Table of Contents
Recently we teamed up with research-firm Aberdeen Group to host a webinar discussing the obstacles email security currently faces as well as solutions that include a blend of advanced technology and human intelligence. In a guest post below, Derek Brink, CISSP, vice president and research fellow at Aberdeen Group, provides a summary of the webinar, including what steps can be taken to have an effective email security solution.
--
Cybersecurity isn’t fair.
It’s generally understood that in their ongoing battles, highly focused and financially motivated attackers need to be successful only once — but enterprise defenders need to be successful every time.
In email security, it’s even worse than that.
In my day job at Aberdeen, I was fortunate to be given the opportunity to analyze empirical data from a leading email security solution provider — IRONSCALES — which illustrates the incredible leverage currently enjoyed by attackers. For every uniquely identified phishing email attack:
- The number of unique user mailboxes affected ranges from 2 to more than 40
- The total number of organizations affected ranges from 5 to more than 150
In plain language: Every phishing email attack affects multiple mailboxes at multiple organizations — which requires hundreds of successful detections by the collective email security capabilities of enterprise defenders.
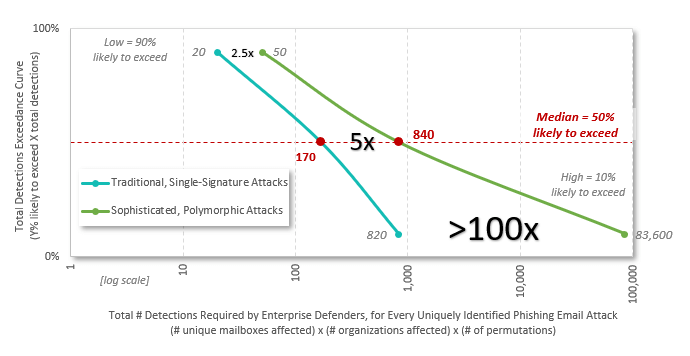
Doing the math: Based on the empirical data, a straightforward Monte Carlo analysis shows that every phishing email attack requires a median of 180 detections by all affected defenders, with a range from 20 to more than 840. That is, there’s still a 10% likelihood that it will be greater than 840.
Even in an era of more specifically targeted attacks (e.g., spear phishing), the empirical data illustrates how significantly email security threats are being amplified.
Unfortunately, it’s getting even worse going forward.
Empirical data from IRONSCALES further shows that more than 40% of phishing email attacks are polymorphic — meaning that they undergo at least one permutation that’s designed to evade traditional email security controls. The most sophisticated attackers are already implementing polymorphic phishing email attacks that undergo hundreds of permutations to evade traditional defenses, in addition to multiple mailboxes and multiple enterprises.
Again, we can do the math. An extended Monte Carlo analysis shows just how much these techniques increase the total number of detections required by enterprise defenders — the “blast radius,” if you will — as compared to that of traditional, single-signature attacks:
- From 20 to 50 at the low end, an amplification of 2.5 times
- From a median of 180 to 890, an amplification of about 5 times
- From 840 to more than 88,000 at the high end, an amplification of more than 100 times
Visually, this fundamental asymmetry between attackers and defenders is depicted in the following chart.
Polymorphic Phishing Email Attacks Significantly Increase the “Blast Radius,” Raising the Bar for Email Security
What Does More Effective Email Security Look Like?
To adapt and evolve with financially motivated and technically sophisticated attackers, effective email security requires a purpose-built blend of advanced technologies, human intelligence, and user behaviors.
Strategically, it seems to me that the two biggest opportunities for more effective email security are found in the following high-level capabilities:
- Increase the rate of detection / prevention, through
- Advanced technologies (e.g., automation, AI, machine learning)
- More effective leverage of human intelligence (e.g., specialized solution provider expertise, user reporting, cross-enterprise information sharing)
- Better user behaviors (e.g., security awareness training, reduced click rates)
Accelerate the time to detection / prevention / remediation
For these reasons, it seems clear to me that enterprises should establish their email security solution selection criteria — from specialist service providers such as IRONSCALES — in line with the above.
For more information, watch the full webinar below.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)













.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)