisticated threats.
Let’s continue our exploration and dissect the anatomy of these emerging attacks, compare their operational tactics, and analyze real-world examples. Then let’s touch on the multi-pronged strategies organizations are planning in response to these threats.
The Anatomy of Image-Based vs. QR Code Phishing Attacks
Image-based and QR code phishing attacks, while related, target victims using different methods. Image-based attacks are carefully crafted forgeries, imitating legitimate communications with the help of visual elements that can often escape detection by traditional Secure Email Gateways (SEGs) that primarily analyze text.
QR code phishing (Quishing) is a type of image-based attack that exploits the now ubiquitous QR code—perceived to be generally innocuous by most people—with links that take recipients to malicious websites. A key thing here is that they are also moving the attack away from “secure” devices managed by organizations, to employee-owned mobile devices.
The Routine as a Battleground
Phishing attackers are cunning artists in the craft of deception, and their canvas is the predictable patterns of our daily routines. The email from a title company concerning closing documents, the prompt from a healthcare provider for a routine check-up notification, a DocuSign request for a contract signature, or an order summary from online marketplaces like Amazon or eBay—these are not merely communications. They are the expected, the habitual, and now, the exploited.
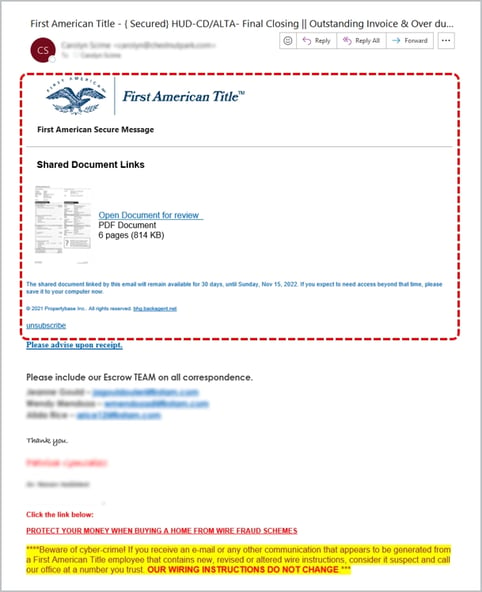
Consider the real estate professional who receives multiple notifications daily (hourly sometimes) about document updates, transaction summaries, and action-required emails. The First American Title spoof above is perfect example, it’s a masterclass in the exploitation of routine. It captures the essence of regular communication so perfectly, even the most vigilant cybersecurity-aware recipient could be forgiven for mistaking it for the real thing.
This attack does not scream danger…it whispers familiarity. An image that replicates an expected notification, down to the placement of logos and disclaimers, carries a serious threat just waiting for a simple click to start the exploit. The detailed deceit is even stretched to include a warning against cybercrime at the bottom…brilliant.
The attack leverages the trust we place in the continuous stream of notifications that are many of us are familiar with. It's not just real estate, every industry has its rhythms, it’s the expected—the update alerts, the transaction notifications, the document signature requests—that when mimicked, can bury the threats in our routines.
Strategic Responses to Evolving Threats
Armed with insights from Osterman Research, organizations are acknowledging the need for a layered approach to cybersecurity. Training users on recognizing emerging threats stands out as a priority, with a staggering 81.9% of organizations gearing up to educate their workforce.
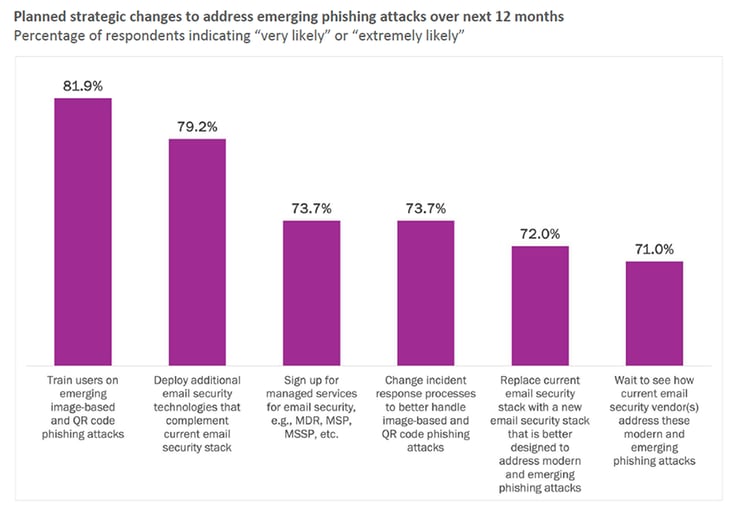
They aren’t limiting their changes to phishing simulations and security awareness training. Close to 79.2% are looking to enhance their email security technologies, an acknowledgment that current solutions must evolve to match the ingenuity of cyber adversaries. In parallel, over 73% of organizations are reevaluating their incident response processes and contemplating a shift to modern security stacks that promise greater resilience against image-based and QR code phishing attacks.
Preparing for the Next Wave
When even a tech titan like Microsoft can be convincingly impersonated to demand urgent action via a QR code, we are reminded that our defenses must be as versatile as the attacks are varied.
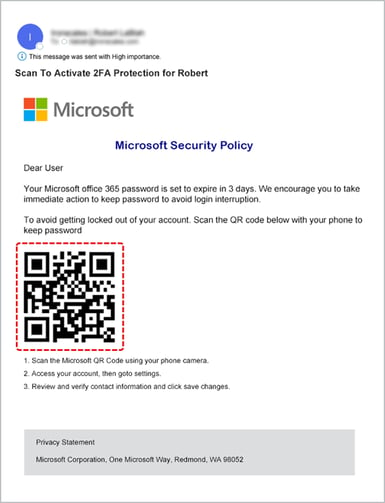
We must familiarize ourselves with these threats as much as we do with the routine emails that orchestrate our daily activities. In combating phishing, our vigilance must stretch beyond the extraordinary to scrutinize the everyday—the breeding ground for the most effective deceptions.
If you haven’t had a chance to read the report we did with Osterman Research, you can read it here (no form fill required), and if you want to hear the detailed insights from the leader researcher from Osterman, watch the webinar here.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)







