Table of Contents
Let's touch on a topic that IT/Security admins can't afford to overlook—phishing simulation testing. Sure, I know it can be a hassle, but trust me, it's a crucial element in your cybersecurity arsenal. Let’s dig in.
The Crucial Role of Phishing Simulation
Imagine fighting email attacks as a chess game, but in this version of the game, your opponent can regularly change the rules and add new (never-seen-before) chess pieces. That's our reality. Our 2023 research with Enterprise Strategy Group sheds light on this: even with advanced tools, 34% of phishing attacks slip through. The 2023 Verizon Data Breach Investigations Report further highlights that human error is involved in 74% of breaches.
AI-based solutions make significant strides in this fight, but they're not foolproof. We need the "air cover" of well-trained human insights to bolster our defenses. This is where the power of regular, engaging phishing simulations comes into play.
Wondering about the effectiveness of these simulations? The answer is a definitive yes. The data we've gathered, which you'll see in the graph below (from our previous blog on phishing simulations), demonstrates their impact in transforming your team from vulnerable to vigilant.
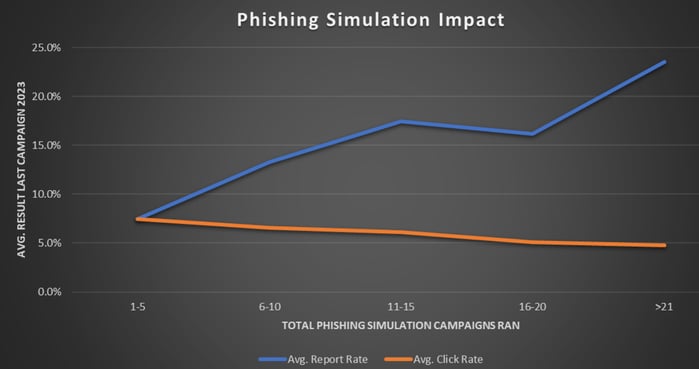
Our in-depth analysis reveals a strong link between the frequency of phishing simulation training and the rate at which employees report suspicious emails. Findings show that organizations conducting 1-5 phishing simulations annually see about a 7% report rate. This rate soars nearly threefold, to almost 21%, when simulations are increased to over 21 per year. This data underscores the importance of regular training in enhancing employees' ability to discern and report phishing attempts, thereby bolstering organizational cybersecurity.
Making Phishing Simulations Work for You
The key to successful phishing simulation lies in two things: relevance and regularity. Let's break that down.
- The Relevance—the content of your simulations should mirror what your team encounters daily. It needs to be relatable, believable–something they might actually click on. This realism is what makes the training effective.
- The Frequency—think of it as a regular drill, where repetition is the mother of skill. But here's a pro tip, randomize these simulations. You want to avoid the ‘gopher effect’ where one employee tips off the others, defeating the purpose of the exercise. Regular, unpredictable tests are your best bet for keeping everyone on their toes.
Addressing the Hesitations
So, why isn't everyone jumping on the phishing simulation bandwagon? Well, it boils down to a few reasons. For starters, it’s one of those “important but not urgent” things—it is undeniably crucial, yet it frequently gets sidelined for more pressing issues. Then, there's the technical and logistical side of things.
Setting up these simulations can be a complex task, especially if you're handling it manually or even with a semi-automated solution. And let's not overlook the fact that just about every IT/Security team is already stretched thin, balancing a myriad of competing priorities. With this in mind, here are some of the key challenges:
- Designing Effective Simulations—Crafting realistic phishing emails and landing pages is crucial. Too predictable simulations risk breeding complacency or overconfidence among users. Additionally, there's the challenge of keeping content updated for new threats and employees.
- Technical and Compliance Challenges—Executing simulations requires technical finesse, like spoofing sender addresses and navigating email gateways, which often involves modifying allow list rules. Moreover, there's the task of ensuring all activities align with legal and regulatory standards, including data privacy and consent laws.
- Feedback and Training Gaps—After simulations, it's essential but often overlooked to provide constructive feedback and follow-up training, especially for those who fail or report the simulations. This step is vital to enhance learning and improve future responses.
While these hurdles can seem daunting, they underscore the importance of a well-thought-out phishing simulation testing strategy.
Our Solution: Full Automation
To tackle these challenges head-on, we introduced our Autonomous Phishing Simulation program. It’s a game-changer. With a one-time opt-in, we take care of everything.
You choose when the simulations run, and we create content that reflects the latest phishing trends. We'll keep you in the loop with notifications and previews before each campaign. And after each simulation campaign goes live, you’ll get insights into which team members might need more training.
In the end, embracing phishing simulation testing is about more than just checking a box. It's about proactively empowering your team to face real-world threats. And with the ease of automation, it seamlessly integrates into your cybersecurity strategy. If you would like to learn more about this new feature or see how we can help you improve your email security, set up a demo today.
Stay vigilant and keep up the good fight!
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)







.png)