Guide to anti-phishing tools
Phishing is a social engineering technique that aims to trick the victim into providing sensitive information or performing some action on behalf of an attacker. Phishing attacks use different communication media—such as emails, phone calls, text messages, or social media—and the impact of these attacks can be devastating to any company.
The Internet Crime Complaint Center (IC3) report shows that the cost of phishing in 2022 was $2.7 billion in the US alone. Worse yet, there has been a disturbing increase in the number of phishing emails sent annually, especially since the pandemic. Kaspersky, a famous antivirus vendor, reported that it successfully blocked almost 508 million phishing emails in 2022, twice the amount it detected in 2021. Other reports, like the SlashNext State of Phishing Report for 2022, also indicate an increase in phishing emails.
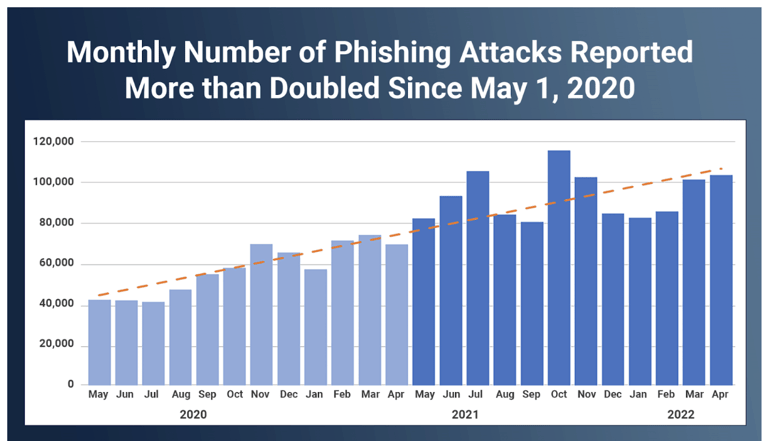
An increasing trend of phishing emails has been seen over the last few years. (source)
Phishing attacks target not only normal individuals but also companies, regardless of their size or profitability. Unfortunately, phishing is still causing companies substantial financial losses, with the SolarWinds supply chain attack in 2021 a concrete example. A phishing attack on SolarWinds led to a supply chain attack that affected over 100 companies and government institutions. The full extent of the damage is not yet known. Even Facebook and Google—big, security-aware companies—fell victim to a phishing scheme in 2015 and lost over $100 million.
All these statistics and famous attacks clearly show that phishing attacks can be devastating and that this attack type is becoming even more common among attackers. All companies should take this threat seriously and invest in anti-phishing tools to help detect, mitigate, or completely thwart phishing attacks and their consequences.
What is Anti Phishing?
Anti-phishing is the practice of using both human and software processes to prevent or remediate phishing attacks or scams where attackers attempt to extract sensitive data or personal information by impersonating a trusted source.
Phishing isn’t new. For decades, scammers have used email and other routes to try to trick unsuspecting victims to volunteer sensitive information like passwords, banking information, social security numbers, and more.
Fortunately, there are several successful tools, like anti phishing software and processes, that all businesses can use to stay safe from phishing attacks. In this article, we’ll dive into these techniques and discuss how you can apply them to combat phishing at scale.
In this article, we will look into some anti-phishing tools and discuss their potential benefits to your organization.
Summary of crucial anti-phishing tools
Understanding the top anti-phishing tools
In this section, we will cover each anti-phishing tool mentioned above in detail and see how they can help thwart phishing attacks.
Use secure email gateways (SEGs) and integrated cloud email security (ICES)
A SEG is an email security solution that is placed in front of your company’s email server to analyze each email before it reaches the email server. It scans emails using anti-spam filtering, AV scanners, anti-phishing filtering, email authentication checks, and DNS reputation scoring, enabling you to manage elements in quarantine (e.g., in case of a false positive).

SEGs have some disadvantages, such as the need to change the DNS MX record to redirect all of your email to the SEG as well as constant filter and YARA rule updates by your IT admins. Due to these disadvantages and the shift of companies from on-premises email servers to cloud-hosted email services, ICES was introduced. ICES offers most of the security features of a SEG, but also harness the power of AI and machine learning to automatically learn what is normal and what is a threat, eliminating the need for constant manual updates. Since it is an API-based solution, it can integrate with cloud-hosted email services in a few minutes without risky or disruptive MX record changes.
Although these email security products share some similarities, deploying both of them helps your company achieve a defense-in-depth approach to email security. This is especially valuable if your company is using a hybrid infrastructure (i.e., partly on-premises and partly in the cloud).
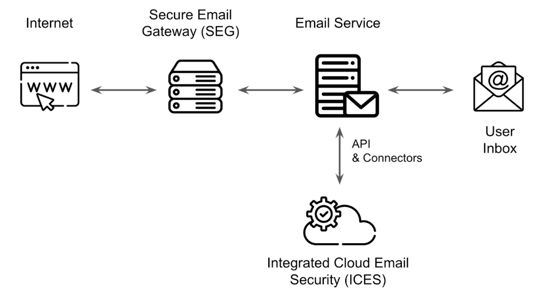
The Integrated Cloud Email Security (ICES) integrates with the email service via API
Integrate malware and URL sandboxes
While SEGs and ICES provide AV scanners, new “unknown” malware and ransomware will eventually manage to bypass these solutions that are dependent on signatures based on “known” malware. That’s why it’s essential to invest in a multi-purpose sandbox that can scan and safely “detonate” malicious attachments and URLs in phishing emails and block these emails before they are delivered to your employees.
Note that there are free online resources that can scan attachments and URLs such as VirusTotal and urlscan.io. However, these require manual effort from your security analysts and should be used only for specific cases. They are unsuitable for big companies that receive hundreds of thousands of emails a day since manually analyzing every attachment and URL your company receives via email is simply unrealistic. It might also contribute to the burn out your security team!
Create (custom) email filters
As mentioned above, many email security solutions provide built-in anti-phishing or anti-spam filters. However, email security solutions often ship with partially disabled email filters to avoid aggressively blocking too many emails, which can have an impact on your company. For this reason, your IT Security team should regularly update the built-in filters, activating or adjusting them to fit your needs.
Aside from the built-in filters, a vital feature to look for in an email security tool should be the ability to create custom filters. Attackers are getting increasingly creative and attempting to abuse many aspects of an email, not only the main attributes such as the subject line or sender field. For example, a recent vulnerability in the Outlook email client (CVE-2023-23397) exploited two specific “exotic” properties of an email to send a phishing email that would leak your NTLM password hash. While built-in filters cannot help you filter malicious emails abusing this vulnerability, an email security tool with support for YARA rules would enable your company to detect and block such emails, acting as a custom filter.

Enforce web proxy use
URL phishing is the most common type of email-based phishing seen today. Enforcing a policy requiring that the entire web traffic of your company go through your web proxy enables the security team to have a central place to search for employees falling victim to URL phishing, e.g., during phishing simulations.
More importantly, most enterprise or commercial web proxies provide additional capabilities, such as URL sandboxing, blocklisting based on threat intelligence (TI), category-based allowing/blocking policies, etc. For example, if your company is working with sensitive information, and you cannot afford for this information to be leaked, your company could create a proxy policy to block access to all websites that are categorized as “file sharing.” This makes it harder for attackers to exfiltrate data via file-sharing websites and can help avoid situations where internal employees mistakenly upload files online where they must not.
Use AI/ML-based detection
As we mentioned at the beginning of the article, phishing attacks continue to be a significant threat even for organizations that have become more security-aware over the years. This is happening because attackers are getting increasingly creative with crafting phishing emails, making it often impossible for email security tools to keep up with the latest trends.
To help with this problem, AI/ML models can be used to “learn” from phishing emails and ensure that future phishing emails with similar properties will also be detected.
As with all AI/ML models, the quality of the training data is crucial to the success of the model. Constantly feeding AI/ML models with real-life phishing samples and verdicts from human experts (i.e., “phishing” or “benign”) will ensure that these models remain up to date with the latest trends and can detect/block such emails if your company ever receives them.
Enforce multi-factor authentication (MFA)
One of the most common types of data that attackers try to phish for are account credentials. The attacker can use these credentials to breach your internal network, establish a foothold in your organization, and then pivot to other networked systems, leading to a full compromise.
Consider enabling and enforcing MFA across your entire organization to limit the impact of compromised credentials. While there are different MFA methods, such as SMS, phone calls, email-based, etc., FIDO2 is considered to be the most secure method.
Institute regular system and software patching
Although patching is often neglected, unpatched systems make successful phishing easier. Most email servers or email client applications perform different security checks on the emails that flow through them. An attacker could abuse a vulnerability in any of these systems to send specially crafted phishing emails that would not be blocked.
Note that patching should be deployed for all your systems—not only for email-related ones—since all devices are part of the internal network, and the compromise of one might lead to the fall of the rest. Make use of vulnerability scanners to identify vulnerable systems and then patch them as soon as possible.
Conduct security awareness training (SAT) and phishing simulations
In the end, the success of phishing emails relies on the ability to trick the email user. By regularly conducting security awareness trainings, your company can ensure that employees better understand what phishing is, how to recognize and report phishing emails, and the danger and impact of phishing emails. By conducting phishing simulations, your company can then measure the effectiveness of the training and identify who needs follow-up training.
Make sure that both SAT and phishing simulations are repeated periodically to keep employees up to date with the latest phishing trends. If your company does not have enough resources to conduct these activities, consider hiring specialized service providers.

Summary
In this article, we looked into phishing, its devastating impact, and famous phishing attacks in the past. We then discussed eight effective phishing tools and strategies that can be used to detect, mitigate, and prevent phishing attacks. The key takeaway from this article is that the amount of phishing emails is increasing at an alarming rate. Companies should consider deploying several anti-phishing tools because there is no one-size-fits-all tool.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











