Table of Contents
In part two of this blog series, we explored the interdependencies of SPF, DKIM and DMARC; the limitations and vulnerabilities of each and addressed some of the unintended consequences of DMARC adoption.
As evident by the success of Mailsploit - a phishing method that enables attackers to create a nearly undetectable spoof – and other DMARC complexities and limitations – attackers are unlikely to abandon their spoofing techniques any time soon, no matter how widespread protocol adoption becomes.
In fact, an unintended consequence of DMARC adoption is that the more companies & organizations implement it, the more that attackers will launch domain impersonation attacks, which DMARC does nothing to protect against. Domain impersonation attacks (also known as homograph or cousin attacks), change character(s) in a domain, replacing numbers with letters, symbols etc. that look the same to both the naked eye and technology. Domain impersonation attacks are far more popular and easier to execute than exact domain spoofing.
In this third and final blog installment, we’ll introduce an anti-spoofing solution that provides all of the benefits of DMARC with none of the limitations.
The Unrealistic Expectations of DMARC Users
As a reminder, the underlying responsibility of DMARC is policy enforcement, so if SPF and DKIM are not properly implemented by both sender and receiver, then DMARC cannot be effective at limiting domain spoofing attacks. In other words, if DMARC is not adopted by every sender that you receive emails from, then you are not protected from domain spoofing attacks. Take note DHS - this reliance on full scale adoption is unrealistic.
Instead of focusing on preventing messages from getting into mailboxes, which will inevitably occur so long as email is a communications medium of choice, organizations must begin to approach email security from a different perspective – from inside the mailbox itself. This approach recognizes that attackers will always find a way in (which they do), and as such, acts as an added layer of security battling the millions of messages they bypass DMARC & secure email gateways (SEGs) every day.
Criminals are purchasing their way into mailboxes at scale with automation.
Attackers can register cousin domains to create DNS records which will nullify DMARC as an indicator of email company authenticity.
Because the domain is brand new, it won’t have a reputation, and as these traditional tools such as SEGs which leverage DMARC have a limited ability to identify potential harmful elements via any other means, they have no choice but to let them in by default.
Inoculating the Mailbox via Anomaly Detection & Smart Fingerprinting
The email protocol was not designed with security in mind, and there is no authentication mechanism in place whatsoever. However pseudo-authentication is now possible using ‘sender fingerprinting,’ an advanced machine learning based technology that can identify the true identity of a sender to answer the basic question of “who is sending me what?”
At IRONSCALES, we’ve developed mailbox-level anomaly detection, advanced protection against business email compromise (BEC), for our anti-phishing platform. This layer of security protects company's employees from all types of business email compromise (BEC) attacks, including domain spoofing, display spoofing and impersonation attempts, by analyzing data at the mailbox-level.
To authenticate emails, our mailbox-level anomaly detection scans every message for:
- The implementation level (no/full/partial) of DMARC/SPF/DKIM
- Sending IP addresses
- Normal communication context
- Email data & metadata
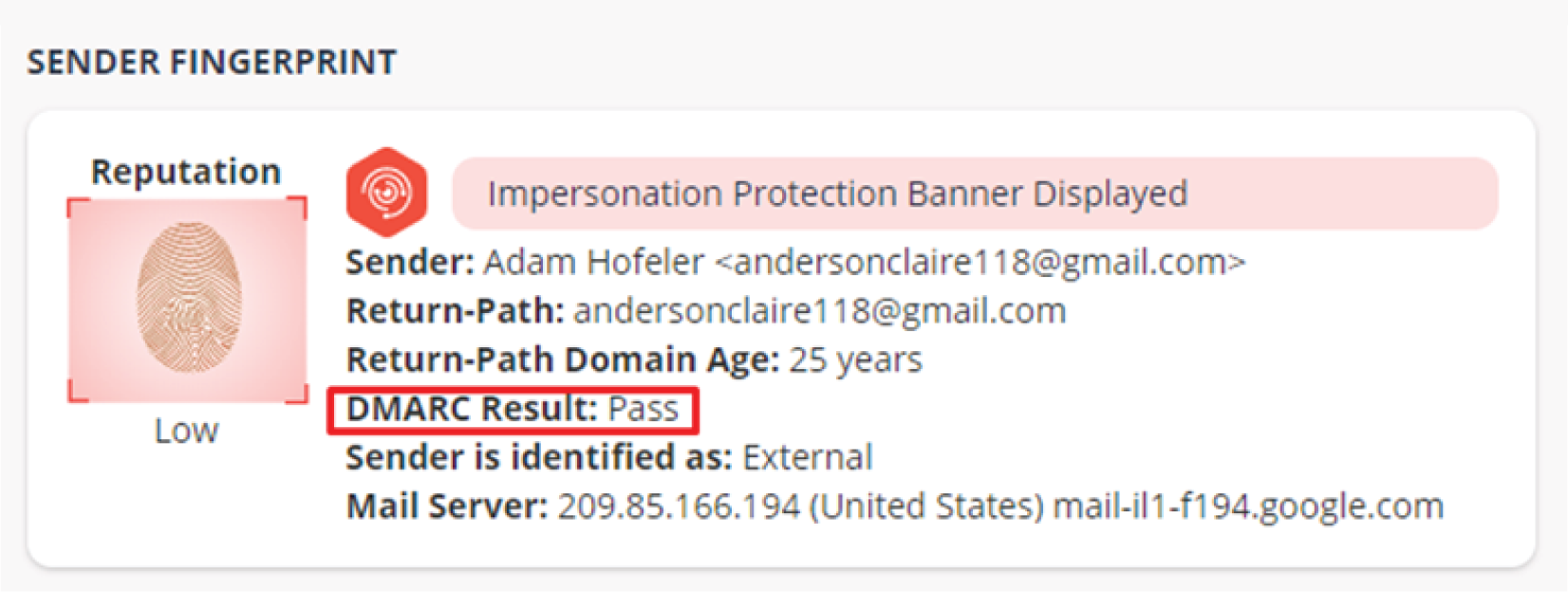
The aggregate of this information creates a baseline of normal communications that is consistently analyzed by machines to build out a unique fingerprint, which is assigned to every sender. Once the fingerprint is established, any deviation from the norm will be immediately detected and recipients will be notified of any potential threat through inline messaging.
Watch Our Video
By examining user communications and meta data to establish a fingerprint, anomalies in communications can more easily be spotted and automatically flagged as suspicious to help people make smarter and quick decisions that can be acted upon automatically or for the SOC/security to investigate, analyze and respond accordingly.
To prevent email compromises from hitting the mark, organizations need tools without limitations that are smart enough to warn end-users of the imminent detonation danger and empower them to neutralize the risk.
DMARC is practical in theory, but in reality, it is hard to use and maintain, and is only effective at stopping exact domain spoofing, which accounts for only a small subset of advanced email phishing threats. Sender fingerprinting, in contrast, is a solution built on advanced machine learning technology, with the primary purpose of discovering the true identity of any sender – no matter the type or technique of the phishing attack.
Social Engineering Phishing Techniques Have Highest Penetration Rates
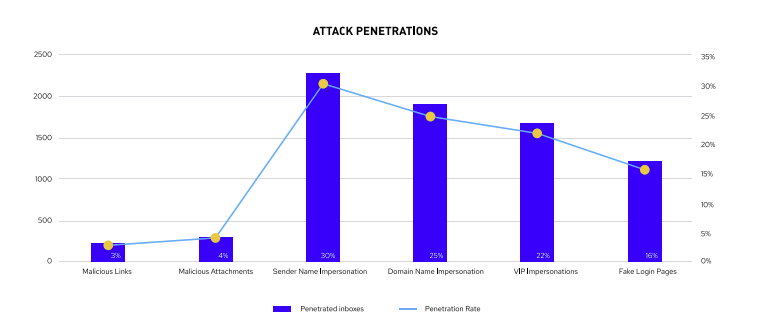
According to recent research, the phishing attack technique with the greatest penetration rate was sender name impersonations, which occur when an email masquerades as coming from a trusted source, such as a colleague, friend or family member.
Sender name impersonations
Accounted for 30% of all SEG penetrations, which represents a 6% increase from our 2019 analysis.
Domain name impersonations
Occurs when an email is from a similar domain, in which attackers register the domain to set the right authentication records in the DNS, accounted for 25% of penetrations This represents a 23% increase from our 2019 research.
VIP impersonations
CEO spoofs and fake login pages came in at 22% and 16%, respectively.
Source:https://ironscales.com/blog/emulations-bypass-segs-research/
To find out how IRONSCALES’ mailbox-level anomaly detection can help you defend against today’s spoofing threats when DMARC can’t by clicking here.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)


