Table of Contents
Background
With several new two-dose COVID 19 vaccines being approved in the US by the FDA (from the companies Pfizer and Moderna), there was a rush of activity at multiple levels of government to establish eligibility criteria and to create websites where citizens could sign up to get their shot. There was a significant amount of chaos and confusion during these early days, as eligibility criteria varied by state and there was no coordinated effort on how best to make online registration webpages available. One particularly significant challenge was in New York City. The initial registration website was difficult to navigate, particularly for seniors (who were the largest group of those initially eligible for the shot.) Naturally, cyber criminals jumped on the opportunity to take advantage of the situation. This is one such example that we identified.
The phish
A number of employees of a company located in NYC received an email that supposedly came from Pfizer stating that the recipient was now eligible to receive the vaccine. To register for the shot, the recipient was asked to confirm their email address using a link embedded in the email they received.
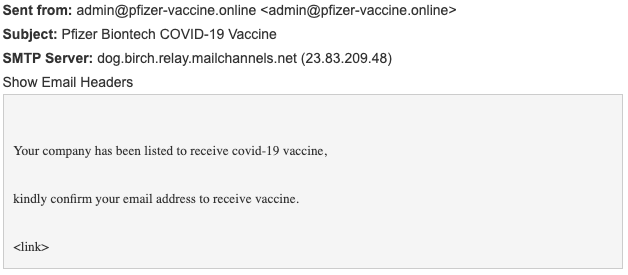
Payload
Upon clicking the malicious link, the victim was redirected to a fake landing page where they were requested to enter their Microsoft Office 365 credentials.
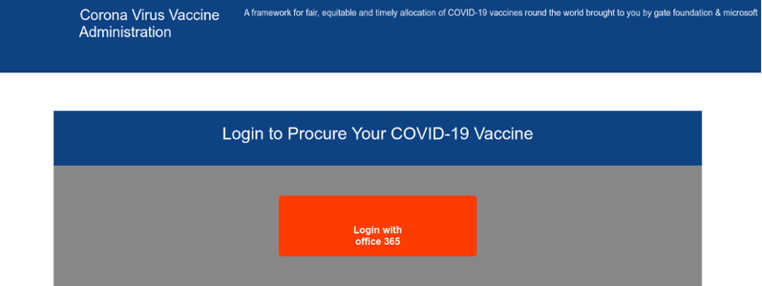 Why the attack could work
Why the attack could work
In this attack, it is possible that the attackers may have used social engineering techniques to identify specific people at the target company. The dynamic, confusing messaging around who is eligible for the vaccine combined with the confusion about how to register for the vaccine created plenty of stress. Add in the fact that New York City (where these recipients work) was particularly ravaged by COVID infections during the initial months of the pandemic and you can understand why the recipients might believe this was an authentic email. Victims may not suspect the fake landing page they were directed to, as it looked very much like a legitimate Office 365 login screen.
How we identified the attack
We were alerted to this potential attack by a member of our user “Community.” Upon further investigation we quickly realized that this email had been able to bypass the customer’s Secure Email Gateway (SEG). Various visual scanners were able to detect very small differences in the fake Office 365 login page that would be nearly impossible to detect by an untrained professional. Our AI (named “Themis”) ingested and analyzed all of this data and then provided a verdict that this was in fact a malicious attack.
We invite you to learn more about how IRONSCALES can fight against this and many other types of phishing attacks by combining human and machine intelligence. Learn more at www.ironscales.com today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)








.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)