Table of Contents
Phishing attacks are rapidly morphing at scale: a Google report shows a 350% increase since quarantine. As such, many organizations are reviewing their email security stacks to determine what’s working and what’s not, as they seek the best phishing protection with the lowest investment of money, effort and time.
But what’s the best way to figure that out? How can security teams ensure that their current email security stack is working? If existing tools are ineffective for your environment, how do you figure that out?
The market is saturated with anti-phishing and email security tools that claim to do everything. To know the extent to which your email defenses are functioning, it’s important to stay within the limits of available resources and test defenses with real, evolving phishing threats.
Unfortunately, some technologies do a better job at testing email security tools than others and at telling security teams what they really need to know.
Breach And Attack Simulation (BAS)
BAS is a new technology that lets organizations simulate hackers’ breach methods using past (read: not current) attacks. Security teams can automate these solutions to continuously test security infrastructure, but many BAS only use made-up email templates that do not necessarily represent phishing attacks trending in the real world. While It is good to know that your company is protected from known, historical attacks, BAS represents a false sense of security because it is not reflective of real-time threats. As attackers continuously launch new phishing attacks, organizations relying on BAS to support their email security infrastructure will be behind the curve, for testing only for known, and dated, attacks vs. the emerging threats they should be targeting will not help reduce enough risk.
Penetration Testing
Penetration testing is a labor-intensive, manual approach that typically assesses a predefined number of targets, using known exploits against known vulnerabilities, for an entire system. This type of testing enables a proactive security approach, helping to test any system with attacks that are as close as possible to real-world incidents. There are some notable drawbacks that make penetration testing expensive in time and money, however. Penetration testing is manual and requires a sophisticated analyst to spend hours performing the test. Organizations that implement this approach often perform penetration tests once or twice a year, or perhaps quarterly. While it can be effective in the moment, like BAS, it can ultimately give a false sense of security.
Vulnerability Scanning
Like traditional anti-virus tools, vulnerability scanning effectively automates testing across a computing environment. Such an approach offers advantages in both automation and speed, plus it’s low-cost, easy to use and thus also easy to continually deploy. However, when it comes to email security, vulnerability scanning is not great at identifying phishing threats – for example, it’s not effective against social engineering attacks, where there is no malware or malicious payload but malintent nonetheless.
Red teams
Large organizations sometimes deploy so-called “red teams” who simulate hackers by proactively trying to hunt and exploit cybersecurity risks in their organization’s computing environment. These teams absolutely mimic real-world attackers, using all means at their disposal - web client, web application, network, social engineering etc. to test. It is a highly sophisticated, manual methodology with its success based on the experience of the SOC team running the test. Red teams are completely out of reach for most organizations.
Introducing a new approach: IRONSCALES phishing emulator
To stay ahead of fast moving, ever changing threats, organizations need a solution that is real-time and real-world by nature. IRONSCALES Phishing Emulator offers a radically different approach. Now, security teams can test real and current threats against existing email security defenses, safely and know in near real-time where and how the company’s email infrastructure might be exposed and what needs to be done to fix it.
Built on our principle of humans and machines working together, Phishing Emulator allows SOC teams to replay real-time real-world phishing attacks, ones that were found effective against SEG’s and other email defenses in the past few hours. In total, Phishing Emulator allows security teams to
- Automatically replay suspicious phishing threats in a safe environment to test the response of security filters during a real phishing attack scenario;
- Explore existing weaknesses in email security infrastructure that could lead to data breaches and malicious infiltration;
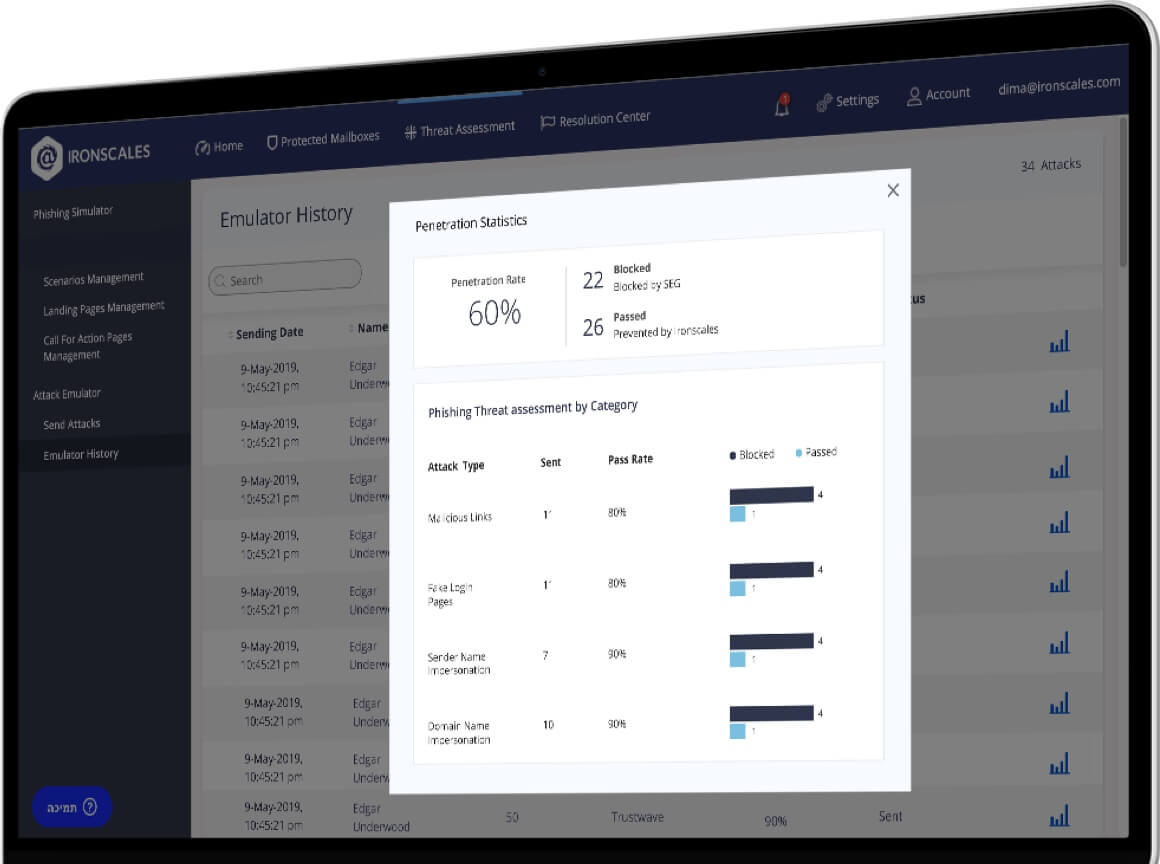
- Generate reports in just minutes on security vulnerabilities, revealing the types of phishing emails that bypass email phishing defenses;
- Show security teams the software, hardware and policy improvements needed to protect against advanced threats.
Security teams can select a pre-defined test mailbox to run a comprehensive test, which produces results in less than 5 minutes. To address this hidden risk, Emulator automatically deploys real-word email phishing attacks, including:
- Business email compromise
- Impersonation and spoofing
- Ransomware and other malware
- Fake login pages
- Other phishing attack techniques
And right now – it’s FREE. Start testing your email security infrastructure today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)