Table of Contents
In the current era of remote work, organizations are grappling with a myriad of cybersecurity challenges. In our recent commissioned report by Enterprise Strategy Group (ESG), Tackling SaaS Communication and Collaboration Security Challenges: Trends and Strategies for Enterprises, which reveals the pressing issue of an increasingly distributed IT environment, where the massive adoption of collaboration and communication tools is inadvertently creating security gaps—gaps that cybercriminals are eager to exploit!
Shadow IT
One striking aspect that the report brings into focus is the issue of shadow IT—the unsanctioned use of software and applications in an organization. Now, when you think of an office, you probably imagine a physical space where workers commute daily. But in recent years, and even more so during the pandemic, the office space has shifted from the corner block to the cloud. Teammates now collaborate and communicate via multiple digital platforms, and many of them aren’t IT-approved, hence the term "Shadow IT.”
In a way, we can see why employees veer towards these applications. They're easy to adopt, offer versatile functionalities, and aid productivity in this work-from-home era…the fact that many of them offer “freemium” options encourages this trend. The problem, however, is that these tools and their low barrier to entry can—unknowingly to employees—open doors for cybercriminals. Unsanctioned tool adoption often means that the tools and services won’t get the normal scrutiny and security assessment from a company’s IT security team. This makes such applications highly attractive vectors for malicious attacks.
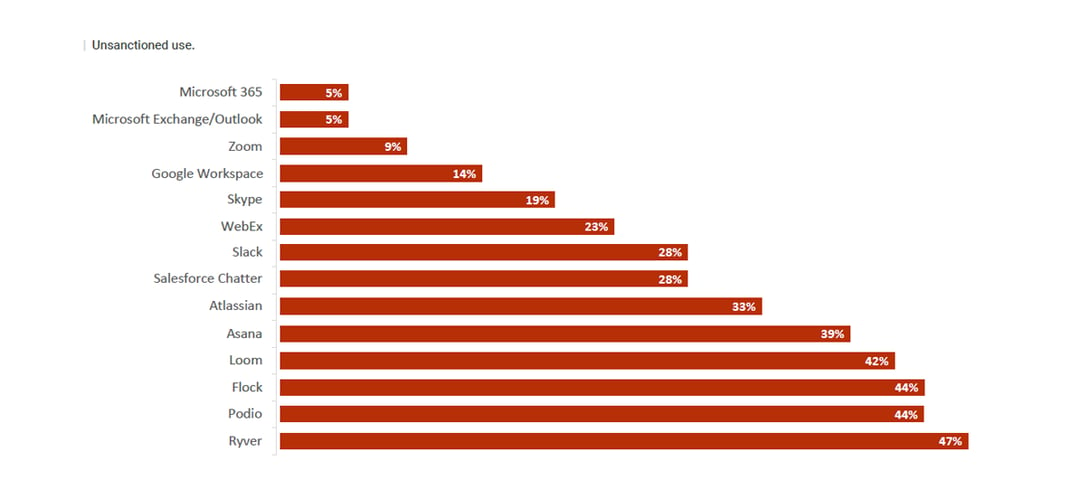
So…how exactly is Shadow IT exacerbating security risks? Let's take a simple example.
A team member decides to use a non-sanctioned file-sharing tool to share a project update. As the tool isn't under the umbrella of the organization's security system, it's an easy target for threat actors. And since “sharing” is uber-germane to a file-sharing tool, it must provide the ability to send notifications to team members about “new shares” and other activities and updates. Attackers can easily send phishing emails that look just like one of these notifications, and they are near impossible to discern with the untrained eye (or even a trained eye in many cases).
In most cases, links in these phishing emails will point to a spoofed log-in page that looks identical to the genuine log-in page. And since the application was adopted without the assistance (or blessings) of the IT security team, the users won’t be able to use company secure single sign-on (SSO) services or company provided MFA/2FA services. Even if these services are used, most of the spoofed log-in pages attackers use today have the ability to intercept or capture authentication codes, and if that happens, the employees are still operating without the air-cover of their security teams.
An Interesting Paradox
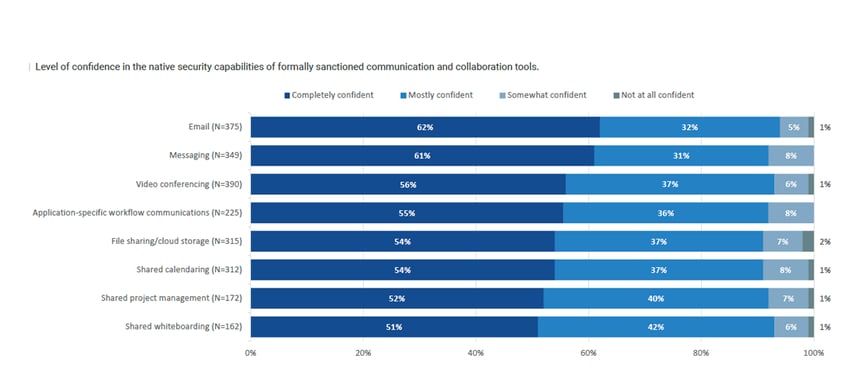
The report also highlights an interesting paradox. When asked how confident they were in the native security capabilities of formally sanctioned communication tools, respondents indicated that they were Mostly to Completely Confident.
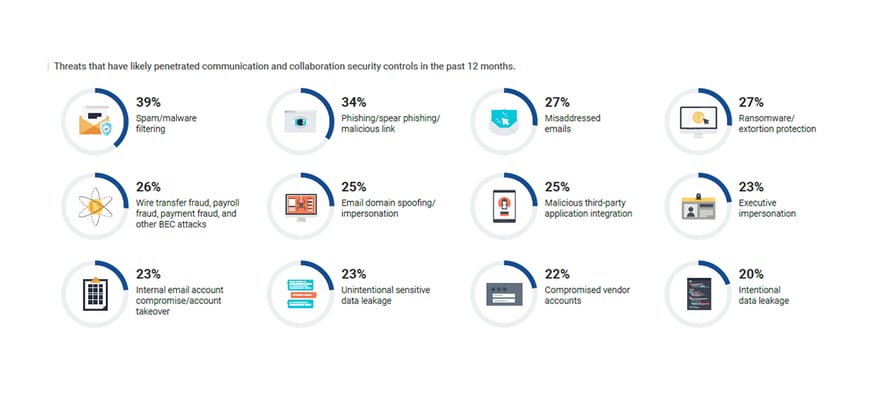
However, when asked how likely it is that 12 common types of malware and phishing tactics have penetrated the same native security controls, respondents indicated that all of them likely been successful at least once in the previous 12 months.
Interestingly, our research shows a positive trend. Organizations recognize the urgency to tackle these security gaps. Most are prioritizing the strengthening of security across all communication channels, with 76% expecting an increase in spending to strengthen multi-channel controls (Page 17: “A High-risk Threat Vector and High Priority for Most”).
Next Up: Tackling the Security Challenges in the Age of Digital Collaboration (Part 2)
While it's promising that organizations are now more aware and willing to act, navigating this new security landscape will require a more holistic and proactive approach. This should involve IT and security teams working together to create and enforce consistent security controls and policies across all enterprise communication channels.
In Part 2, we’ll explore operating models at play that are creating additional security gaps across disparate collaboration and communication channels.
Interested in delving deeper into this report? Download the full version download here.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)









