Table of Contents
UK organizations with sponsor licenses are now targets in a credential-harvesting phishing campaign. This campaign impersonates the UK Home Office and mimics the Sponsor Management System (SMS) login to steal usernames and passwords. Once attackers gain access, they can issue fraudulent Certificates of Sponsorship (CoS), exploit sensitive immigration workflows, or extort compromised users.
This attack is not technically groundbreaking. It is psychologically clever. It plays on trust, familiarity, and urgency.
So the question is not why criminals do this. The question is how we make it a non-event.
What Is Actually Happening
- Employees receive emails that look like they come from the Home Office.
- These messages include realistic branding and urgent instructions related to compliance or account access.
- Links point to a cloned SMS login page that captures real credentials.
- Once stolen, those credentials are used to submit fake sponsorships, extort victims, or pivot deeper into internal systems.
The phishing campaign is effective because it mimics a process people follow regularly. There is no malware, no obvious red flags, just a believable experience designed to catch someone in a hurry.
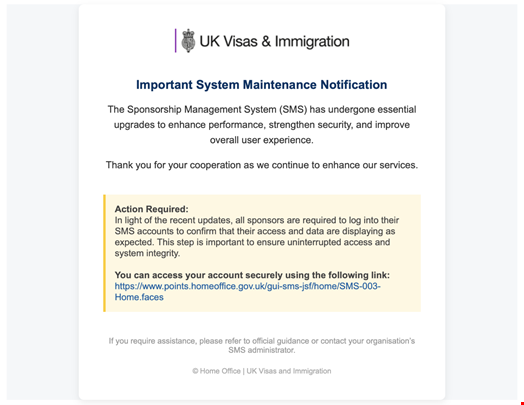
Image Credit - InfoSecurity Magazine 2025
Why Traditional Email Security Struggles
- Authentication checks only confirm sender legitimacy, not intent. A phishing email can pass SPF, DKIM, and even DMARC, and still lead to a dangerous payload.
- Visual mimicry works. Cloned domains and realistic branding trick even attentive employees. The damage often begins after the email is delivered, not before.
- User reporting is often too slow or too hard. If it takes more than one or two steps to flag a suspicious message, the dwell time increases and the attack spreads.
This campaign highlights not just a security failure, but a workflow vulnerability. The impersonation succeeds because it blends into a trusted business process.
What You Can Do This Week
Enforce Domain Authentication and Monitor It Continuously
Move all your email-sending domains to DMARC enforcement. Do not stop at "monitor" mode. Use SPF flattening to avoid lookup limits, rotate DKIM keys regularly, and publish records using a method that supports visibility and centralized control.
Monitor for anomalies using RUA and RUF reports if possible, and make sure that executive teams receive summarized, human-readable updates to track posture over time.
-
- Why it matters: Attackers often register lookalike domains that depend on weak validation to reach inboxes. By protecting your own domain and reviewing authentication reports, you can detect impersonation attempts faster and defend your reputation.
Strengthen Access and Workflow Around the Sponsor Management System (SMS)
You may not control the SMS platform itself, but you can control how your team interacts with it.
-
- Create role-based access with the least privilege necessary for each staff member. Use named accounts for sponsorship activity and rotate them when staff change roles.
- Apply phishing-resistant multi-factor authentication wherever possible, prioritizing app-based or hardware keys over SMS-based methods.
- Prohibit the use of email links to reach the SMS platform. Instead, direct users to begin every session by visiting the official GOV.UK portal. Document this in policy and audit it quarterly.
- Require SMS activity to happen in a dedicated browser profile or managed browser, with no third-party extensions and no auto-fill. This reduces the risk of cross-site contamination or password leakage.
If a phishing message gets through, every minute counts.
-
- Ensure your security tools operate at the mailbox level, with the ability to inspect language, relationships, and behavior patterns after delivery.
- Group near-identical phishing emails into one incident. A single confirmed malicious message should trigger removal across all user inboxes automatically.
- Make reporting effortless. Add a "report phishing" button in Outlook and Gmail that allows users to flag messages instantly, without forwarding or opening a help desk ticket.
If one person sees a phishing message and reports it, the system should be able to protect everyone else within seconds.
Reinforce Policy and Awareness at the Point of RiskTechnical controls are not enough. Habits and training matter.
-
- Add dynamic banners to emails that highlight external senders, unfamiliar domains, or content that references financial or immigration activity.
- Run phishing simulations that mimic current SMS-themed lures. Follow up instantly with training for anyone who interacts with the phish. Simulations should reflect the real world and build confidence over time.
The goal is not to expect perfection from users. It is to make it easy for the first person who senses something wrong to speak up and get a fast resolution.
What You Can Do This Quarter
Inventory Your Trusted Sender List
Create a living document of verified senders who are authorized to communicate about immigration or sponsorship processes. Include known Home Office and GOV.UK addresses, as well as any approved partners or third-party vendors. Share this list with staff and flag anything outside it for out-of-band verification.
This helps establish a baseline of trust and reduces the risk of falling for spoofed or typo-squatted senders.
Coordinate With HR and Legal for Incident Response
If an account tied to the Sponsor Management System is compromised, you need a clear and immediate playbook. Work with HR and legal to define what happens next: revoking access, rotating credentials, notifying affected departments, and contacting the Home Office through official channels.
Agree in advance who is responsible for each step. Run tabletop exercises to test the plan.
Set Up a Lookalike Domain Watch List
Monitor for new domain registrations that resemble your brand or known government agencies. Watch for inbound and outbound mail that includes these domains, even if the messages are not flagged as malicious. This early warning system helps identify impersonation campaigns before they gain traction.
Where appropriate, register variations of your domain name to prevent them from being used maliciously.
Review and Adjust Incident Automation Thresholds
As your detection and response systems mature, consider raising your level of automation. Begin with alert-only mode, then move to auto-quarantine, and eventually enable automatic removal of confirmed malicious campaigns.
Customize this based on your team’s capacity and risk tolerance. Automation should reduce alert fatigue, not create new blind spots.
Make Good Habits Easy
If your team types "Sponsor Management System" into their browser multiple times a day, give them a permanent bookmark and clear guidance: we never log in through an email link.
Security culture is built on consistency. Habits beat heroics every single day.
Final Takeaways
This campaign is not about breaking technology. It is about exploiting routine behavior. As long as sponsor-licensed teams continue to click login links in emails, these attacks will keep coming.
What works in practice:
-
- Enforce and monitor DMARC, SPF, and DKIM records for your domains.
- Use mailbox-level detection to catch threats after delivery, not just at the edge.
- Empower users to report suspicious messages in a single click and remove copies from every inbox instantly.
- Eliminate email from the login workflow by using bookmarks and policy enforcement.
- Train people using lures they are most likely to see.
Attackers depend on routine. Defenders must too.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)














.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)

