Table of Contents
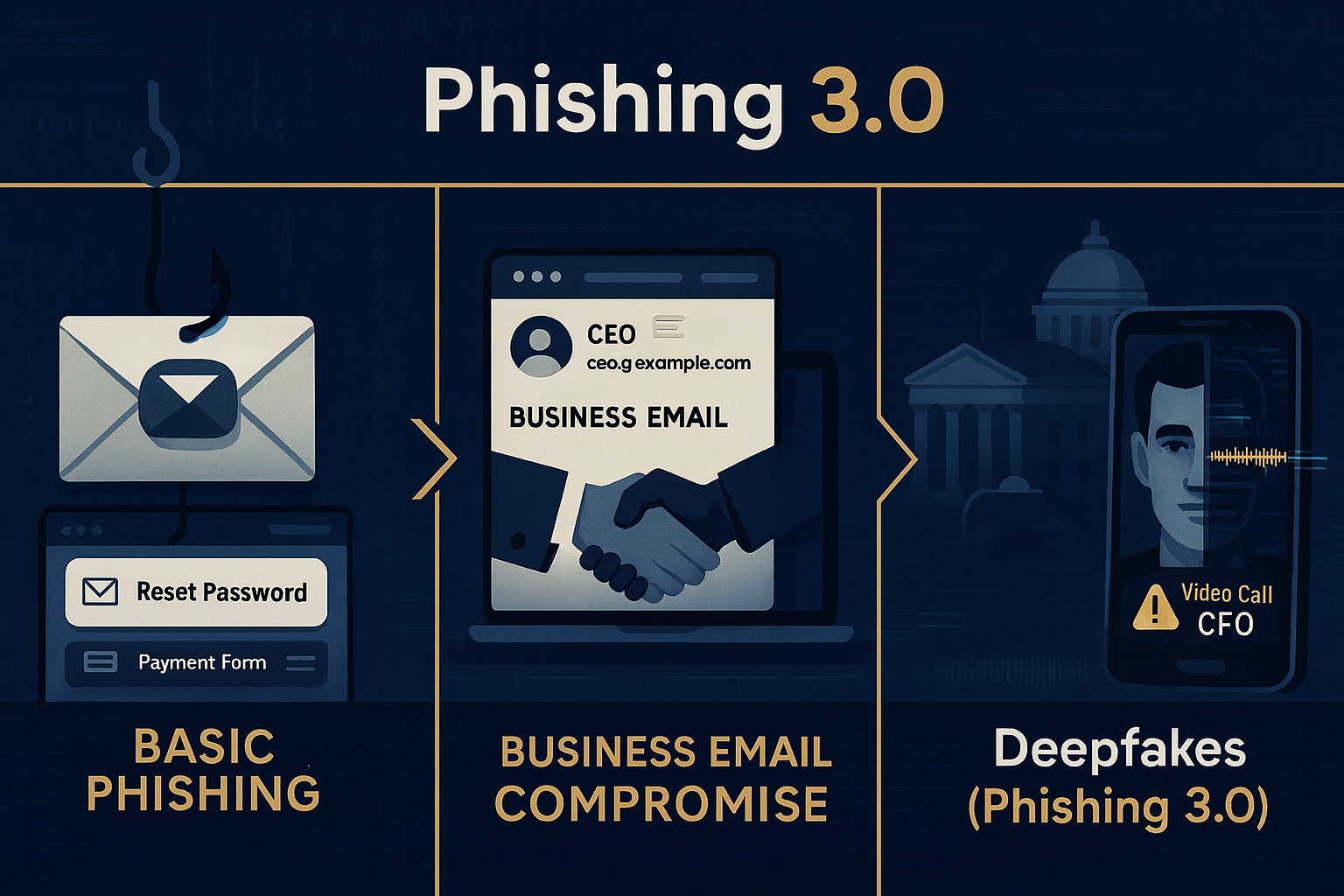
Social engineering has always been one of the most effective weapons for cybercriminals. They exploit trust, manipulating people into giving up sensitive information or taking actions they shouldn’t. But now, with deepfake technology, these attacks have become even more dangerous and far more convincing. As deepfakes get more realistic, the line between truth and deception blurs, making it harder than ever to spot the threat.
Deepfakes Are More Than Just Video
Many people think of deepfakes solely as videos, but they actually encompass various forms of media. Besides video, they also include images and audio (both live and recorded). These are generated using artificial intelligence to accurately replicate someone’s face, voice, or behavior. Their danger lies in how authentic they can appear or sound.
While deepfakes started in entertainment, they’ve quickly become tools for cybercriminals who want to trick businesses.
Here’s where it becomes alarming for businesses...deepfakes are now enhancing social engineering attacks by enabling attackers to mimic key individuals with frightening precision. Suddenly, that “CEO” requesting an urgent transfer via video appears much more convincing.How Deepfakes Take Social Engineering to a New Level
Social engineering works by tricking people into making decisions they shouldn’t, usually by pretending to be someone else. Deepfakes amplify this, introducing a level of authenticity that traditional attacks have always lacked. Let me break it down for you:
-
CEO Fraud Gets a Dangerous Makeover — We’ve all heard of CEO fraud, where attackers send emails that appear to be from the boss, asking for wire transfers or sensitive information. Now imagine getting a video message or a phone call from your CEO, complete with their voice and mannerisms, asking you to authorize a payment. It’s no longer just a cleverly worded email—it’s something far more believable, and harder to detect.
-
Voice Phishing (Vishing) Becomes Almost Undetectable —Voice phishing used to rely on scammers sounding just “official enough” to convince someone over the phone to share private data. Now, deepfake audio can replicate someone’s voice so perfectly, it’s almost impossible to tell the difference. If an employee gets a call from a “trusted colleague” asking for access to sensitive systems, how likely are they to think twice?
-
Fake Video Calls — As video conferencing becomes the norm, deepfakes can now target these meetings. Imagine joining a video call with your supervisor, only to realize later it wasn’t really them. Deepfake videos can simulate live interactions, making these impersonations disturbingly real and harder to spot on the fly.
Real-World Deepfake Attacks We’ve Seen
Deepfake scams are no longer hypothetical. In a high-profile case, a finance worker at Arup, a global design and engineering firm, was tricked into transferring $25 million after an elaborate video call featuring deepfake versions of his colleagues, including the CFO. Initially suspicious, the employee set aside his doubts because other familiar faces on the call also looked and sounded genuine. This incident underscores the increasing sophistication of deepfake fraud and highlights the urgent need for rigorous verification processes.
What We Can Do to Defend Against Deepfake Attacks
Deepfakes are challenging because they’re so convincing, but we’re not powerless. Here’s what we can do:
-
Verify Through Multiple Channels — Even if a request looks or sounds legitimate, always confirm it through a second method. If you get a video message asking for a financial transfer, follow up with a secure message or make a phone call to verify. It might feel redundant, but with high-stakes transactions, it’s necessary.
-
Educate Your Team — I can’t emphasize this enough—training is key. Your employees need to know about deepfakes and how to spot them. Include it in your social engineering awareness training, so people start questioning unusual requests, especially those involving money or sensitive information.
-
Use Code Words — Establish unique, regularly updated code words for verifying sensitive requests. These codes should be known only to relevant parties and used during high-risk communications, like financial transactions. Make sure employees are trained on when and how to use them, and periodically practice this protocol to ensure everyone can implement it effectively in real-time.
-
Monitor Public Channels for Misinformation — We’ve seen deepfakes being used for disinformation, and it’s only going to get worse. Make sure someone in your organization is actively monitoring social media and public forums for fake content that could harm your brand. Having a crisis communication plan ready to go will help you get ahead of any false narratives.
The Future of Deepfakes and Social Engineering
Deepfakes are redefining how social engineering attacks work. They’re not just phishing emails or phone scams anymore—these attacks are becoming more personal, more realistic, and harder to stop. If we stick to traditional defenses, we’re going to struggle. But if we stay informed, invest in the right tools, and put strong verification processes in place, we can protect ourselves from this evolving threat.
The key is staying ahead of the curve. Deepfakes aren’t going away, and they’re only getting more convincing. Now’s the time to act.
IRONSCALES Fall 2024 Report - Deepfakes
Deepfakes: Is Your Organization Ready for the Next Cybersecurity Threat?
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)