Table of Contents
In July 2020, threat actors preyed on pandemic-driven financial distress by launching a series of stimulus-related phishing attacks. As talks continue in DC to expand the stimulus, IRONSCALES researchers have identified a renewed and forceful strain of this attack. This attack is targeting the employees of U.S.-based companies with malicious links by using social engineering techniques, but is global in scale. It follows a series of attacks first seen in the round of stimulus payments last Spring, with the clear intent being to harvest credentials for account takeover, fraud and other criminal activity.
The timing is especially ostentatious as the U.S. federal government passed its second round of individual stimulus payments on December 27, 2020, with more stimulus expected from the Biden Administration. Both the Better Business Bureau and the Internal Revenue Service have already warned to expect scams related to this round of stimulus payments - but that has mainly focused on text/sms phishing. And we know the first round of stimulus payments led to similar prying attempts to dupe consumers into entering sensitive financial information.
To date, at least 88 IRONSCALES customers have been targeted by this attack, with the email promising stimulus money in the form of government backed grants.
Stimulus Phishing Attack Details
This phishing attack can bypass secure email gateways (SEGs) and DMARC because it is being conducted from non-spoofed sender addresses, enabling the message to defeat the sender policy framework (SPF) authentication protocol.
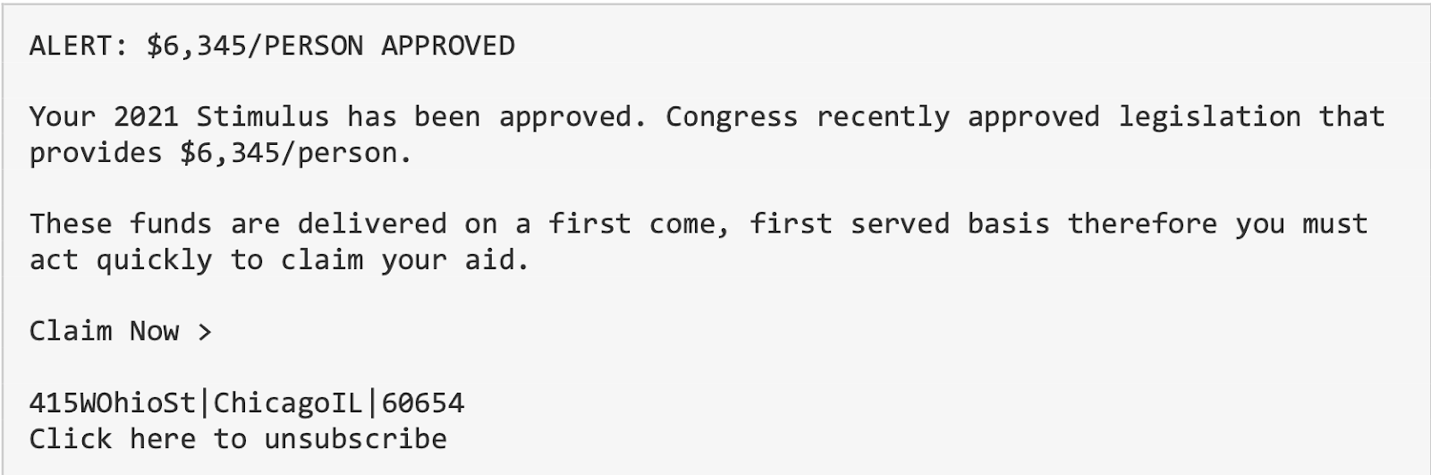 There is a twofold strategy behind this attack, making it of particular consequence. First, the email uses social engineering attack techniques to create an emotional appeal to the recipient. By combining economic uncertainty caused by COVID-19 with the recent stimulus legislation, the user is enticed to respond and secure “approved” 2021 stimulus. In addition, there is a sense of urgency that is a hallmark of phishing emails, asking the user to “act quickly to claim your aid.”
There is a twofold strategy behind this attack, making it of particular consequence. First, the email uses social engineering attack techniques to create an emotional appeal to the recipient. By combining economic uncertainty caused by COVID-19 with the recent stimulus legislation, the user is enticed to respond and secure “approved” 2021 stimulus. In addition, there is a sense of urgency that is a hallmark of phishing emails, asking the user to “act quickly to claim your aid.”
Of note, the “Claim Now” and “unsubscribe” links contain a domain that is known to be suspicious. Additionally, this domain is known to forward users to other malicious websites.
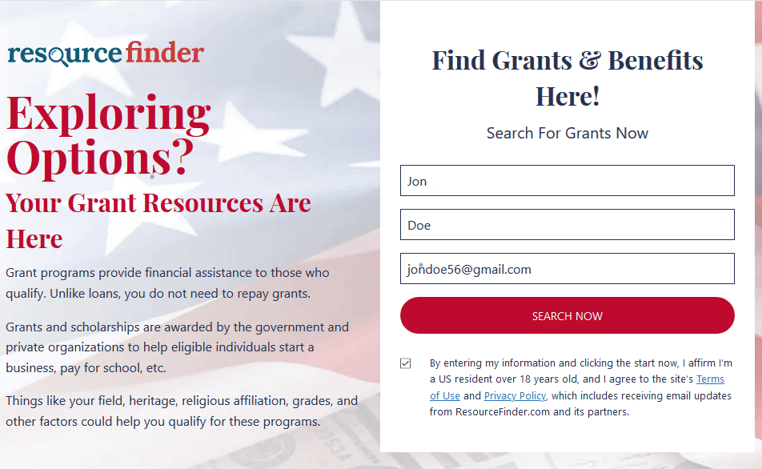


Second, once engaged, the recipient is directed to a chain of sophisticated spam-like websites where the user inputs an array of personal information. While the email and some of the login pages would look suspicious to those with phishing awareness training, far too many people will recognize it as legitimate because it bypassed at least one email security filter.
The landing pages also utilizes deceiving visuals and text (the U.S. flag, “your grant resources are here”) to coerce users into entering personal information. Further, users are directed to a number of other “grant” and “financial assistance” pages that ask users to fill out surveys containing questions about zip codes, age, income and more. Although these “phishy” links do not contain malware, the information inputted can be used in future attacks and the intent is clearly malicious. Further, we can surmise that if users continued to follow the direction of these links, there is a strong possibility that they might eventually run into a malware attack.
Identifying and Remediating Advanced Phishing Threats
Again, it is notable that the “phishy” pages go above and beyond most to appear legitimate. The details are down pat, with a strong, photoshopped image in the back of the U.S. flag and American cash, a logo that leverages a magnifying glass and even a terms of use and privacy policy checkbox. Clearly, the cybercriminals are savvy enough to understand that the combination of stimulus payments with the realistic-looking landing page is enough to make this a credible threat.
IRONSCALES virtual SOC analyst Themis was able to remediate all instances of this attack using artificial intelligence and natural language understanding, the danger lies if the attack was more widespread to non-IRONSCALES customers that don’t have the same level of mitigation.
With the 2020 Verizon Data Breach Investigations Report showing that ~65% of all breaches now result from hacking and/or email phishing attacks, it’s imperative for businesses to educate employees on pressing threats and have the right technology to protect against today’s hacking and phishing challenges.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)









.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)





