Table of Contents
Phishing attacks are always evolving, and in 2024 we’ve seen a major spike in campaigns using RTF (Rich Text Format) files. In March alone, we detected (and stopped) 6,755 of these attacks. What makes this wave stand out isn’t just the use of an outdated file format—it’s the clever tricks attackers are using to make their emails and attachments look more legitimate than ever.
Let’s dive into how these phishing attacks are manipulating file names, obscuring malicious URLs, and leveraging old-school attachment types to bypass defenses.
The Anatomy of the Attack
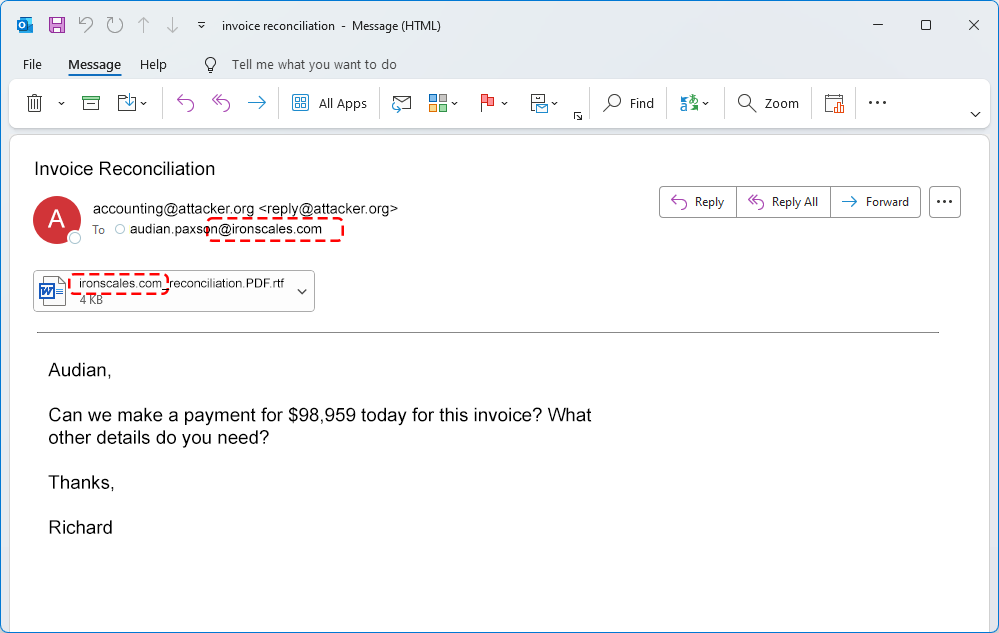
Here’s what these phishing emails look like at a glance: a businesslike message claiming to be an invoice reconciliation, with an RTF file attached. But there’s a clever twist—the file name is customized to match the domain of the target recipient.
For example, if this attack was directed at me, an employee at ironscales.com, the attachment would look like this:

This small detail goes a long way in convincing the victim that the email is legitimate, playing off the assumption that an attachment bearing their organization's domain name must be safe. And this is just the first layer of deception in this attack.
Why the RTF File?
RTF files are rarely considered suspicious. They’ve been around for decades and don’t raise the same red flags as executable (.exe) or compressed (.zip) files. But old doesn’t mean harmless. In fact, attackers are increasingly using RTF files because they’re often able to bypass more traditional email security filters, which may not thoroughly inspect these types of attachments.
And since many employees are used to dealing with financial documents like invoices and reconciliation reports, an RTF file with their domain name in the title feels like a normal part of their workflow. Attackers are betting you’ll open it without a second thought. (You really shouldn’t)
The Trickiest Part, Obscuring the Malicious URL with the @ Symbol
Inside the RTF file in these attacks is a link that looks innocent enough—often appearing to lead to a well-known site like microsoft.com. But this is where the attackers get even more creative. They use the @ symbol to trick the victim into thinking the URL is legitimate.
In the world of URLs, anything before the @ is treated as a ‘username’ but can be written to look like a trusted domain. The catch? The browser ignores everything before the @ and only cares about what comes after. So, a link like this:
https://microsoft.com@malicious-site.com/invoice.pdf
...isn’t taking you to microsoft.com at all. It’s redirecting you to malicious-site.com, where all sorts of bad things can happen, from credential theft to malware downloads. It’s like saying, “Trust me, I’m Microsoft” while leading you down a dark alley.
Let’s Break Down the Three Key Tactics Used in This Attack
- RTF File Use: Attackers are leveraging the trusted and widely accepted RTF file format to bypass traditional filters and gain a foothold in inboxes.
- Attachment Personalization: By prepending the name of the attachment to match the recipient's domain, the attackers are making the email feel more legitimate, increasing the likelihood that the victim will open the file.
- URL Obfuscation: The use of the @ symbol in URLs hides the true destination, tricking users into thinking they're clicking on a trusted domain like microsoft.com, when in reality, they’re being redirected to a malicious site.
Advanced Tactic - Using Hidden CSS and Obfuscation
In addition to using RTF files and personalized attachment names, attackers are also embedding hidden CSS rules and obfuscation techniques to make phishing emails even harder to detect.
Attackers often pack emails with garbage CSS, applying rules like display: none, color: transparent, height: 0, and width: 0 to hide parts of the content. This invisible text doesn’t show up for the recipient but exists in the email’s HTML, where it can help attackers bypass security filters.
For example, here’s how attackers use CSS to hide text by setting properties like display: none and color: transparent:
 CSS rules used to hide text within the email’s HTML, making content invisible but present.
CSS rules used to hide text within the email’s HTML, making content invisible but present.
Additionally, attackers often insert zero-width spaces (\u200b), a Unicode character that is invisible to users, into the text. These characters break up important strings of text to confuse automated detection systems. This makes it harder for filters to flag the email based on keywords or known phishing signatures.
In addition to hidden CSS, attackers often use zero-width spaces and HTML tags to insert malicious content into emails without being detected.
Below is an example of attackers using <abbr> tags and zero-width spaces (\u200b) to obfuscate the email content:
![]() Zero-width spaces (\u200b) and HTML tags used to obfuscate content, making it difficult for filters to detect phishing keywords.
Zero-width spaces (\u200b) and HTML tags used to obfuscate content, making it difficult for filters to detect phishing keywords.
How IRONSCALES Stopped These Attacks
We’re not an old SEG, these tactics didn’t go unnoticed by our AI. Our platform’s AI-powered behavioral analysis immediately detected and blocked these phishing attacks before they could cause any harm. By continuously monitoring communication patterns and analyzing content, our AI flagged these anomalies in real-time.
Additionally, our attachment and link scanning confirmed the malicious nature of the RTF files and obfuscated URLs. The combination of Adaptive AI detection and real-time scanning continues to prove essential in combating these evolving phishing tactics. It’s how our models learn how to detect the next variation of this attack.
What This Means for Your Organization
Phishing attackers are getting smarter, using RTF files, personalized attachment names, and clever URL tricks to lure victims. But by staying aware of these tactics—and deploying advanced security solutions—you can protect your organization from these evolving threats.
Here’s what you should do (other than making sure you are using IRONSCALES):
- Empower Your Team
Train your employees to spot suspicious file names and check the full URL before clicking on any links, especially if they contain the @ symbol. - Don’t Trust File Names Alone
Attackers know that something as simple as including your company’s domain in the file name can make you drop your guard. If a file name looks oddly customized or too perfect, double-check it with the sender—especially when handling invoices or contracts. Always open attachments with caution, even if the name seems familiar. - Beware of Unexpected File Types
If you’re receiving an RTF file when you expected a PDF or other common document type, take an extra pause. RTF files are rarely used in modern workflows, so any unexpected RTF should be considered suspicious until verified.
RTF-based phishing attacks show that attackers are constantly finding new ways to trick users. While AI-powered email security can catch most of these threats, staying vigilant—especially around file names, unexpected formats, and evolving tactics—remains key to keeping your organization secure.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)