Table of Contents
Welcome to our live blog tracking new phishing threats related to the recent CrowdStrike incident. This blog will be continuously updated with newly discovered malicious domains and instructions to protect your organization. Use the Table of Contents to access each update.
Initial Post
In the wake of the recent CrowdStrike incident, malicious actors are seizing the opportunity to launch phishing attacks. We've observed a surge in the registration of look-a-like domains specifically designed to deceive users and propagate malicious activities. These domains were registered today within a four-hour window and pose a significant threat to organizations and individuals alike.
Below is a list of newly registered domains that you should block immediately to safeguard your systems.
Stay tuned, we will update this live blog with new domains as they are discovered.
[25-Jul-2024, 09:56 EST] List of Malicious Domains to Block
Our list of potentially malicious domains:
- Text file: crowdstrike_associated_domains_07252024_0852.txt
- CSV file: crowdstrike_associated_domains_07222024_0852.csv
Why This Matters
Phishing attacks exploit these domains to trick users into providing sensitive information or downloading malware. They can impersonate official communications, leading to data breaches, financial losses, and compromised systems. Immediate action is crucial to mitigate these risks.
Steps to Protect Your Organization:
- Block the Domains: Add the above-listed domains to your block lists within your email security systems, web filters, and firewalls.
- Educate Your Team: Conduct urgent phishing awareness training to inform your employees about the current threats and how to recognize suspicious emails. Use simulation tools to reinforce learning and vigilance.
- Monitor and Respond: Implement continuous monitoring of your network and email systems for any signs of compromise. Have incident response plans in place to act swiftly if a breach occurs.
By taking these proactive measures, you can significantly reduce the risk of falling victim to these sophisticated phishing attacks. Stay vigilant and keep your defenses strong.
[19-Jul-2024, 15:02 EST] Instructions for Adding Malicious Domains to M365 Block List
Step 1: Open the Microsoft 365 Admin Center
- Go to admin.microsoft.com.
Step 2: Navigate to the Security & Compliance Center
- In the left-hand menu, select Security.
- Click on Threat management, then select Policy.

Step 3: Access the Tenant Allow/Block Lists
- Under Policies & rules, click on Threat policies.
- Select Tenant Allow/Block Lists.

Step 4: Add a Block List Entry
- Click on the Domains & addresses tab
- Click on the + Block button
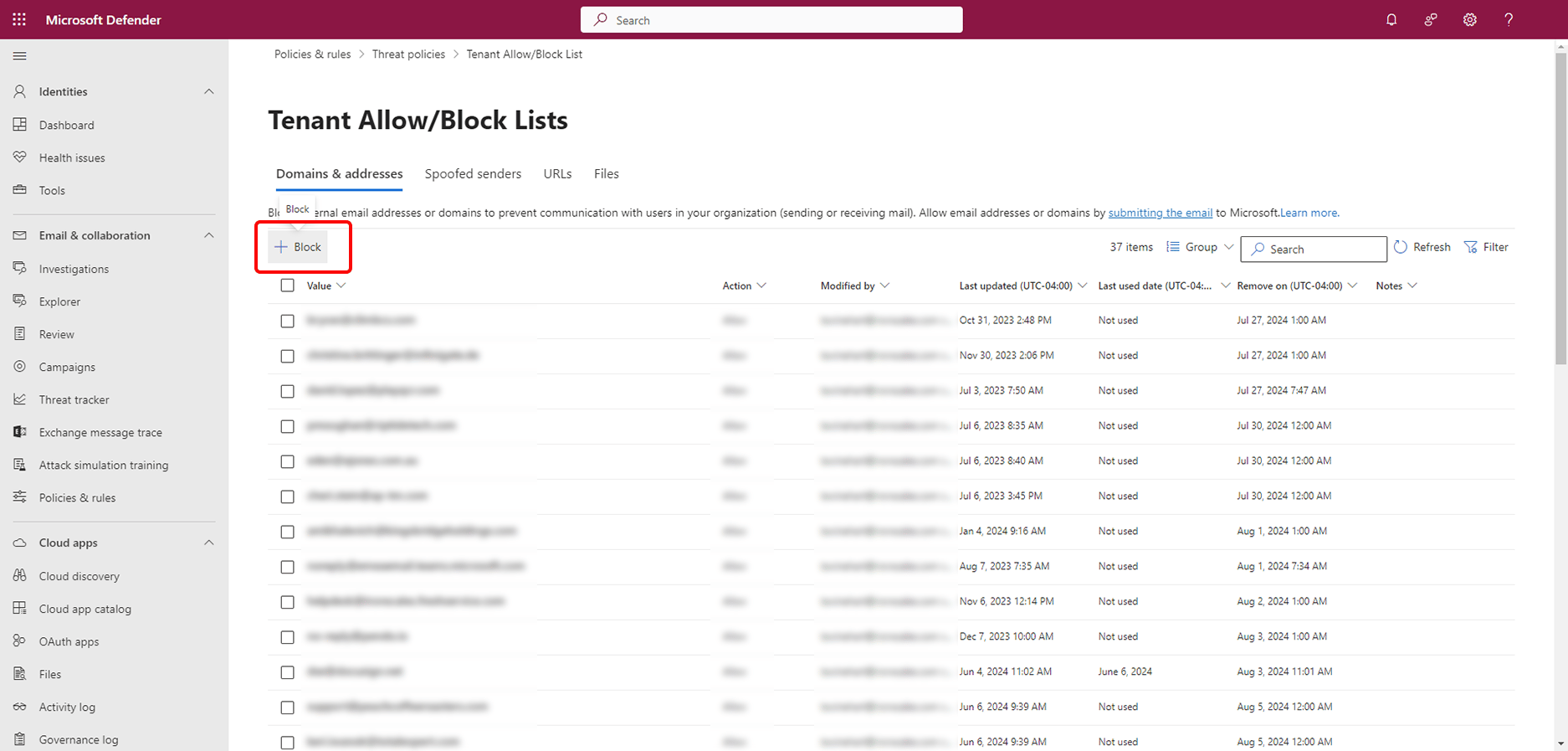
Step 5: Enter the Malicious Domains
- In the Block domains & addresses dialog, add the malicious domains to the list.
- Optionally, add a note, such as "Newly registered domains, likely to be used for phishing related to CrowdStrike outage."
- Click Add to save the block list.

These steps will help protect your organization from the phishing threats associated with the recent CrowdStrike incident. Check back regularly for updates.
[19-Jul-2024, 15:03 EST] Instructions for Adding Malicious Domains to Google Workspace (GWS) Block List
Step 1: Open the Google Workspace Admin Console by going to admin.google.com.
Navigate to Gmail Settings
In the left-hand menu, select Apps.
Step 2: Under Google Workspace, select Gmail.
Step 3: Access Spam, Phishing, and Malware Settings > Scroll down and select Spam, Phishing and Malware.

Step 4: Configure Blocked Senders
Scroll down to the Blocked senders section.
Click Configure.

Step 5: Create or Edit the Block List
In the Add setting dialog, click Create or edit list.


Step 7: Name the Blocked List and Add Domains
Name the list, e.g., CrowdStrike Impersonations
Click Bulk add addresses
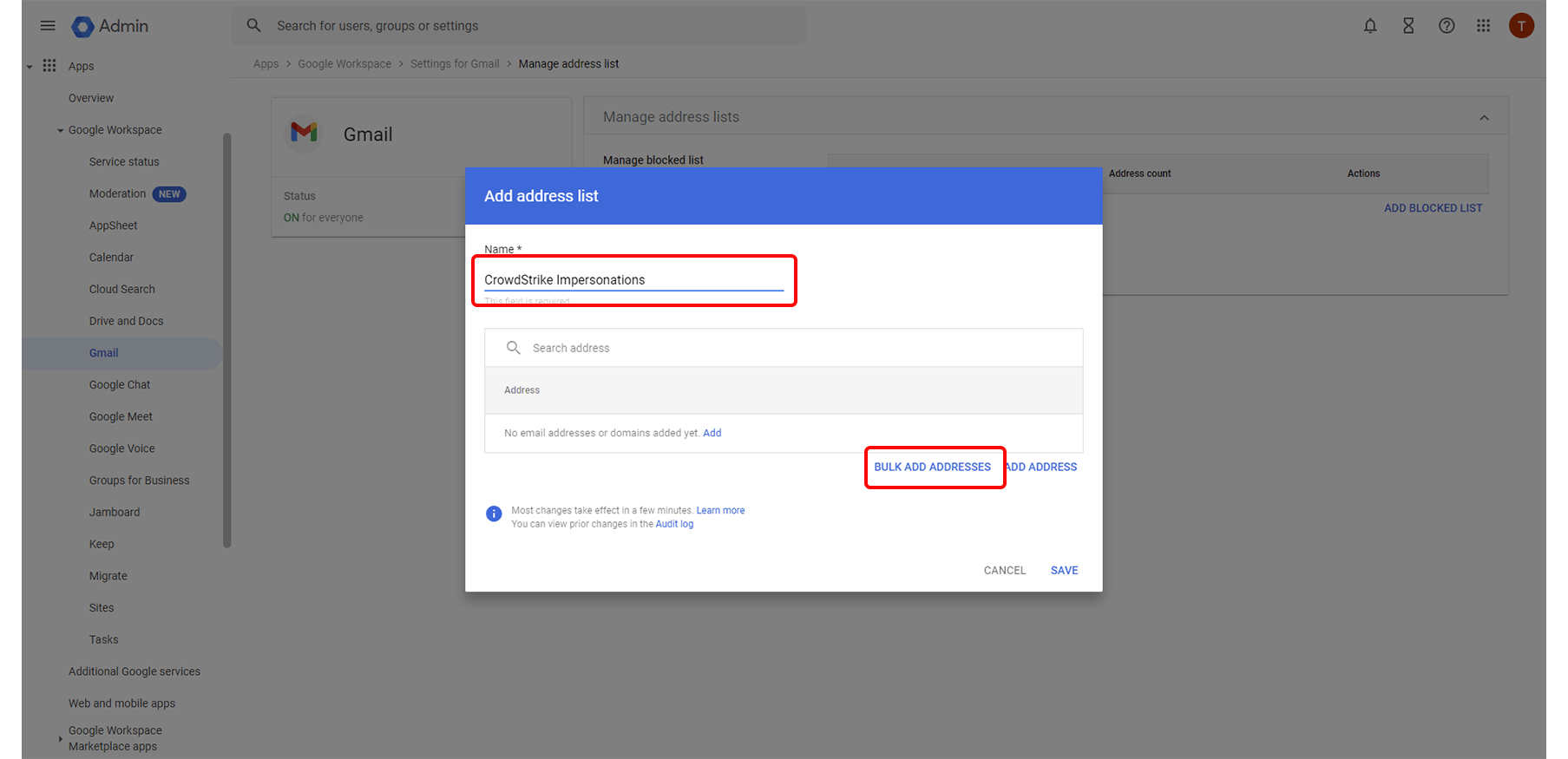
Step 8: Enter Malicious Domains
Enter the malicious domains in the provided field, separated by commas (or spaces).
Click Add.


Step 10: Use the Created List
Back in the Add setting dialog in the previous tab of your browser, click Use existing list and select the created list.
Uncheck the option to Bypass this setting for messages received from addresses or domains within these approved senders lists.
Click Save.

Step 12: Confirm Settings Update
Confirm that the blocked senders settings are updated.

[19-Jul-2024, 15:16 EST] - Additional source for emerging domains
Here is an additional source for new/emerging domains associated with CrowdStrike (note that there are many duplicates listed): https://urlscan.io/search/#crowdstrike*
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)







