Table of Contents
Attackers never stop looking for new ways to target individuals and defraud organizations. And the recent collapse of Silicon Valley Bank (SVB) and Signature Bank has provided cyber criminals a ripe opportunity to create a new variant of business email compromise (BEC) attacks. These attacks will exploit fear and uncertainty for businesses, their employees, and their vendors; all of whom want to ensure that their payroll and business operations are not disrupted.
If you aren’t familiar with what a business email compromise (BEC) is or how they work, in short, they are a type of phishing email where the attacker impersonates a legitimate person or company to trick the recipient into taking some action, such as changing banking account information, transferring money, or making one-time payments in the event of an emergency (like the collapse of a financial institution). BEC attacks have been around for several years and have evolved to become increasingly sophisticated. See What is Business Email Compromise? to learn more about BEC attacks.
This new variant of BEC will use the pretext of the events surrounding the collapse of Silicon Valley Bank or Signature bank to impersonate known vendors and request that victims provide new bank account routing and account numbers to update payment information. Victims will be less likely to question the legitimacy of these requests since they are keenly aware of the recent news. As such, it's important for individuals and organizations to be aware of this new variant of BEC to avoid falling victim to it.
To protect against this new variant of BEC, individuals and organizations need to be extra vigilant when reviewing emails. It's important to scrutinize the details of the email to ensure that it is legitimate. For example, the recipient should check the email address of the sender and confirm that it is accurate. As always, they should also look for any language that might be out of place, such as poor grammar or spelling mistakes, however, the arrival and easy access to ChatGPT makes it much easier for attackers to craft higher quality and more convincing emails.
SVB Email and the Sharp Eye of an Employee (yeah, training works!)
No single technology or solution will catch 100% of phishing emails and BEC attacks, especially zero-day or emerging variants. So, it is critical that ALL employees regularly receive security awareness training (SAT) and phishing simulation testing to ensure they can recognize sophisticated attacks that slip by traditional secure email gateways, and that they also know how to report any emails that they believe to be out of the ordinary. If they aren’t absolutely confident the email is safe, it’s always best to rely on a security expert to analyze the email, the bad guys only have to be lucky one time to do a lot of damage to an entire organization.
On Sunday, Mar 12, we received an alert from one of our customers about a potential Silicon Valley Bank (SVB) themed BEC attack. One of their employees with a sharp eye noticed something unusual about the email (other than the obvious subject matter) and used the IRONSCALES “report phishing” button in their Microsoft Outlook client to escalate the email to their IT security team and IRONSCALES analysts.
Our analysts reviewed the email, and it passed all the normal DMARC technical checks and scoring of the sender’s domain and IP address. Our AI and machine learning didn’t identify anything anomalous relative to what is normal for that customer or the sender, and there weren’t any malicious links or attachments to scan, which is typical for a BEC attack, so we investigated the “call to action” or intent of the email. We were able to confirm that the email was 100% authentic and safe.
What caught the employee’s eye? A copy of the email is below. The sender knew that this type of email might look suspicious to their recipients, especially because it had to do with Silicon Valley Bank and changing payment information, so they went above and beyond and added text right at the top of the message stating, “This is not a phishing or scam email” and additional “Anti-Fraud Evidence” at the bottom of the email. It is common for attackers to add this type of language to email attacks, and the employee had been trained to look out for such an indicator.
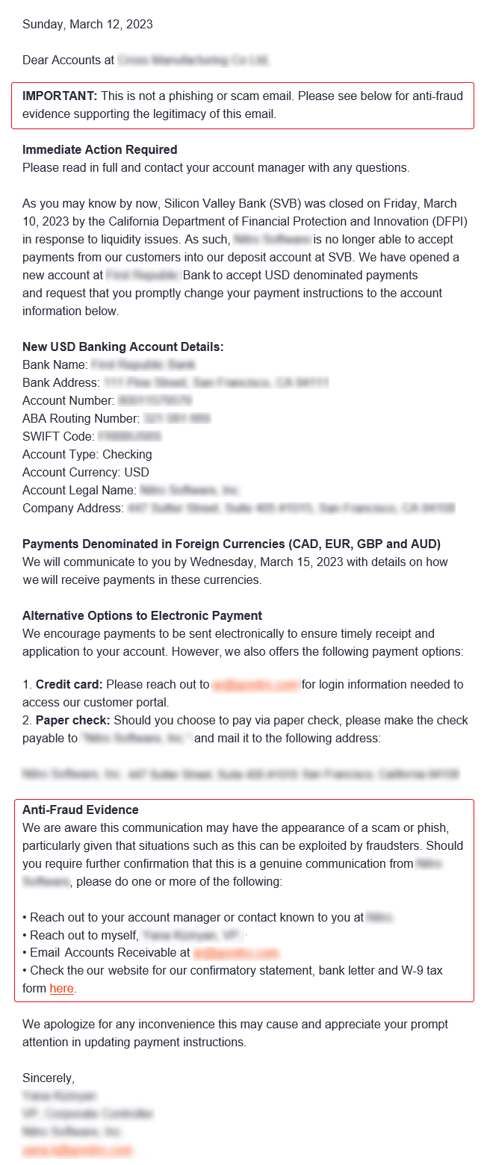
This is why IRONSCALES uses AI and Human Insights to combat advanced phishing threats. This approach catches emerging attack variants and helps train AI and machine learning models with new examples of what good and bad looks like.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)







