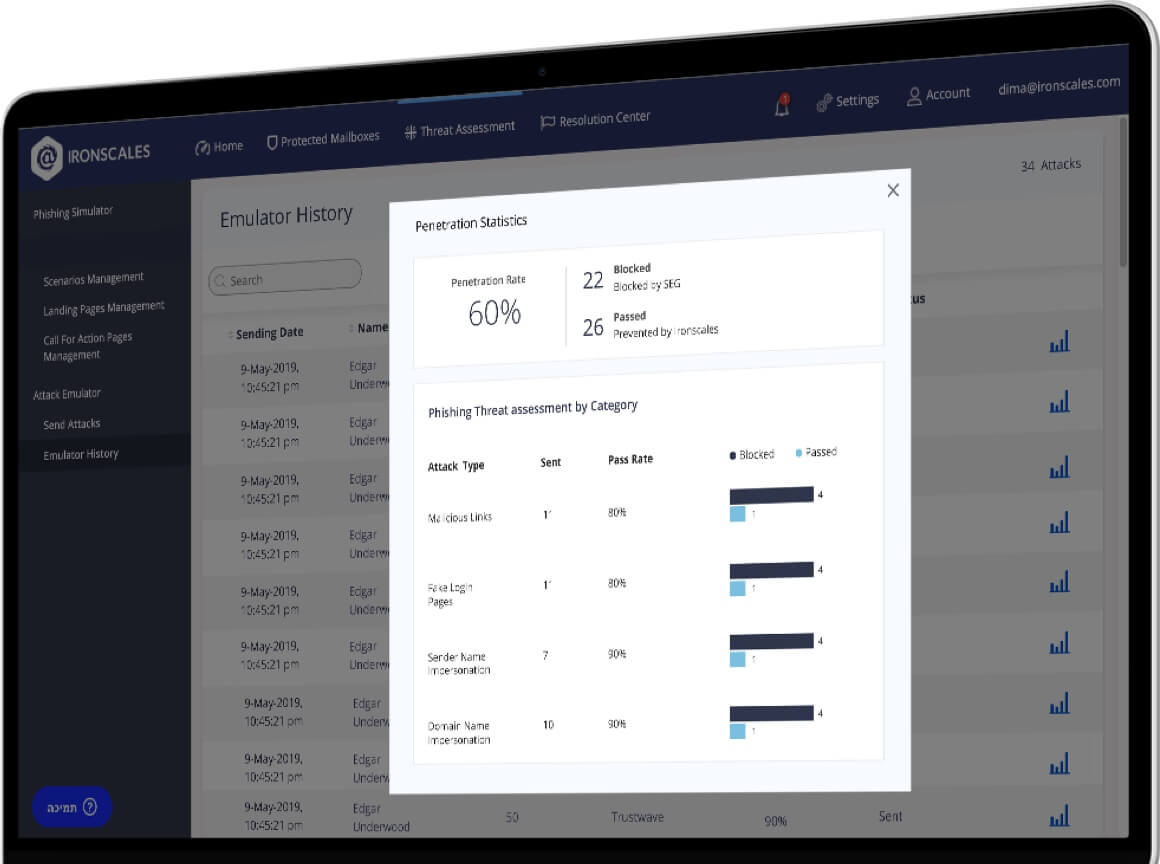
Table of Contents
We recently wrote about the most prominent phishing attacks so far in 2017. Such attacks have led to record-breaking ransomware payments of more than $100 million; impersonations of CEOs at major Fortune 500 organizations and breaches of critical infrastructure, including the power grids and water facilities of sovereign nations. And that’s just the tip of the phishing iceberg.
According to Cyberscoop analysis of the Anti-Phishing Working Group’s 2016 Global Phishing Survey, hackers are eating up internet addresses from the domain name registration to use in phishing attacks. Similarly, according to eWeek, the FBI recently revealed an astounding $1.33 billion in losses stemming from Business Email Compromise (BEC), a type of phishing attack that tricks companies into paying “fraudulent invoices.” These troubling statistics follow the patterns identified in our recent data report, which found that 70 percent of attacks targeted 10 inboxes or less, and one-third of malicious messages targeted only one inbox.
At the same time, financial investment in phishing awareness and training is exploding. Cybersecurity Ventures estimates the “global spending on security awareness training for employees predicted to reach $10 billion by 2027.” Yet unfortunately, the risks of cyberattacks proliferating from a phishing event is as high as it has ever been.
The Painstakingly Long Forensics Process for Phishing Emails
We’ve said it many times before: to mitigate and remediate phishing attacks, time is of the essence. But while a phishing-informed workforce may be able to identify suspicious emails more frequently, the forensics process often stalls significant from there, especially for companies that rely on SOC teams for analysis and remediation. In fact, the average time for phishing attack identification to remediation is an astounding 146 days, according to FireEye.
So, what’s taking SOC and security teams so long to confirm and remediate a phishing attack or determine it to be a false positive? We have also written before about the unprecedented burdens facing SOC teams, but even so, the process remains infuriatingly slow, especially for those most at risk of a sustained breach.
To understand why remediation takes so long, you first have to understand all of the intricacies that the forensic phase consists of. This includes:
- The email must be carefully forwarded to the SOC team in its full and original state.
- The SOC team typically delivers specific instructions to the employee on how to accomplish this task without adding new risks.
- Examine attachments by uploading to a third-party examination site.
- The attachment is then run in a Sandbox
- Results may take a long time!
- Examine the Header
- Identifying return-path by running a quick ‘whois’ on the offending siteSpecifically, security teams look for the validity of sender name, sender address, links, attachments, sense of urgency and typos in body and subject. This process includes:
- Authenticate user, if possible
- Analyze routing information, including the IP address of both the sender and relaying mail server
- Conduct a SPF check
- Conduct a DKIM check
- Conduct a DMARC check
- Identifying return-path by running a quick ‘whois’ on the offending siteSpecifically, security teams look for the validity of sender name, sender address, links, attachments, sense of urgency and typos in body and subject. This process includes:
- If phishing is suspected, ask the IT team to search all mailboxes for this mail and by subject, sender, and attachment name (if any). This can be done using New-Compliance Search and Start. ComplianceSearchAction features on Exchange 2016 and Office 365.
- Note that this is a multistep process that can take time to uncover results
With so many time-consuming steps in the phishing identification process, it’s no wonder that SOC teams struggle to analyze each and every reported suspicious email in a timely manner.
Machine Learning & Automation Essential to Phishing Forensics
Email phishing is not going to get any better; in fact, it’s likely going to get worse. This reality exists as analysts’ project 3.5 million open cybersecurity jobs by 2021. Thus, cybersecurity teams need machine learning and automation more than ever to help identify suspicious emails and expedite the forensics process overall.
IronTraps, our automatic phishing incident response technology, performs the only fully automated forensics of reported or detected suspicious emails. This includes:
- URL/Link Scanning – Using Virus Total multi AV Engines and Google Safe browsing to detect against known malicious links such as malware/social engineering.
- Attachments Scanning – All detected or reported phishing emails are scanned automatically for malicious attachments using Virus Totals’ Multi AV Engines and Check Points’ SandBlast and immediately quarantined if found to contain anything malicious.
- Affected Mailboxes Real -Time Report – Provides a comprehensive forensic analysis and unified view of the affected mailboxes, allowing security teams to review the status of the potential phishing attack and intervene if necessary with a single mouse click.
- Spam Analysis – The system clusters similar reported spam emails as one single entry so that users and security members can tag the entries as spam, removing the amount of “noise” from the dashboard reports. This enables teams to spend more time on legitimate problems.
- Email Clustering – Using patented algorithms to cluster and find similarities in phishing emails to create a repository of patterns, IronTraps prevents the same or similar types of attacks from infiltrating IRONSCALES’ detection.
This automated process takes only a matter of seconds, and it has proven to accelerate the time from identification to remediation from weeks to minutes. In the next blog post, we’ll address how IRONSCALES automation and machine learning impacts the remediation and prevention phases of phishing emails. In the meantime, click here to learn more about and get started with IronTraps.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)