Table of Contents
OpenSea, the largest non-fungible token (NFT) marketplace, disclosed a breach on their blog on June 29, stating that an employee of Customer.io, their email delivery vendor “misused their employee access to download and share email addresses – provided by OpenSea users and subscribers to our newsletter.” They went on to advise users to be alert for phishing emails that may attempt to impersonate OpenSea via email.
Attackers have been targeting OpenSea users with phishing messages for some time, but this breach will certainly lead to a wave of phishing emails targeted at the estimated 600k leaked email addresses that are probably already being sold on black markets. Since these email addresses will likely be listed as known NFT wallet holders, other NFT platform brands will probably be impersonated with “offer, trade, transfer” themed phishing email attacks.
More skilled attackers may also try to match these leaked email addresses with other data breaches to find passwords and other personal information that can be used to log in to OpenSea accounts as well as other crypto, finance, social media, or email accounts.
And if you are an IT or SecOps admin, don’t assume that these attacks don’t apply to your “domains”; many employees use their work email addresses for personal business and a malicious attachment or link can be used to propagate across your network.
Back to phishing: below are a couple of examples of credential theft attacks using impersonation attempts. We’ve seen many variations of these, and we are certain to see new ones—especially on the heels of this recent breach.
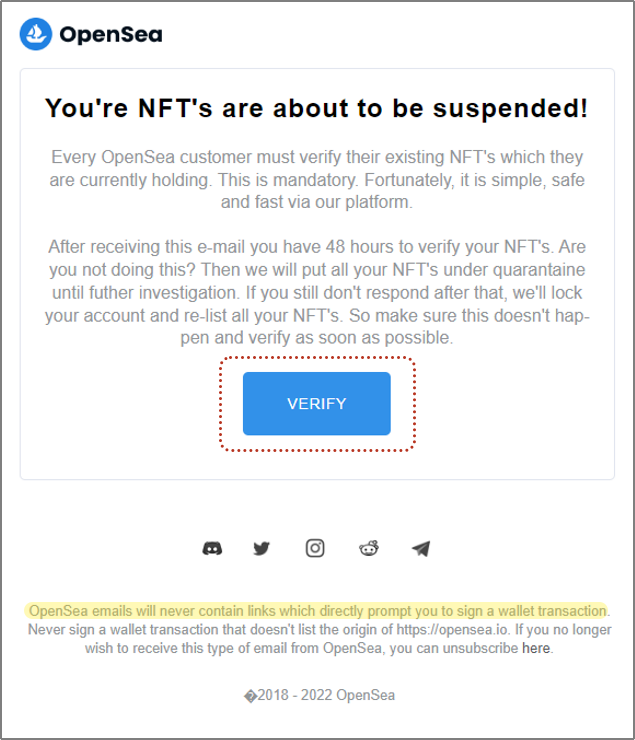
Example 1 - Verify Your NFTs
This email is designed to look like an official email from OpenSea and is an impersonation attempt designed to capture user credentials. It passes DMARC checks, but that just means that the sending domain wasn't spoofed. If the attacker tried to make it look like the email came from opensea.io, it would have failed a DMARC check.
The message (CTA) states that the recipient’s NFTs must “verify their NFTs within 48 hours or they will be quarantined.” They included a handy-dandy VERIFY button that links to a malicious URL that has already been taken down—but new ones will be created just as quickly as this one was taken down.
There are nine links in the email, eight of which are valid and safe links, but not that big blue button.
This is a decent-looking email by phishing standards. It has a properly sized logo at the top, the body of the email appears normal at first glance, and they included valid social media links at the bottom of the message. They even included a security statement at the end stating that “OpenSea emails will never contain links which directly prompt you to sign a wallet transaction.” Nice touch.
Sender:OpenSea Team<mail@puntodventa.com.pe>
To: █████████████
Return-Path:mail@puntodventa.com.pe
Return-Path Domain Age:N/A
DMARC Result:Pass
Mail Server:67.222.149.58 (United States) s15.servidorlatinoamerica.com
 Example 2 - You Have an Offer
Example 2 - You Have an Offer
This email is also an impersonation attempt. It was written in German (the English-translated version is also included below). The message’s SPF authentication check returned “soft fail,” probably because it has a valid domain of opensea.io for the sending address but different domains/IP addresses for the return path and mail server.
The message (CTA) states someone has made an offer of 9.8 ETH (Etherium) for an unnamed NFT article. Naturally, a recipient that has a digital wallet with NFTs for sale might be interested to learn more about the offer as soon as possible—and the attacker includes an easy-to-click button so the recipient can review the offer. The button links to a malicious URL that displays a page designed to capture the user’s OpenSea credentials.
Sender:Opensea.io<cpf@opensea.io>
To: ████████████████████
Return-Path:www-data@bundestag.de
Return-Path Domain Age:N/A
SPF Result:Softfail
Sender is identified as:External
Mail Server:185.116.106.98 (France) bundestag.de
.png?width=575&name=OpenSea%20content%202%20(english).png)
.png?width=575&name=OpenSea%20content%202%20(german).png)
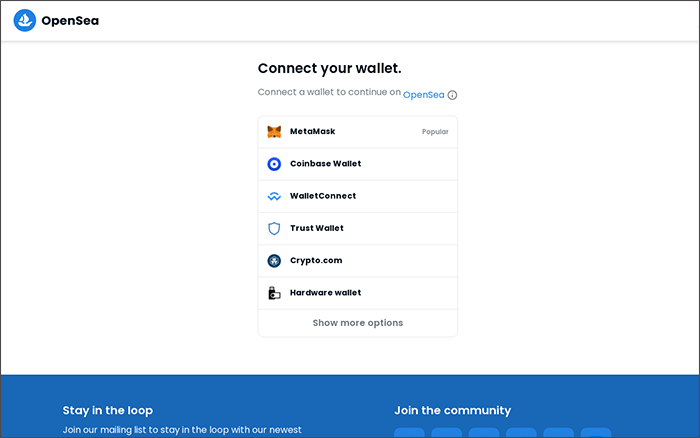
These attacks, and similar variations to come, attempt to steal a user’s credentials by including links to fake web pages that prompt visitors to provide their OpenSea credentials. Submitting the proper credentials will usually fail, but in some cases, the webpages will actually “proxy” the credentials to the actual OpenSea webpage after capturing the user’s credentials.
Here are examples of fake webpages designed to capture OpenSea credentials.
 What can you do?
What can you do?
If your email address was part of the OpenSea breach:
- Change your OpenSea password as soon as possible. Then go update your password on other accounts (NFT, crypto, finance, etc.) especially if you reuse passwords or use simple derivatives.
- If you don’t have one, get a password manager and use it to randomize unique passwords for all of your accounts.
- Consider removing SMS 2FA from your accounts and then enable U2F/FIDO tokens, especially if you have a high-value wallet, as motivated attackers will socially engineer your phone number to perform a SIM swap.
- Follow the advice provided on the OpenSea blog post (https://opensea.io/blog/safety-security/important-update-on-email-vendor-security-incident/).
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)