Table of Contents
Traditional email security solutions such as secure email gateways (SEGs) are no match for today’s increasingly sophisticated email phishing and business email compromise (BEC) attacks.
Attackers are now using email phishing as the primary means for credential theft – a technique used to harvest credentials or access information – in order to commit types of fraud, such as selling stolen credentials on the Dark Web or performing account takeovers.
Compromised credentials lead to account takeover
Since it is typically the first piece that enables criminals to gain access to the account, credential theft is now considered by experts to be a stepping stone to account takeover. Through phony websites, malicious links and other carefully designed requests, attackers can now gather all the information they need to steal credentials, reset passwords and perform account takeover (ATO) for their gain, and the organizations’ loss. In fact, losses from ATO more than tripled in the last year to $5.1 billion, according to the 2018 Identity Fraud Study by Javelin Strategy & Research.
But while criminals can obtain credentials in many ways, email phishing remains the most common vector due to its ease of use and low risk, high reward.
Fortunately, organizations can reduce the risk of account takeover by training their employees in best email security practices and by putting an artificial intelligence-powered anti-phishing solution in the mailbox to identify suspicious emails in real-time.
Types of credential theft phishing
One popular credential theft phishing method is to register legitimate domains and use fake login pages of popular brands such as PayPal, Office 365 and Yahoo, then attempt to trick users to login at these sites through a fraudulent email alert. These login pages often look so real that even trained users can’t always identify them, and their lack of malicious code and content makes it difficult to impossible for email security safeguards to detect. To further mask the fraud and add legitimacy to the requests, attackers will often send emails from genuine user accounts.
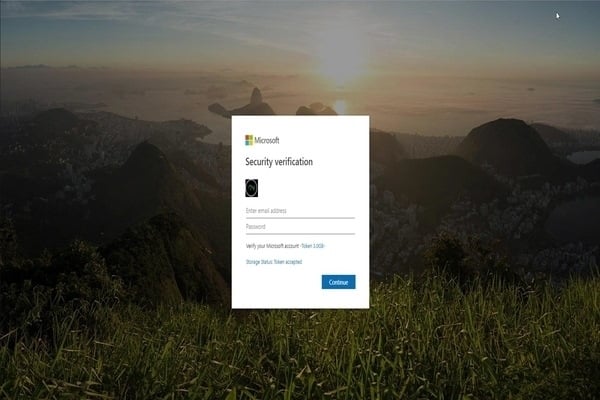
For example, this fake Office 365 log-in website the user is taken to can look extremely convincing, even adding a count-down clock to add pressure and drive action. The form itself looks identical to the real version usually with an identical Microsoft favicon. Often the site also has a valid SSL sign and sometimes they are even set up within a legitimate domain — making it extremely difficult for end-users to spot.
Other strategies to steal credentials include:
- Using malware to install keyloggers to collect data, login and password information
- Researching potential targets on social media to gather information
- Using brute force hacking tools
- Hijacking a Wi-Fi network
- Purchasing stolen credentials on the Dark Web
Once adversaries have the information necessary to access an account, they will often change the login credentials and contact information to lock out the original account holder. This often buys them time to conduct fraudulent activities before the user even realizes that their account has been taken over.
Reducing the risk of credential theft and account takeover
No two ATO attacks are alike, so organizations should use a combination of employee training and mailbox-level email security technology to reduce risk.
First and foremost, if a breach is suspected, IT administrators or security operation center (SOC) teams should shut down the compromised machine and remove it from the network. Next, reset all users’ passwords connected to the network, reformat or replace the compromised machines and notify third parties about the breach.
It’s best to be as proactive as possible, attempting to mitigate the risks beforehand by training employees in best security practices, including:
- Don’t click on links from suspicious emails
- Remain cautious of name brands asking for updated account information
- Use a password manager and never use the same password for multiple accounts
- Take advantage of two-factor authentication (2FA) when possible and use a VPN, especially when connected to public Wi-Fi
- Warn employees to be careful about what they share on social media because information such as names of coworkers and emotions on a topic are often used by attackers to build profiles and cultivate phishing emails
Organizations can use security information and event management (SIEM) systems to monitor login time, frequency, IP address and other events to detect suspicious logins. Administrators can also manually monitor or use automated solutions to monitor accounts for suspicious behaviors such as the escalation of privilege changes, big downloads, and unusual requests to access sensitive data.
Credential theft protection powered by computer vision and neural networks
IRONSCALES provides a robust layer of credential theft security with our AI-powered advanced email security platform, which analyzes sender profiles to determine the legitimacy of messages while looking for anomalies in login pages, visual deviations and referencing URLs in email communications.
Download our white paper, The Seven Essentials of a Modern Email Security Platform, to learn how you can reduce the time to detect phishing attacks from days to just seconds.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)


